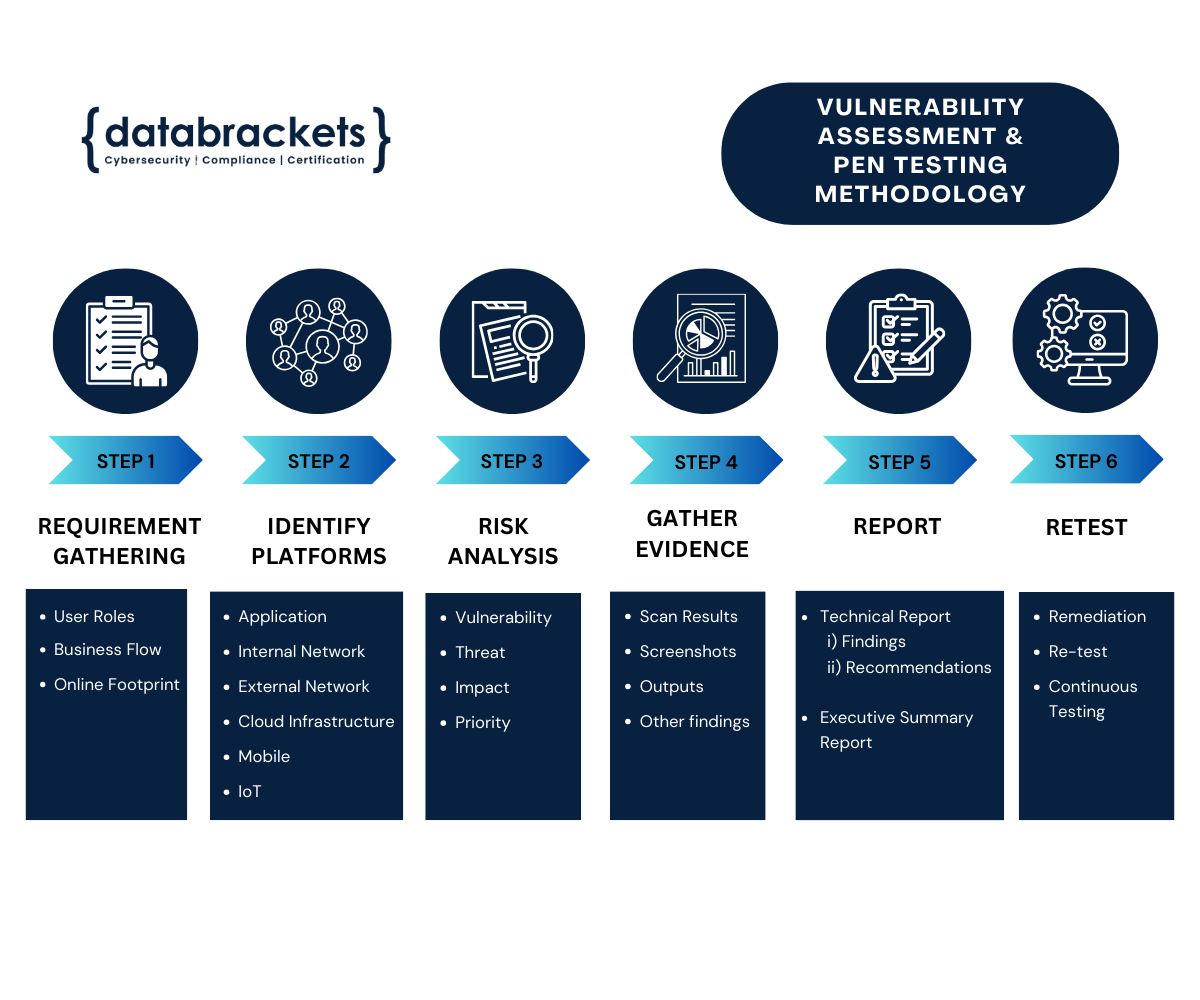
Vulnerability Assessment and Penetration Testing
Be the first to find the gaps in your network, applications, cloud services, and code before an attacker does. Learn exactly how vulnerable and exploitable your most critical systems are to cyber-attacks. databrackets’ A2LA accredited process and certified ethical hackers can help identify your security vulnerabilities in the most efficient and cost-effective way.
Vulnerability Assessment and Penetration Testing
Why Does Vulnerability Assessment and
Penetration Testing Matter?
Organizations do all they can to protect their critical data, but they don’t always systematically and periodically test their defenses. A vulnerability assessment and penetration test, colloquially known as a pen test or VAPT, is an authorized simulated cyberattack on computer systems. VAPT helps in identifying security vulnerabilities and helps prevent hacking and losing credibility with the customers. A vulnerability assessment exercise discovers vulnerabilities that are present in the system and infrastruture, but they do not exploit the flaws identified. However, a penetration test is meant to show how damaging a flaw could be in a real attack rather than find every flaw in a system. Together, penetration testing and vulnerability assessment process provides a detailed picture of the flaws that exist in an application and the real risks associated with those flaws. Penetration testing from databrackets consulting services helps you strengthen your security for those systems by identifying vulnerabilities, misconfigurations and missing best practices in your business posture.

Why databrackets?
- Accredited By Reputed Organizations
- Combination of Manual and Automated Process
- Our Pen Test Guarantee
- Our Quick Turnaround Time
- Framwork-Based Approach
- Best Value for Your Money
What is Covered in VAPT?
Internal Network
External Network
Web Application
Mobile Apps
Cloud Infrastructure
IoT Devices
Internal Network
 An internal penetration test leverages the exploited box from an external penetration test, or a device on the inside of the network to conduct the assessment. Internal reconnaissance and attacks are launched while a poorly secured domain control may lead to total control of the network, most tests require multiple attack paths to achieve their testing objectives. This method often includes exploiting less-important systems and then leveraging information found on these systems to attack more important systems in the network.
An internal penetration test leverages the exploited box from an external penetration test, or a device on the inside of the network to conduct the assessment. Internal reconnaissance and attacks are launched while a poorly secured domain control may lead to total control of the network, most tests require multiple attack paths to achieve their testing objectives. This method often includes exploiting less-important systems and then leveraging information found on these systems to attack more important systems in the network.
External Network
 An external penetration test attempts to gain entry into the internal network by leveraging vulnerabilities discovered on the external assets. The external penetration test includes reconnaissance on the in-scope assets, gathering intelligence on all assets in scope. This intelligence includes open ports, vulnerabilities, and general information about the organization’s users for password attacks. Once the perimeter is successfully breached, the objectives of the external penetration test has been achieved, and the tester moves to the internal penetration test.
An external penetration test attempts to gain entry into the internal network by leveraging vulnerabilities discovered on the external assets. The external penetration test includes reconnaissance on the in-scope assets, gathering intelligence on all assets in scope. This intelligence includes open ports, vulnerabilities, and general information about the organization’s users for password attacks. Once the perimeter is successfully breached, the objectives of the external penetration test has been achieved, and the tester moves to the internal penetration test.
Web Application
 Web application penetration testing is done by simulating unauthorized attacks on the in-scope application to get access to sensitive data. A web application penetration testing helps the organization find out the possibility for a hacker to access the data from the internet and exploit the vulnerabilities in the web-facing internet applications. Our service includes both manual and automated web application penetration testing as automated penetration testing tools simply can’t find every flaw. Our manual testing identifies complex authorization issues to business logic flaws.
Web application penetration testing is done by simulating unauthorized attacks on the in-scope application to get access to sensitive data. A web application penetration testing helps the organization find out the possibility for a hacker to access the data from the internet and exploit the vulnerabilities in the web-facing internet applications. Our service includes both manual and automated web application penetration testing as automated penetration testing tools simply can’t find every flaw. Our manual testing identifies complex authorization issues to business logic flaws.
Mobile Apps
 databracket’s mobile application penetration testing covers the complete mobile app environment, from the local app running on-device to the back-end web services and RESTful APIs that power mobile apps. Our mobile penetration testing includes security, privacy, and compliance risks introduced via Mobile Apps, Mobile Devices, and IoT Devices. Our methodologies ensures all back-doors are identified and vulnerabilities whether they are there accidentally or purposefully.
databracket’s mobile application penetration testing covers the complete mobile app environment, from the local app running on-device to the back-end web services and RESTful APIs that power mobile apps. Our mobile penetration testing includes security, privacy, and compliance risks introduced via Mobile Apps, Mobile Devices, and IoT Devices. Our methodologies ensures all back-doors are identified and vulnerabilities whether they are there accidentally or purposefully.
Cloud Infrastructure
 A cloud infrastructure penetration test aims to uncover vulnerabilities within the cloud-based assets by simulating external attacks. This involves conducting reconnaissance on the targeted assets within the cloud environment, gathering pertinent information such as open ports, misconfiguration, identified vulnerabilities, and insights into the organization’s user base for potential password-related exploits. Upon successful breach of the cloud infrastructure’s perimeter, the primary goals of the external penetration test are accomplished, signaling the transition to the internal penetration testing phase.
A cloud infrastructure penetration test aims to uncover vulnerabilities within the cloud-based assets by simulating external attacks. This involves conducting reconnaissance on the targeted assets within the cloud environment, gathering pertinent information such as open ports, misconfiguration, identified vulnerabilities, and insights into the organization’s user base for potential password-related exploits. Upon successful breach of the cloud infrastructure’s perimeter, the primary goals of the external penetration test are accomplished, signaling the transition to the internal penetration testing phase.
IoT Devices
 databrackets leverages knowledge-based approach with homegrown and commercial tools mixed together to accomplish IoT penetration testing. We cover IoT devices that run over a network, such as the Internet, BLE, 4G, LTE, Zigbee, LoRA, WiFi, MQTT, 802.11.15.4, etc. Some of the IoT device hardware including chip, storage, JTAG, UART ports, Sensors, Camera, port, sensor, camera, firmware or other devices is included as part of IoT pen testing.
databrackets leverages knowledge-based approach with homegrown and commercial tools mixed together to accomplish IoT penetration testing. We cover IoT devices that run over a network, such as the Internet, BLE, 4G, LTE, Zigbee, LoRA, WiFi, MQTT, 802.11.15.4, etc. Some of the IoT device hardware including chip, storage, JTAG, UART ports, Sensors, Camera, port, sensor, camera, firmware or other devices is included as part of IoT pen testing. Methodology