For defense contractors working with the Department of Defense (DoD), managing Controlled Unclassified Information (CUI) has become a critical compliance challenge. As CMMC Consultants we have guided organizations to identify and manage CUI for CMMC and implement controls. We have witnessed firsthand the confusion, frustration, and sometimes panic that ensues when contractors first attempt to understand their CUI obligations.
This comprehensive blog aims to demystify CUI management within the context of Cybersecurity Maturity Model Certification (CMMC), offering practical solutions to common challenges. You can connect with our certified experts to get customized solutions whether you’re still trying to identify what constitutes CUI in your environment or looking to refine your existing protection measures. Our team has worked with NIST 800-171 controls and is well-versed with and certified to handle CMMC Compliance.
What is CUI?
Controlled Unclassified Information represents the government’s solution to standardizing the protection of sensitive but unclassified information. According to 32 CFR Part 2002, CUI is “information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.”
Put simply, CUI is information that requires protection from unauthorized disclosure but does not meet the threshold for classification under Executive Order 13526.
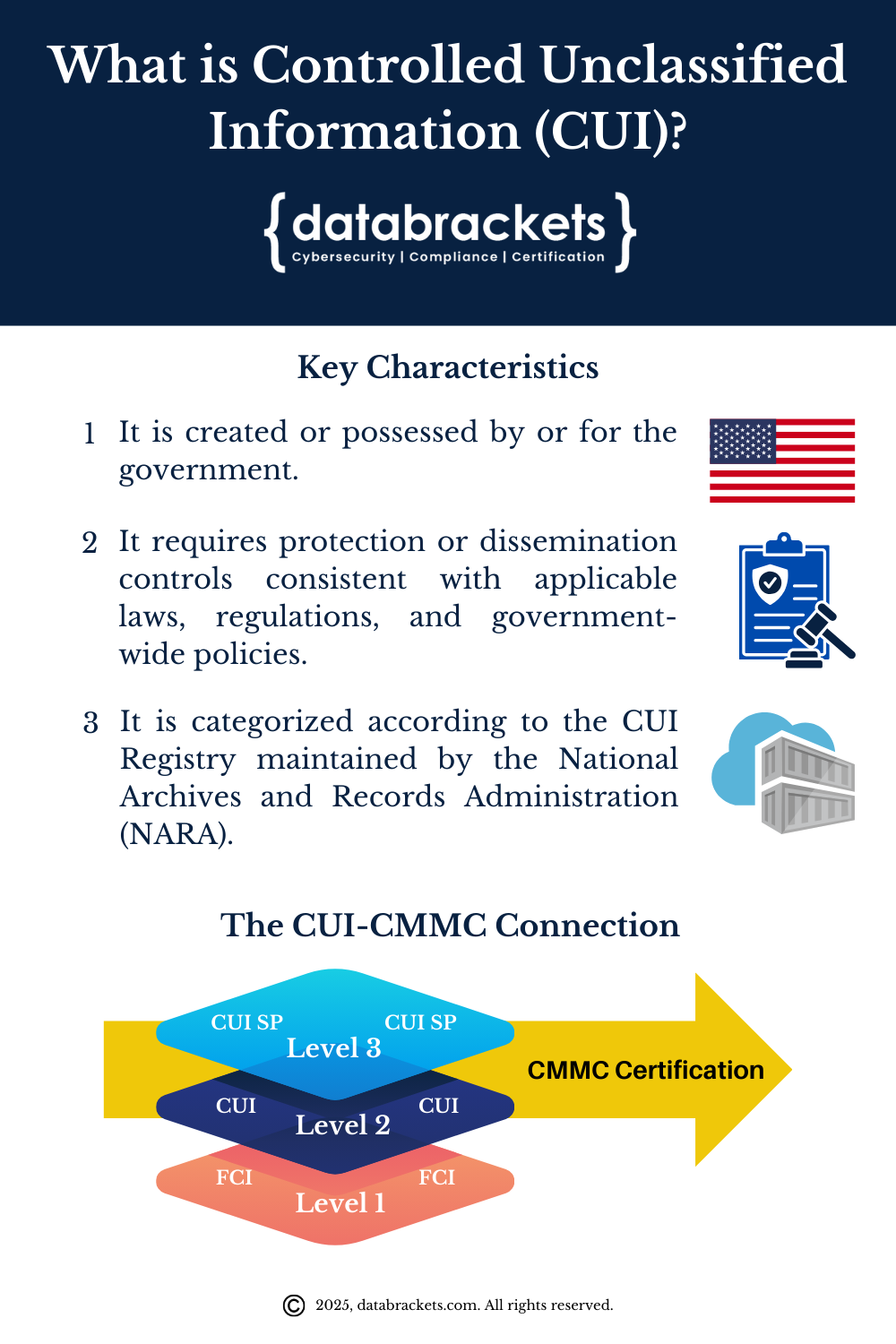
Key characteristics of CUI include:
It’s created or possessed by or for the government.
It requires protection or dissemination controls consistent with applicable laws, regulations, and government-wide policies.
It is categorized according to the CUI Registry maintained by the National Archives and Records Administration (NARA)
CUI SP refers to the defined set of security practices required to protect Controlled Unclassified Information under CMMC Level 3. It goes beyond basic cyber hygiene, demanding a mature, risk-based approach to access control, incident response, and data protection aligned with federal expectations. The specific security practices for CMMC Level 3 compliance exceed the controls required for CUI protection under CMMC Level 2 compliance.
The CUI – CMMC Connection
CMMC 2.0 requirements are directly tied to the protection of CUI. The framework establishes three levels of cybersecurity maturity:
Level 1: Focuses on the protection of Federal Contract Information (FCI)
Level 2: Encompasses the protection of CUI and requires implementation of 110 security controls from NIST SP 800-171
Level 3: Provides enhanced protection for CUI in critical programs and technologies
Most defense contractors handling CUI will need to achieve at least CMMC Level 2 certification, which represents the bulk of compliance effort across the DIB.
Common CUI Pain Points and Practical Solutions
Pain Point 1: Identifying CUI in Your Environment
Many contractors struggle with the fundamental question: “What information in our possession actually qualifies as CUI?”
Solution: Implement a structured identification process:
Review contract language carefully: Look for references to CUI, NIST SP 800-171, controlled technical information, or similar terms in your contracts and RFPs
Consult the CUI Registry: Visit the NARA CUI Registry to understand the 20 categories and 125+ subcategories of CUI.
Conduct data flow mapping: Document how potentially sensitive information moves through your organization.
Create an inventory: Maintain a detailed record of all identified information that can be classified under this title, including its category, source, format, and location.
Establish a review board: Form a cross-functional team to make determinations about ambiguous information.
Pain Point 2: Marking and Handling Procedures
Once it is identified, contractors often struggle with appropriate marking, handling, and dissemination procedures.
Solution: Develop comprehensive handling policies:
Implement proper marking: Apply standardized markings to documents and materials containing CUI according to 32 CFR Part 2002
Create handling procedures: Establish clear guidelines for how it should be handled, processed, transmitted, and destroyed.
Train all personnel: Ensure everyone who might come into contact with such information understands proper handling procedures.
Document authorized users: Maintain an up-to-date list of individuals authorized to access specific categories of CUI
Implement need-to-know principles: Restrict information access to only those who require it to perform their job functions.
Pain Point 3: CUI in Cloud Environments
As organizations increasingly migrate to cloud services, protecting information in these environments presents unique challenges.
Solution: Take a deliberate approach to cloud usage:
Verify FedRAMP Moderate (or equivalent) compliance: Ensure your cloud service provider meets this minimum standard.
Implement customer-responsible controls: Remember that many NIST 800-171 controls remain your responsibility even in cloud environments.
Create data classification policies: Clearly define what types of data can be stored where
Use encryption properly: Implement encryption both in transit and at rest for all sensitive information.
Monitor cloud security posture: Continuously assess your cloud environment for security gaps.
Pain Point 4: Managing CUI with External Parties
Contractors often struggle with how to handle sensitive information when working with subcontractors, vendors, and other external parties.
Solution: Implement robust supply chain management for sensitive information:
Flow down requirements: Ensure all CMMC and CUI protection requirements are properly flowed down to subcontractors
Assess supplier capabilities: Evaluate whether external parties have the necessary safeguards to protect it
Limit sharing: Only share information with external parties when absolutely necessary
Use secure transmission methods: Implement encrypted email or secure file-sharing solutions for external CUI sharing
Document all exchange of information: Maintain records of which type of sensitive information was shared, with whom, when, and for what purpose
Technical Implementation of CUI Protection
1. Creating CUI Enclaves
For many organizations, segregating CUI into a well-defined boundary or “enclave” represents the most practical approach to compliance. Key considerations for enclaves include:
Boundary definition: Clearly define what systems, networks, and data repositories are part of your environment
Access controls: Implement strong authentication and authorization for the enclave
Monitoring and logging: Ensure comprehensive visibility into activities within the CUI boundary
Data transfer controls: Establish secure methods for moving information in and out of the enclave
Documentation: Maintain detailed network diagrams and system security plans for this environment
2. Implementing Multi-Factor Authentication
NIST SP 800-171 requirement 3.5.3 mandates multi-factor authentication (MFA) for local and network access to systems containing CUI. Practical implementation approaches include:
Software authenticators: Applications like Microsoft Authenticator or Google Authenticator
SMS-based solutions: While less secure, can be a starting point (though not recommended for high-sensitivity environments)
Biometric authentication: Fingerprint or facial recognition paired with another factor
3. Encryption Solutions
Proper encryption is fundamental to CUI protection, especially for requirement 3.13.11 (encrypt CUI at rest). It needs to be FIPS validated.
Effective encryption strategies include:
Full disk encryption: BitLocker (Windows) or FileVault (Mac) for endpoint protection
File-level encryption: For more granular protection of specific documents
Database encryption: For structured CUI stored in databases
Email encryption: Solutions like Microsoft Information Protection for protecting sensitive information in communications
Encrypted backups: Ensuring backup copies of CUI remain protected
Developing a CUI Program
A mature CUI management approach requires a structured program with clear governance.
Key program elements include:
CUI policy: A formal document establishing CUI management requirements
CUI procedures: Step-by-step instructions for handling CUI
Designated CUI Program Manager: An individual responsible for program oversight
Training program: Regular education for all personnel who handle CUI
Compliance monitoring: Ongoing assessment of adherence to CUI requirements
Incident response procedures: Specific protocols for potential CUI breaches
Integrating CUI Management with Existing Processes
Rather than creating entirely new workflows, successful organizations integrate CUI protection into existing business processes.
Integration opportunities include:
Contract review process: Add CUI identification steps to contract analysis
Information lifecycle management: Incorporate CUI considerations into data handling procedures
Employee onboarding/offboarding: Include CUI training in onboarding and CUI access termination in offboarding
Vendor management: Add CUI handling capabilities to vendor assessment criteria
Risk management: Incorporate CUI-related risks into your overall risk management framework
Integrating CUI Management with Existing Processes
Rather than creating entirely new workflows, successful organizations integrate CUI protection into existing business processes.
Integration opportunities include:
Contract review process: Add CUI identification steps to contract analysis
Information lifecycle management: Incorporate CUI considerations into data handling procedures
Employee onboarding/offboarding: Include CUI training in onboarding and CUI access termination in offboarding
Vendor management: Add CUI handling capabilities to vendor assessment criteria
Risk management: Incorporate CUI-related risks into your overall risk management framework
Preparing for your CMMC Assessment
A) Gap Assessment and Remediation
Before pursuing formal CMMC certification, conducting a thorough gap assessment is essential.
Recommended approach:
Perform initial self-assessment: Use the DoD Assessment Methodology to establish a baseline
Conduct detailed practice reviews: Examine each NIST 800-171 requirement in depth
Develop a detailed Plan of Actions & Milestones (POA&M): Document all gaps with remediation plans
Implement high-priority controls first: Focus on fundamental practices with significant security impact
Document evidence of implementation: Maintain records that demonstrate compliance
B) Documentation Preparation
Proper documentation is crucial for successful CMMC assessment. Essential documentation includes:
System Security Plan (SSP): A comprehensive document describing your cybersecurity implementation
Configuration management documentation: Records of system hardening and configuration standards
CUI handling procedures: Detailed protocols for managing CUI throughout its lifecycle
Incident response plan: Procedures for addressing cybersecurity incidents
Training records: Evidence of security awareness and specialized CUI training
Beyond CMMC Compliance
While achieving CMMC certification is necessary for defense contractors, the most successful organizations recognize that effective CUI protection offers benefits beyond compliance.
Robust CUI management:
Enhances your competitive position for government contracts
Protects your own intellectual property with similar sensitivity
Demonstrates commitment to national security
Builds trust with government clients and prime contractors
Creates organizational discipline that improves overall security posture
By adopting a structured, programmatic approach to CUI management, you not only satisfy regulatory requirements but also strengthen your organization’s security foundation and competitive position in the defense industrial base.
As you continue your CMMC journey, remember that proper CUI protection isn’t just about checking compliance boxes—it’s about contributing to national security while building a more resilient organization.
Additional Resources:
Key Takeaways
Controlled Unclassified Information is the primary driver of CMMC scope, because certification requirements apply only to systems, processes, and environments that store, process, or transmit CUI in support of Department of Defense contracts.
CUI is defined by the government, not by individual organizations, which means contractors must rely on official markings, contract language, and authoritative categories rather than internal judgment when determining whether information qualifies.
Misidentifying or over-generalizing CUI expands compliance obligations unnecessarily, while under-identifying it creates certification risk by leaving regulated data outside documented protections.
Accurate CUI identification requires understanding how information flows through the organization, including where it originates, how it is used, and where it is ultimately stored or shared.
CUI scoping decisions directly shape system boundaries, documentation requirements, and assessment expectations, making early clarity essential for efficient compliance planning.
Not all sensitive or proprietary information is CUI, and conflating internal business data with regulated government data leads to inflated security scope and avoidable operational burden.
Proper CUI handling is inseparable from documentation, because assessors evaluate not only technical protections but also whether CUI locations, flows, and protections are clearly described and consistently maintained.
CUI responsibilities extend beyond internal systems to any external services or partners that interact with the data, requiring deliberate consideration of where CUI leaves organizational control.
Treating CUI identification as a one-time exercise undermines compliance readiness, since changes in contracts, systems, or workflows can alter what data is in scope over time.
Clear, disciplined CUI understanding enables organizations to focus CMMC efforts where they are contractually required, rather than diffusing resources across systems that do not impact certification.
How databrackets can help you with your CMMC Journey
databrackets is an authorized C3PAO and independent consulting organization for CMMC. We offer Certification OR Readiness and Consulting services for CMMC. To avoid a conflict of interest and abide by CMMC’s independence requirements, we do not offer both services to the same client.
We are an ideal partner for either service since we bring over 15 years of proven expertise in helping organizations achieve compliance or certification with the most rigorous cybersecurity and data privacy standards, including ISO 27001, SOC 2, HIPAA, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, and CMMC. We are an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
Schedule a Consultation to work with us as your C3PAO for CMMC Certification or as your Compliance Partner to help you prepare for it.
A. Why Choose databrackets as your C3PAO
1. Proven Multi-Framework Expertise
What makes databrackets particularly valuable is our extensive experience across complementary frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and NIST Cybersecurity Framework. We are also an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
This breadth of knowledge enables our assessment teams to understand how CMMC controls integrate with your existing compliance efforts and identify synergies that strengthen your overall security posture.
2. Technical Environment Proficiency
databrackets’ assessment team of CCAs and CCPs has the specialized technical competence essential for accurate CMMC evaluations. Our experience spans diverse technological environments, from traditional on-premises infrastructures to complex cloud deployments, ensuring we can effectively assess whatever technical landscape your organization operates in.
3. Strategic Timeline Management
With proven capability in managing sophisticated assessments spanning the typical 4–8-week timeframe, databrackets understands how to minimize disruption to your operations while ensuring comprehensive evaluation of all 110 NIST SP 800-171 security controls.
As a authorized C3PAO with extensive cybersecurity and compliance experience, databrackets offers a deep understanding of the CMMC assessment process. This comprehensive expertise enables us to conduct thorough assessments with clear explanations of findings and methodologies, resulting in more insightful evaluations for organizations seeking certification.
To inquire about our C3PAO Services, contact our team at sales@databrackets.com or schedule a free consultation.
B. Why Choose databrackets for Your CMMC Compliance Journey
We specialize in transforming CMMC compliance from a daunting obstacle into a strategic business enabler.
Proven Track Record: Over 15 years supporting organizations across diverse industries with complex compliance requirements
Comprehensive Approach: End-to-end support from initial assessment through ongoing compliance
Industry Recognition: Authorized certifying body for ISO 27001 and 3PAO for FedRAMP
Strategic Partnership: We don’t just help you achieve compliance—we help you leverage it for competitive advantage.
Our Comprehensive CMMC Compliance Services include:
1. Strategic Planning & Assessment:
CMMC readiness assessments and comprehensive gap analysis
CUI system boundary definition and scoping guidance
Network architecture documentation and CUI flow diagrams
Risk assessment and vendor compliance evaluations
2. Implementation & Documentation Support:
System Security Plan (SSP) development and customization
Complete policy and procedure documentation suite
FIPS validation documentation and shared control matrices
Evidence collection strategies and management systems
3. Assessment Preparation:
Mock assessments and readiness validation
CMMC documentation optimization and organization
Personnel training and assessment preparation
C3PAO coordination and selection support
4. Ongoing Compliance:
Continuous monitoring and compliance maintenance
Annual affirmation support and triennial assessment preparation
Change management and configuration control guidance
Customized CUI awareness training programs
For immediate assistance with your CMMC compliance journey, contact our certified experts at sales@databrackets.com or schedule a free consultation.
Helpful Resources:
Summary
To summarize,
Controlled Unclassified Information (CUI) is the foundation for determining whether CMMC applies and how far its requirements extend, because only systems and processes that handle CUI fall within certification scope.
CUI is defined and categorized by the federal government, not by contractors, requiring organizations to rely on contract language, markings, and official guidance rather than internal assumptions when identifying regulated data.
Incorrectly identifying CUI creates downstream problems, either by expanding the compliance boundary unnecessarily or by excluding data that should be protected and assessed under CMMC.
Understanding where CUI resides and how it moves through the organization is essential, since data flows directly influence system boundaries, documentation accuracy, and assessment outcomes.
CUI scoping is not limited to primary systems, as shared services, supporting infrastructure, and external service providers can all become in scope if they interact with the data.
Not all sensitive or proprietary information qualifies as CUI, and treating all important data the same dilutes focus and increases compliance effort without improving certification readiness.
Effective CUI handling depends on clear documentation that explains locations, flows, and protections in a way that assessors can verify against operational reality.
CUI identification must be revisited over time, because contract changes, system modifications, and workflow adjustments can alter what data is regulated and where it is processed.
A disciplined understanding of CUI allows organizations to concentrate CMMC efforts on the environments that truly matter, supporting both efficient compliance and defensible assessments.