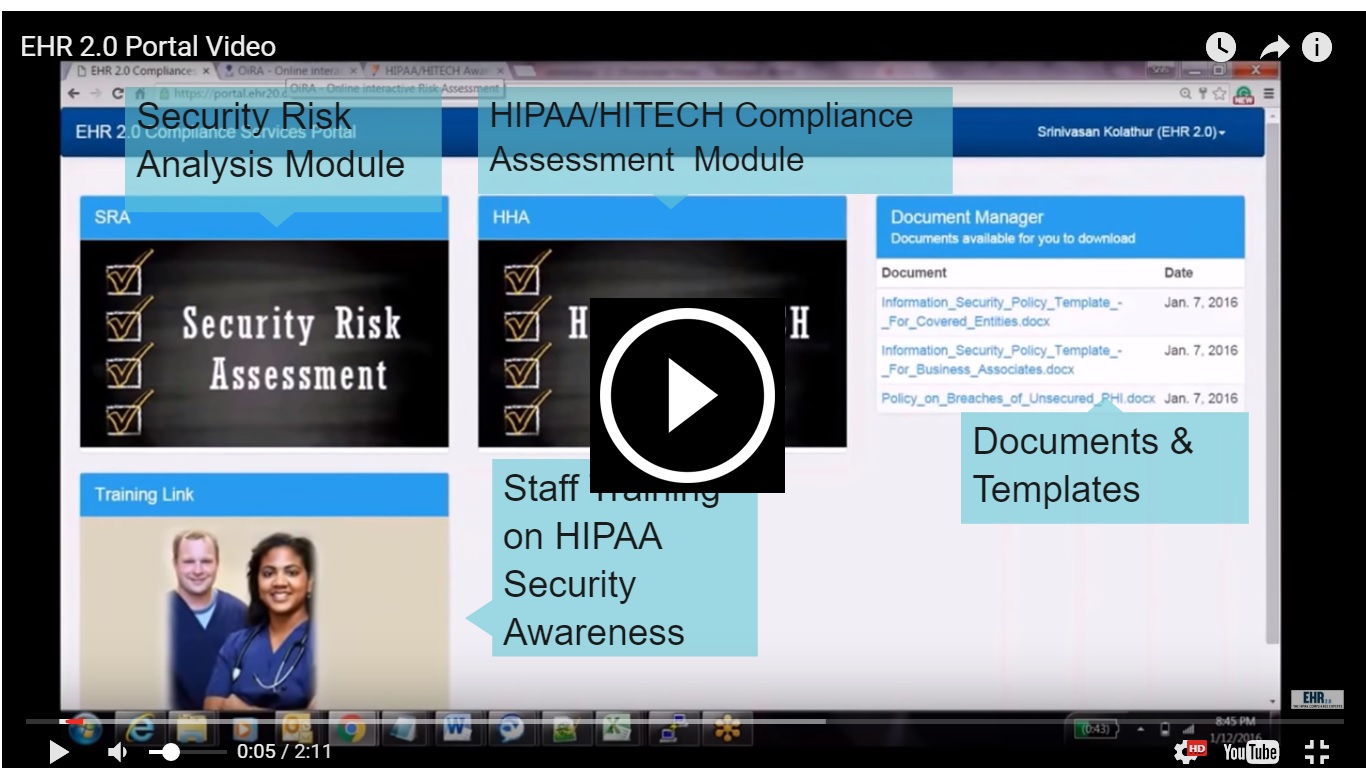
We offer a secure, user-friendly online Security Risk Assessment (SRA) platform for small medical practices with limited resources and time, to identify and prioritize security risks and demonstrate MIPS/MACRA and HIPAA compliance. Our online SRA is optimized for multiple sites with up to 50 staff. For larger practices, we recommend our consulting services.
Online Do-it-Yourself Security Risk Analysis Toolkit
Organize, Analyze, and Report your Security Risks
- Know your risks along with appropriate measures
- Evaluate impact to different technology assets
- Track exposures, prioritize risks, develop a mitigation plan using pre-populated solutions (optional) or customized approach
- Download and print your reports in hours
Meet Meaningful Use/MACRA/MIPS Security Risk Analysis Requirements
- Be prepared for meaningful use/MACRA/MIPS audits
- Build on your previous year’s report to meet annual attestation requirements


Comply with One of the Key Requirements of HIPAA/HITECH
- Electronic patient data security risk analysis is the key component of HIPAA/HITECH
- Cover yourself from OCR/HHS audit
- OCR/HHS phase 2 audit is underway
Even If It’s Random, It’s Still an Audit
- A certified security professional reviews your report and provides recommendations with our consulting option
- Protect your hard earned reputation and money
- Minimize patient data breach penalties

And More Ways to Help Meet Your Goals
- Policies and procedures template is included
- End user security awareness training
- External network vulnerability scan
- Required documents organized securely on our portal
Want to learn more about partnership/white label opportunities? We have partner program for practice management groups/IT vendors
Frequently Asked Questions
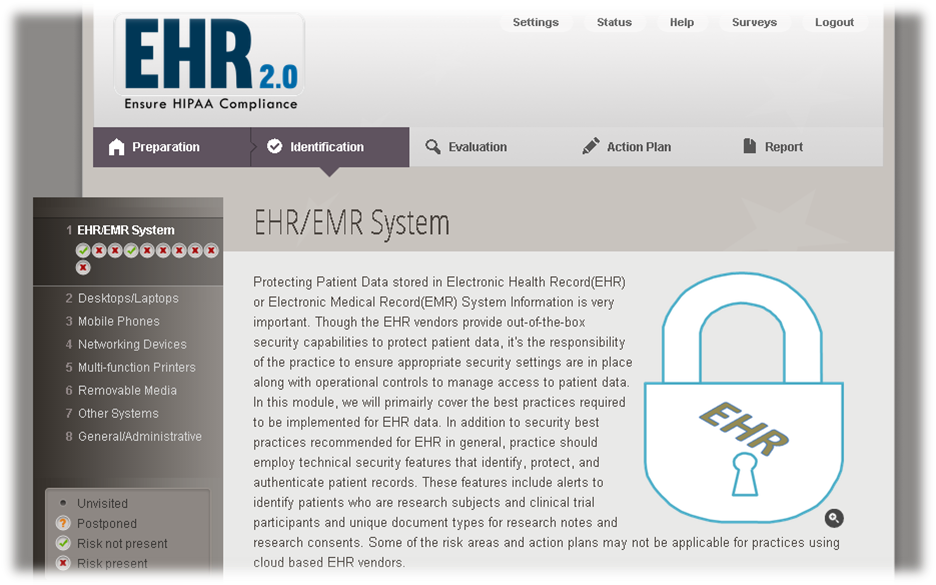
This tool can be used by anyone wishing to assess healthcare PHI-related security risks that might exist in a practice that uses electronic devices like Networking equipment, desktops, laptops, mobile devices, servers, etc.
It is a 5-step process:
Step 1: Preparation introduces the user (practice) to the risk assessment
Step 2: In identification the user goes through the risks (structured in modules / submodules) and answers YES or NO to the statements. These are always affirmative statements for consistency and are arranged in a logical order.
Step 3: Evaluation for each problem spotted, the end-user evaluates the risk
Step 4: Action Plan is filled in with measures to tackle all stated risks
Step 5: Report the action plan is converted into a report to be downloaded and printed
It’s impossible to say how long an assessment will take in general as the tools differ according to your practice setup. Usually, it should not take more than 2 to 3 hours to complete your assessment.
You do not need any kind of specific preparation to start using the tool, however you should take some time to think about who is going to carry out the risk assessment, how your IT and other people involved in PHI are going to be involved in the process, etc.
Disclaimer
This tool contains links to other websites which are not are under the control of databrackets (Agency) and the organizations involved. The Agency and the organizations involved accept no liability in respect of the content of these websites.
databrackets will not be liable for any false, inaccurate, inappropriate or incomplete information stored in the tool or any other damages as a result of using the software.
Moreover, this tool is not intended to cover all the risks of every healthcare practice but to help you put the risk assessment process into practice. For the tool to be fully effective it needs to be adapted to the context of your particular practice – some items might need to be added others omitted if they are not relevant.
For practical and analytical reasons, the tool presents problems separately, but in practices they may be intertwined. Therefore interactions between the different problems or risk factors identified must be taken into account.
Therefore, databrackets does not accept any liability for damages and claims in case a tool does not cover all risks of a given sector or any potential audit issues.
Moreover, the Agency and the organizations involved in the production of the tool do not accept any liability for damages and claims arising out of the use or inability to use the tool and the data stored therein. Similarly, databrackets does not accept any liability in case of unavailability of the function of the tools to print the report, recording the risk assessment automatically generated by the tool. Therefore, the customer has to make sure, at any time, to be in possession of a printed, accurate and up-dated risk assessment.
Explore more of our services: www.databrackets.com