dbACE - Cybersecurity, Compliance and
Audit Management Platform
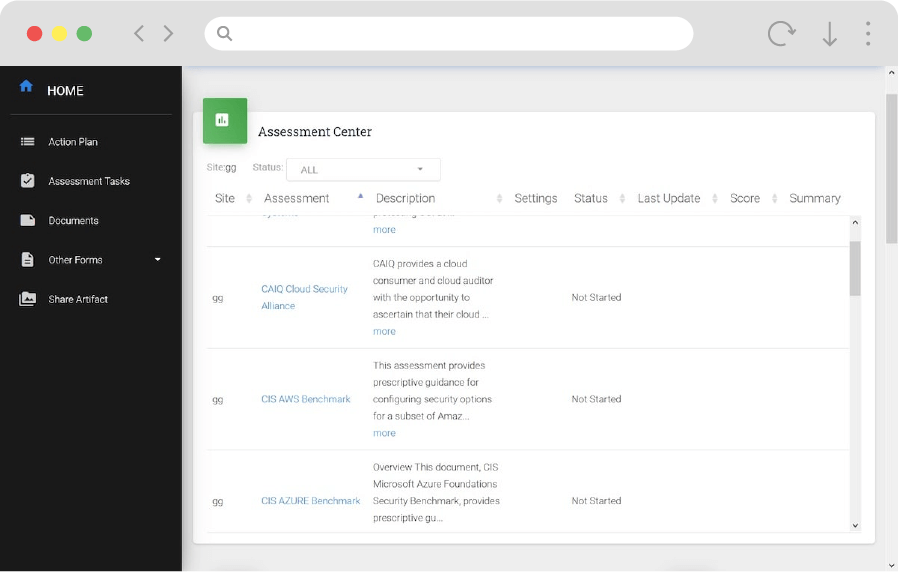
databrackets offers a secure and user-friendly online assessment platform for small to medium-sized organizations and partners with limited resources and time, to complete cybersecurity, compliance and standards assessments, identify gap areas, prioritize solutions, and demonstrate compliance with Government regulations.
Assessment libraries, risk register, customized documents, training, integration and much more...
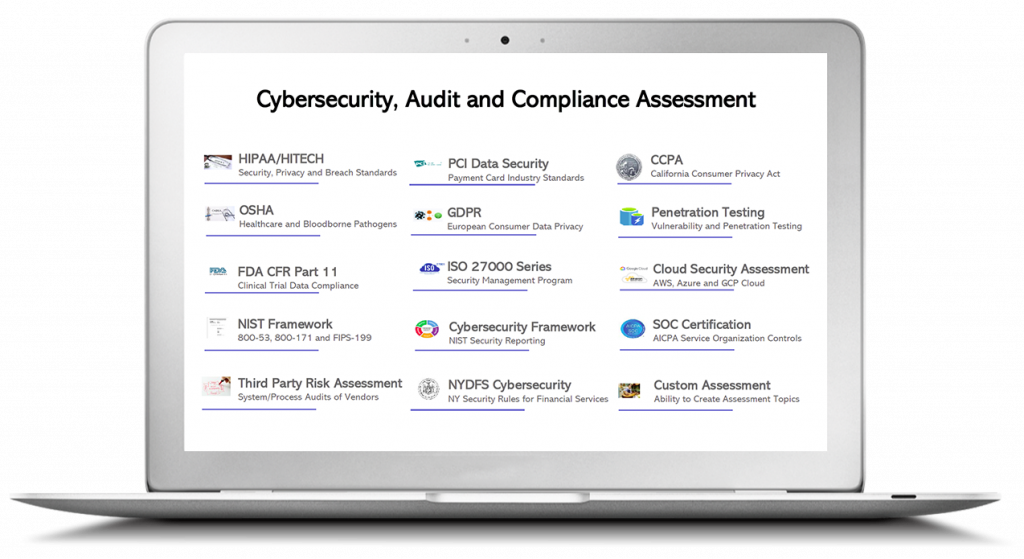
Compliance & Cybersecurity Standard Libraries
- Assess using a comprehensive platform-based approach to efficiently utilize resources
- Protect your business from agency audit and cyber insurance challenges
- Track gaps, prioritize risks, develop mitigation plan using the pre-populated solution
- Get notified on regulatory updates, action plans, etc.
- Minimize sensitive data breach
AI-Powered Platform
- Secure AI capabilities enable quick drafting of responses and action plans from simple prompts—minimizing manual effort and improving consistency
- Instantly generate executive-level summaries from assessment data, making it easy to deliver clear, actionable reports to your customers
- Get real-time answers to customer inquiries and RFP questionnaires through an intelligent, embedded chatbot interface
- Seamlessly verify using dbACE AI engine that all required control objectives are fulfilled—automatically. (Coming soon)
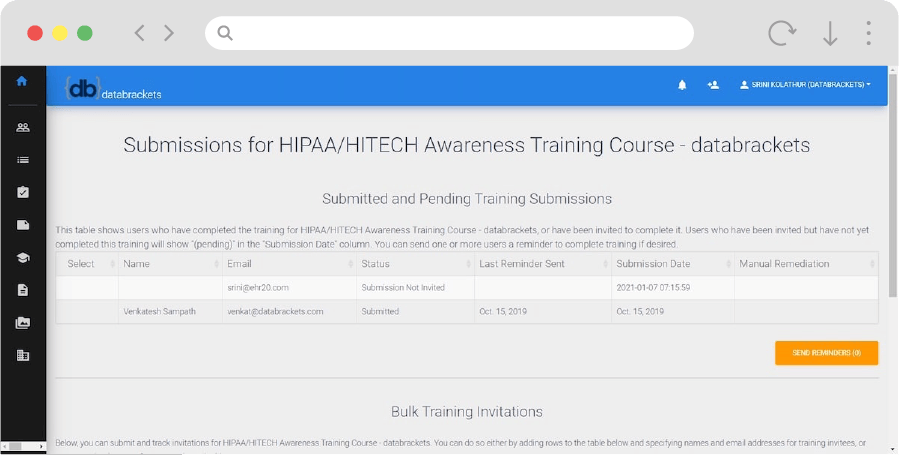
Online Training Center
- User Awareness Training on various Compliance and Assessment topics
- Role-based Training that offers customized Training depending on a specific role or function
- Compliance Assessment and Evaluation as a key element in measuring the effectiveness of monitoring, control, and surveillance (MCS)
- Certification of professionals participating in the Training
- Training Logs/Reports that help to track Employee Training
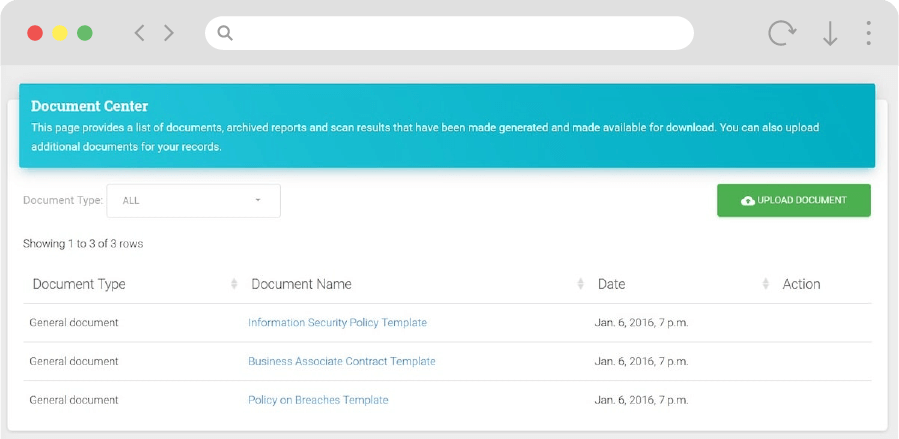
Document Center
- Policies and procedures template
- Customized documents based on user input
- Documents and templates for compliance and certification
- Analyze documents/evidence based on assessment types
- Ability to create custom documents/procedures
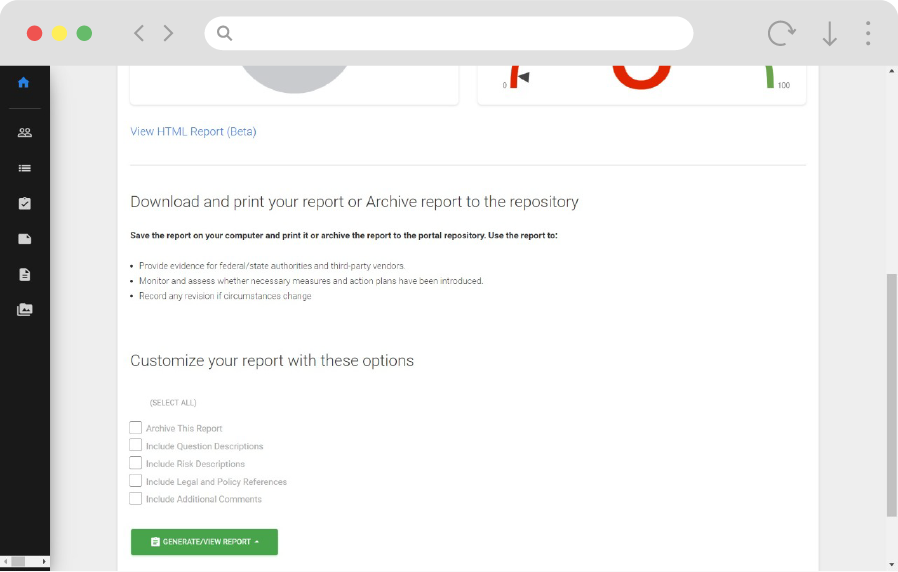
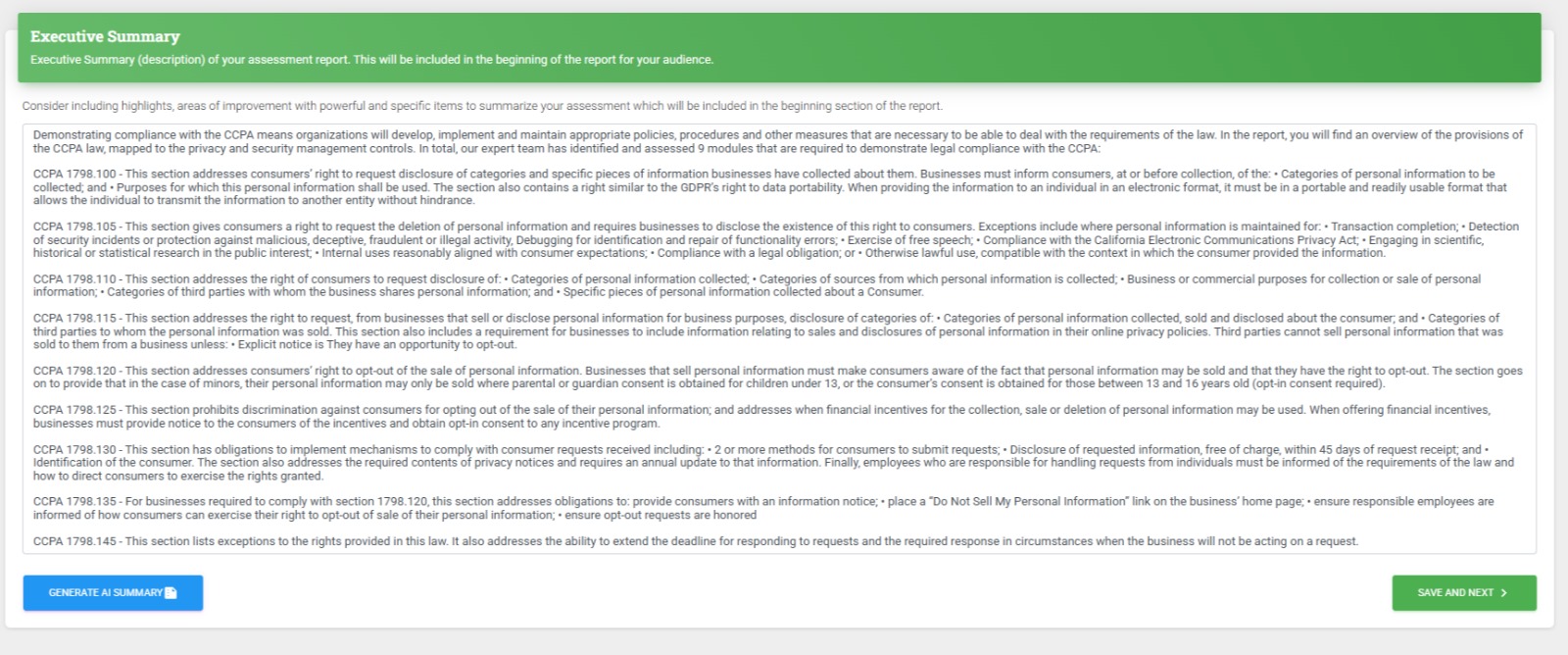
Customizable Reports
- Comprehensive assessment reports generation
- The download of reports in flexible format – PDF/Excel and Document
- Action plans updates and regeneration of remediated reports
- Generation of reports for executive management, technical teams, customers, and partners
Generate Policies and Procedures
- Security, Privacy, and Breach Templates for easy customization
- Leveraging our comprehensive list of documents to save time and cost
- Additional customization feature to the templates to tailor your needs
- Leverage our secured online portal to manage policies and procedures

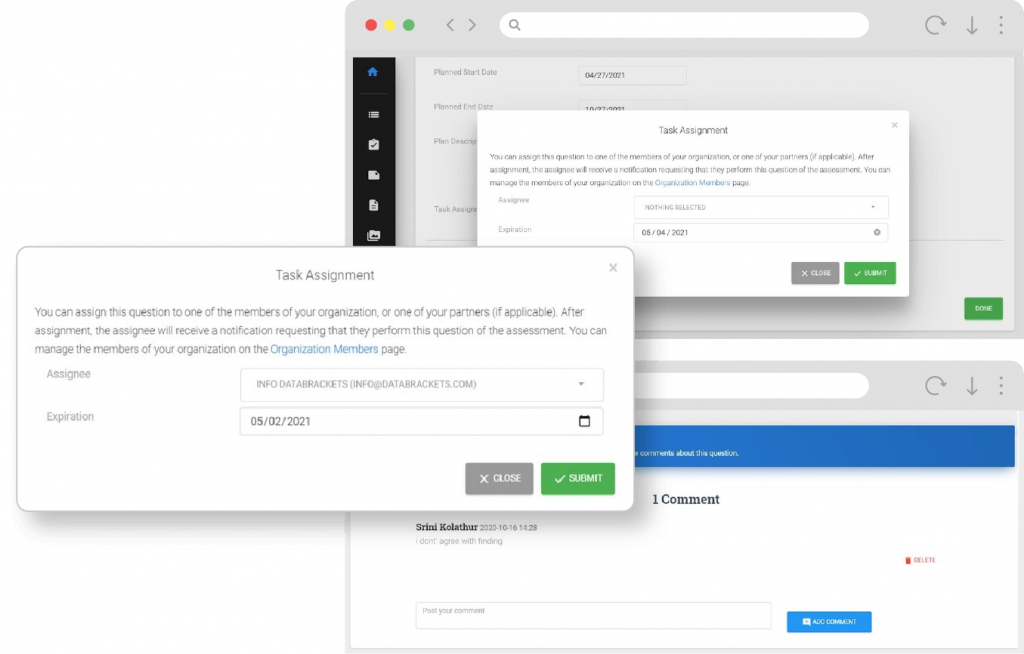
Manage Workflows
- Assignment of tasks to individuals, internal and external auditors
- Creation of comments and observations to notify the task owners
- Enablement of notifications on specific tasks
- Validation of responses and evidence
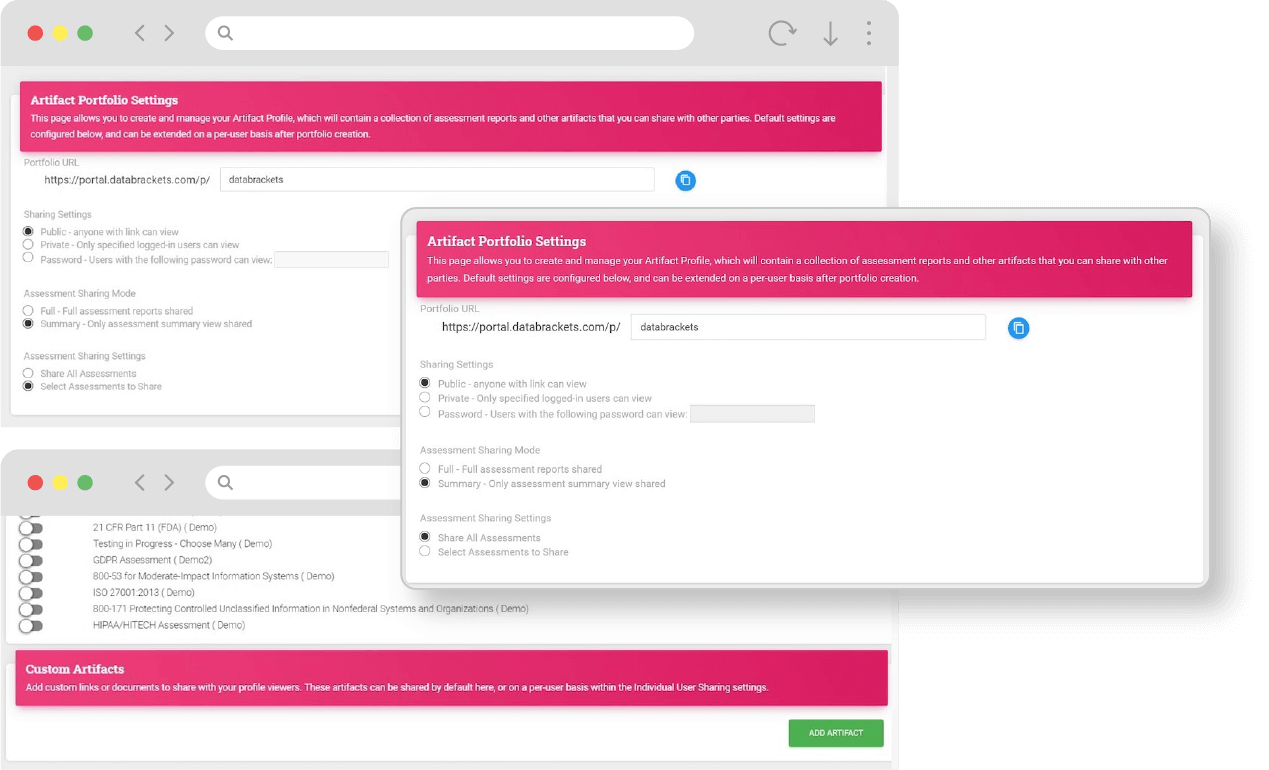
Share Artifacts
- Sharing of summary or detailed assessment report with your customers/stakeholders
- Safeguarding and countermeasures in the information that are shared
- Provision of access to all your prospective customers to save time and cost
- Publication of your latest reports and making them available in real-time
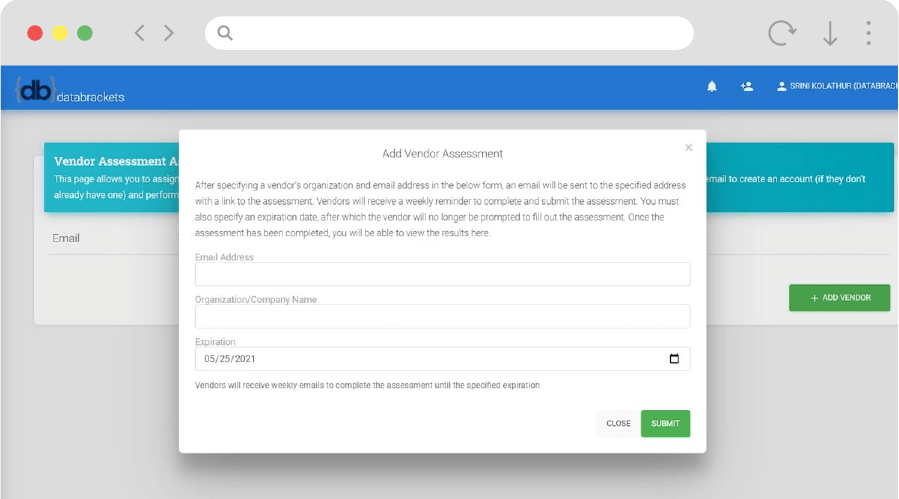
Assess Third-Party Vendor Risks
- Identification and management of your critical vendors’ risks
- Assignment of cybersecurity and compliance assessments to vendors and tracking progress
- Management of your vendor’s remediation plans and reminders
- Provision of vendor access to the management of assessments
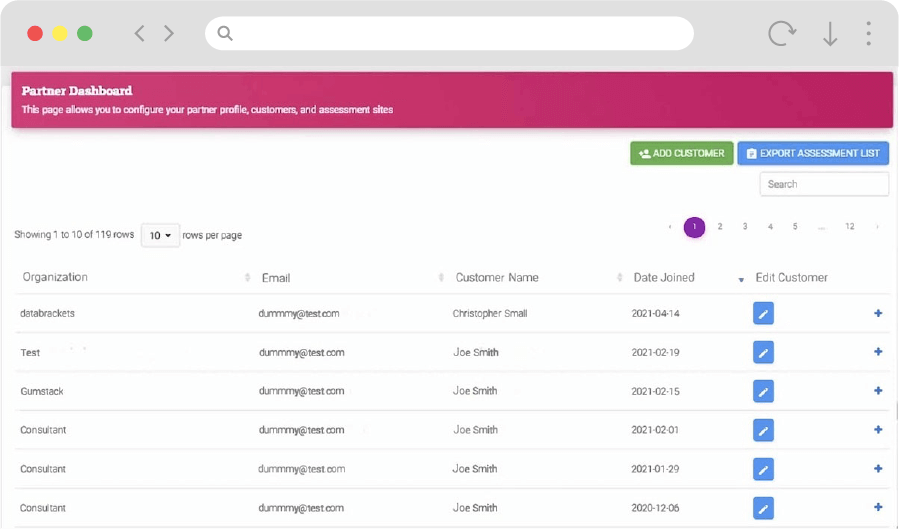
Partner Capabilities
- White Label, multi-customers, multi-users, and partner dashboard
- Collaboration with multiple members, vendors, and stakeholders
- Provision of portal access to end-customers
- Messaging, templates, and document sharing with private or public groups
- Complete control around handling end customers
- Deploy custom assessments to customers
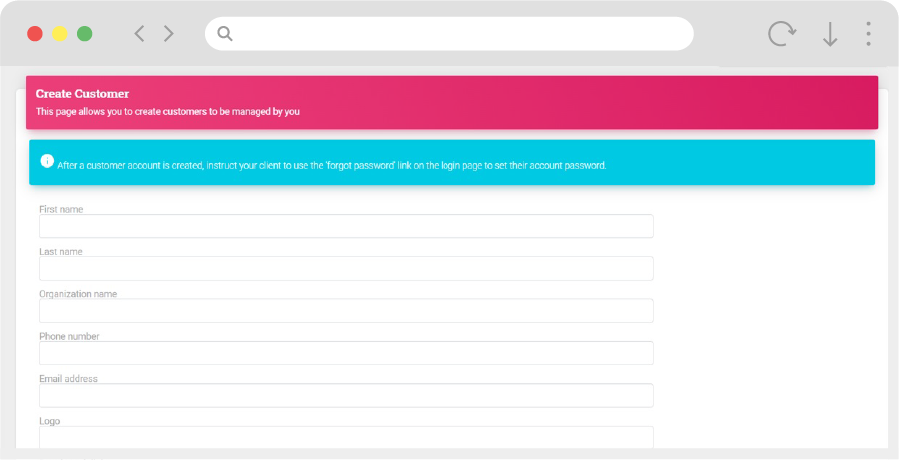
Generate Custom Assessments
- Creation of new assessments for partner customers
- Assignment and management custom assessments
- Management of custom assessments using Partner dashboards
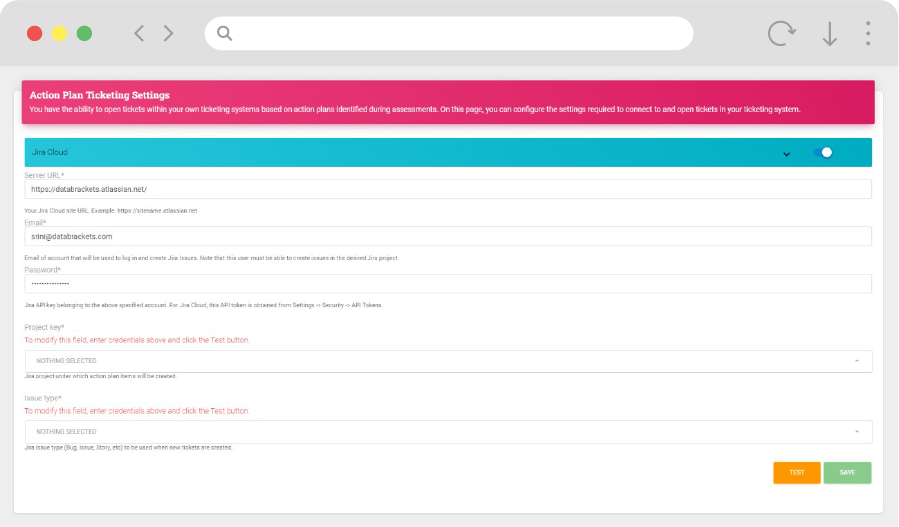
API Integrations
- Connect with your ticketing/task management systems
- Jira, Servicenow and other leading ticketing systems
- Monitor, Track and Update Tickets/Tasks Status (bi-directional)
And More Ways to Help Meet Your Goals
- The best customer support in the industry
- Use APIs to integrate with third-party platforms
- Secure access with multi-factor authorization
- Value for your money
What is SaaS-based Assessment Tool?
It is a web-based tool that allows you to perform cybersecurity, audit and compliance assessment of your sensitive data without having to install any software or host any system on-premise*.
Who is the platform for?
This platform can be used by all types of industries and partners wishing to assess their business based on updated cybersecurity, compliance and audit rules
What do I have to do?
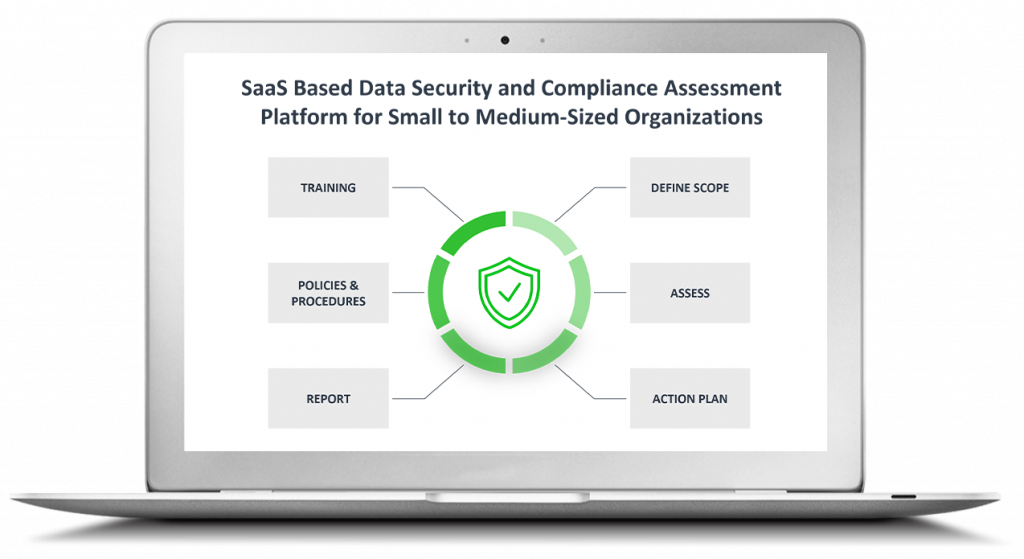
It is a 5-step process:
Introduces the user to the assessment process
The user goes through the standards (structured in modules/submodules) and answers YES or NO or NOT APPLICABLE to the questions. These are always affirmative statements for consistency and are arranged in a logical order.
For each problem spotted, the end-user evaluates the risk
Is filled in with measures to tackle all stated risks
The action plan is converted into a report to be downloaded and printed
How long will it take?
It’s impossible to say how long an assessment will take in general as the tools differ according to your practice setup. Usually, it should not take more than 3 to 5 hours to complete your assessment.
Do I need to prepare?
You do not need any kind of specific preparation to start using the tool, however, you should take some time to think about who is going to carry out the risk assessment, how your IT and other people involved in sensitive data are going to be involved in the process, etc.
Disclaimer
Platform contains links to other websites which are not under the control of databrackets (Agency) and the organizations involved. The Agency and the organizations involved accept no liability in respect of the content of these websites.
databrackets will not be liable for any false, inaccurate, inappropriate, or incomplete information stored in the tool or any other damages as a result of using the software.
Moreover, the platform is not intended to cover all the risks of every industry but to help you put the risk assessment process into practice. For the tool to be fully effective, it needs to be adapted to the context of your particular practice – some items might need to be added others omitted if they are not relevant.
For practical and analytical reasons, the tool presents problems separately, but in practice, they may be intertwined. Therefore interactions between the different problems or risk factors identified must be taken into account.
Therefore, databrackets does not accept any liability for damages and claims in case a tool does not cover all risks of a given sector or any potential audit issues.
Moreover, the Agency and the organizations involved in the production of the tool do not accept any liability for damages and claims arising out of the use or inability to use the tool and the data stored therein. Similarly, databrackets does not accept any liability in case of unavailability of the function of the tools to print the report, recording the risk assessment automatically generated by the tool. Therefore, the customer has to make sure, at any time, to be in possession of a printed, accurate, and up-dated risk assessment.