Ransomware Prevention
Work with Certified Security Experts to Protect your Organization from Evolving Cyber Threats
Ransomware Prevention
Ransomware is dangerous for organizations because it can disrupt operations, incur substantial financial costs, damage reputation, lead to legal consequences, and pose significant cybersecurity challenges. Organizations need to adopt a proactive approach to cybersecurity to minimize the risks associated with ransomware attacks.
To mitigate the risk of falling victim to ransomware, organizations and individuals need to adopt a multi-faceted approach. This includes regularly updating software and security patches, employing robust antivirus and anti-malware solutions, conducting employee training on phishing awareness, implementing strong password policies, and regularly backing up critical data to offline or secure cloud storage. A proactive stance on cybersecurity is key to avoiding the devastating consequences of ransomware attacks.
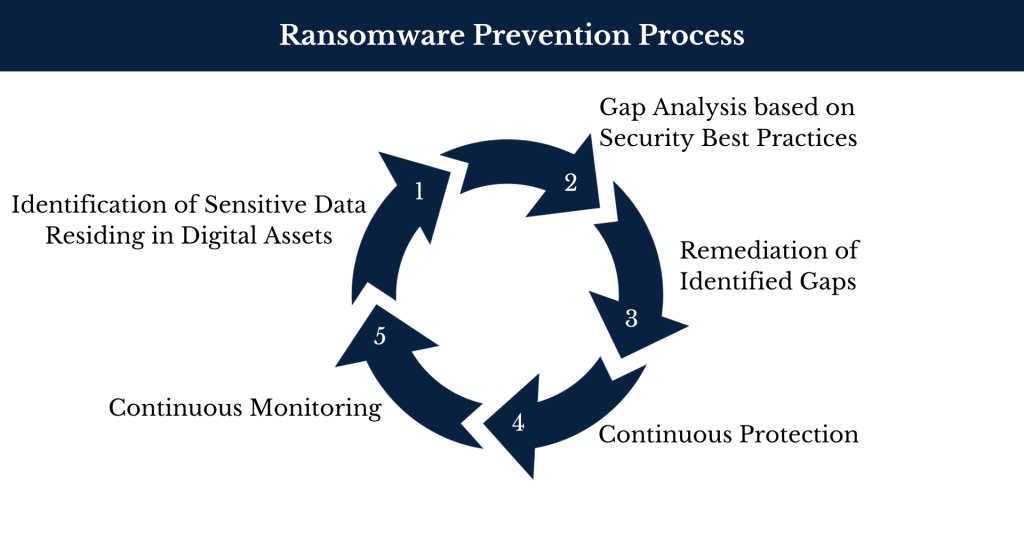
Ransomware Prevention Process
Our certified security experts have over a decade of experience working with leading security vendors. Our team uses a comprehensive approach to implement security technology and protect your digital assets and prevent cyber attacks, including ransomware.
1. Identification of Sensitive Data Residing in Digital Assets: This step involves pinpointing valuable and sensitive data stored within digital assets, such as personal information or critical business data.
2. Gap Analysis: A thorough evaluation is performed to assess the existing security measures against established best practices, identifying vulnerabilities or weaknesses in the system.
3. Remediation of Identified Gaps: After gaps are identified, appropriate actions are taken to address these vulnerabilities, which may include software updates, security patches, implementing new security tech and making policy adjustments.
4. Continuous Protection: Ongoing security controls and measures are implemented to maintain a robust defense system, ensuring that potential threats are consistently mitigated.
5. Continuous Monitoring: Real-time monitoring tools are employed to actively detect and respond to security issues as they arise, allowing for swift action to prevent or limit damage from ransomware or other threats. Monitoring leads back to a modified version of step 1 in this circular process as unprotected sensitive data is identified.
Explore Blogs, Webinars and other Resources
Trusted by Reputed Companies
What Our Clients Say
We used databrackets (formerly EHR 2.0) in our small medical practice for our risk analysis assessment to be in compliance with meaningful use. Their response was fast, the final report is detailed but simple and easy to follow. They were always available to answer our questions.
E. Compres
Pulmonary and Sleep Center of the Valley
I never miss the opportunity to learn something new …that’s why I am always registering to all free seminars offered on the web. databrackets (formerly EHR 2.0) happened to be the friendliest, comprehensive and up-to- date source of HIPAA Privacy and Security updates.
Alexandra V.
Community Healthcare Network
Today’s presentation was great! Thank you for sending the slides. My only feedback is that it would be fabulous to have the slides ahead of time so I could print them and take notes on the slides.Thanks for your time and knowledge today!
T.B., PM
Community Health Network
Particularly interesting was the flow chart on Administrative Simplification. I utilize all of the Security subcategories you list under the Security tile and appreciate knowing that I am hitting all of the relevant topics during my employee training.
Jessica B.
JD, CHC
I have re-worked our original risk assessment….We are using databrackets' (formerly EHR 2.0) Meaningful Use Security Risk Analysis Toolkit and it meets our needs. It was easy to use and I believe that it very beneficial to our meeting meaningful use.
Bill Curtis
Neurosurgical Associates Of Texarkana, TX
Information (webinars) presented by databrackets (formerly EHR 2.0) highlights some of today’s most demanding healthcare topics. The webinars help to direct those operating in today’s rapidly changing environment in the right direction.
Candace M.
Privacy and Security Officer, Springhill Medical Center
Our Growing List of Credentials
0
+
Assessments
0
+
Clients
0
+
Assessment Libraries
0
+
Years of Experience
0
+
External audits handled