NIST SP 800-171 Rev 2 serves as the strategic foundation for CMMC compliance success. Organizations that master NIST implementation first can dramatically reduce CMMC certification costs, accelerate timelines, and increase certification success rates. This isn’t about choosing between frameworks—it’s about leveraging their complementary relationship for maximum competitive advantage in the Defense Industrial Base.
Important Note on NIST Versions: The DoD requires contractors to continue complying with NIST SP 800-171 Rev 2 until further notice.
The Strategic Relationship Between
NIST SP 800-171 and CMMC
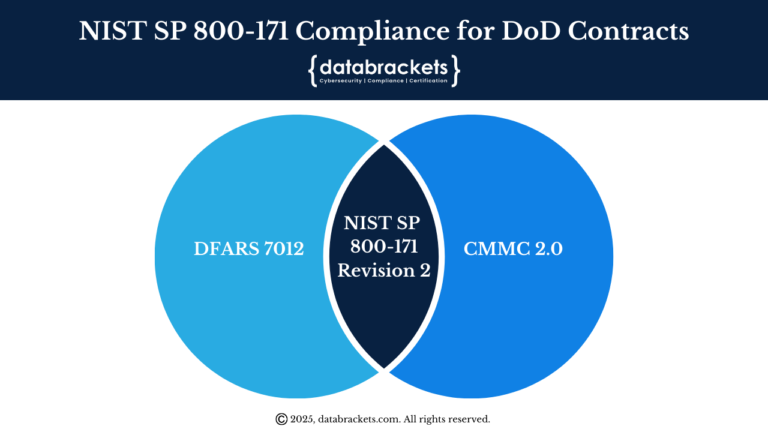
NIST SP 800-171 Rev 2 provides the foundation for cybersecurity controls that CMMC builds upon. CMMC is a certification program, while NIST SP 800-171 Rev 2 is a set of guidelines. These frameworks are designed to work together rather than compete.
NIST SP 800-171 Rev 2 provides the technical foundation and implementation guidance, while CMMC adds the verification mechanisms and competitive advantages that defense contractors need. Organizations that recognize this complementary relationship can optimize their compliance investments and achieve greater certification success.
Learn about Comparing NIST SP 800-171 and CMMC
The Power of Complying with NIST SP 800-171 and CMMC
Implementing one standard largely satisfies the requirements of the other, creating unprecedented efficiency opportunities for defense contractors:
1. Efficient Resource Utilization: Since CMMC Level 2 incorporates all 110 NIST SP 800-171 requirements, organizations that implement NIST SP 800-171 have already satisfied the majority of CMMC Level 2 requirements. For CMMC Level 3, organizations gain an even greater advantage as all 110 NIST SP 800-171 controls are required, with only 24 additional enhanced controls from NIST SP 800-172 needed to achieve the full 134-control requirement. This means NIST SP 800-171 compliance provides 82% coverage for CMMC Level 3, eliminating duplicative efforts and maximizing return on compliance investments across all CMMC certification levels.
2. Streamlined Documentation: Documentation developed for NIST SP 800-171 compliance—including System Security Plans (SSP) and Plans of Action and Milestones (POA&M)—can be leveraged directly for CMMC certification, reducing documentation burden by up to 70%.
Learn more about CMMC Documentation
3. Progressive Implementation: Organizations can focus on NIST SP 800-171 compliance first, then address the additional CMMC requirements through targeted enhancements rather than wholesale program redesign.
4. Risk Reduction: Properly implementing either framework significantly reduces cybersecurity risk while creating the foundation for enhanced security maturity across the organization.
Implementation Roadmap for NIST SP 800-171 and CMMC
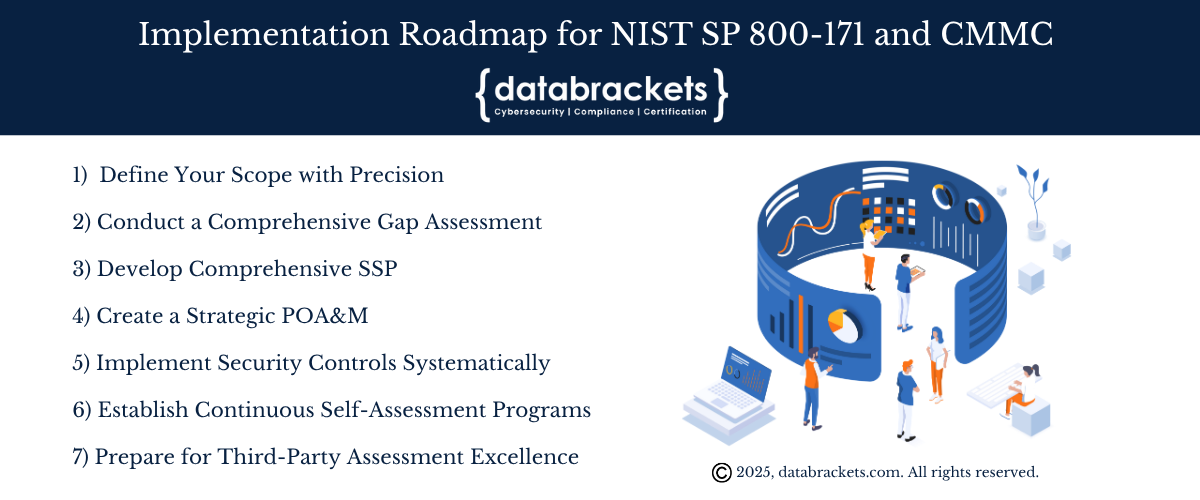
Achieving compliance requires a systematic approach that maximizes efficiency while ensuring comprehensive coverage. Here’s the proven roadmap that successful organizations follow:
Step 1: Define Your Scope with Precision
Strategic scoping dramatically impacts compliance effort and cost. Organizations must identify where Controlled Unclassified Information (CUI) exists within their environment:
System Identification: Which systems process, store, or transmit CUI?
Boundary Definition: What are the precise boundaries of your CUI environment?
Segmentation Opportunities: Can you segment CUI from other data to reduce your compliance burden?
Implementing proper scoping can reduce compliance efforts by 40-60% by limiting the systems that must meet all requirements. This strategic approach allows organizations to focus resources on protecting critical assets while maintaining operational efficiency.
Learn more about CUI for CMMC
Step 2: Conduct a Comprehensive Gap Assessment
Before implementing changes, organizations must assess their current environment against all applicable requirements using proven methodologies:
Current State Documentation: Document existing security controls with detailed implementation descriptions
Gap Identification: Identify specific deficiencies using NIST SP 800-171A assessment procedures
Risk-Based Prioritization: Prioritize gaps based on risk impact and implementation complexity
Resource Planning: Determine budget, timeline, and personnel requirements for remediation
A thorough gap assessment provides the clear roadmap essential for compliance success and helps organizations avoid costly implementation mistakes.
Step 3: Develop Comprehensive System Security Plan (SSP)
The SSP serves as the cornerstone document outlining how your organization meets each requirement. Successful SSPs include:
Implementation Status: Document the current implementation status for each of the 110 requirements
Responsibility Matrix: Define clear responsibilities for security control implementation and maintenance
Technical Specifications: Specify technologies and processes that address each requirement with detailed configuration settings
Evidence Collection: Include systematic approaches for collecting and maintaining compliance evidence
Learn more about Creating an SSP for CMMC & CMMC Documentation
Step 4: Create a Strategic Plan of Action and Milestones (POA&M)
The POA&M addresses gaps identified during assessment while considering framework-specific restrictions. Organizations must understand that they—not the DoD—are responsible for creating and maintaining POA&Ms:
For NIST SP 800-171: Organizations develop and maintain POA&Ms as part of their SSP with flexibility in timeline management and scope inclusion.
For CMMC: Organizations develop POA&Ms for assessment-identified gaps, though certain high-risk deficiencies may not be allowable under POA&M status, depending on the specific contract requirements. Critical restrictions include:
Level 1: No POA&Ms permitted at any time for self-assessments
Level 2: POA&Ms allowed only for certain low-impact controls with specific exclusions including AC.L2-3.1.22 (privileged functions), AC.L2-3.1.20 (external connections), CA.L2-3.12.4 (SSP development), PE.L2-3.10.3, PE.L2-3.10.4, and PE.L2-3.10.5 (physical access controls)
Level 3: POA&Ms permitted for non-critical requirements only with similar high-priority restrictions as Level 2
Organizations must achieve a minimum score of 80% on the initial assessment (88 out of 110 points for Level 2) with POA&Ms limited to a maximum of 22 security requirements valued at 1 point each, plus one exception for SC.L2-3.13.11 (CUI Encryption) at 3 points if partially implemented.
Effective POA&Ms include detailed gap documentation, assigned remediation responsibility, realistic implementation timelines, required resource allocation, and systematic progress tracking toward full compliance. Critical POA&M management considerations include:
Timeline Requirements: All POA&M items must be remediated within 180 days maximum for CMMC Levels 2 and 3, after which certification expires if issues aren’t resolved. NIST SP 800-171 does not mandate specific timeframes, allowing more flexible remediation scheduling.
Approval Process: CMMC POA&Ms must be approved by the assessor (C3PAO for certification assessments or self-managed for self-assessments), while NIST SP 800-171 POA&Ms are self-managed internally.
Remediation Tracking: CMMC requires tracking through eMASS for certification assessments with automatic transmission to SPRS, while NIST SP 800-171 uses internal processes via SPRS reporting.
Closeout Assessment: CMMC requires a formal POA&M closeout assessment (self-assessment for self-assessments, C3PAO assessment for certifications), while NIST SP 800-171 requires no formal closeout process.
Consequences of Non-Completion: CMMC certification expires with potential contractual penalties up to termination, while NIST SP 800-171 non-completion remains an internal risk management decision.
Step 5: Implement Security Controls Systematically
Based on gap assessment and POA&M priorities, implement necessary security controls across three categories:
1. Technical Controls: Deploy solutions, including multi-factor authentication, encryption, access controls, logging systems, and vulnerability management platforms.
2. Administrative Controls: Develop comprehensive policies, procedures, training programs, incident response plans, and risk management processes.
3. Physical Controls: Implement physical security measures for systems containing CUI, including facility access controls, environmental protections, and media handling procedures.
Step 6: Establish Continuous Self-Assessment Programs
Ongoing self-assessment ensures sustained compliance and preparation for formal assessments:
Periodic Reviews: Conduct quarterly reviews of all 110 requirements with documented findings
Control Testing: Test controls systematically to ensure continued effectiveness
Documentation Maintenance: Update all compliance documentation to reflect environmental changes
Assessment Preparation: Identify and address deficiencies proactively before formal assessments
Step 7: Prepare for Third-Party Assessment Excellence
For organizations pursuing CMMC certification, thorough preparation ensures assessment success:
C3PAO Engagement: Select qualified Certified Third-Party Assessment Organizations with proven track records
Pre-Assessment Activities: Conduct comprehensive mock assessments to identify potential issues
Findings Remediation: Address all pre-assessment findings with documented evidence
Formal Assessment Scheduling: Complete assessments with confidence in successful outcomes
How to Overcome Common Implementation Challenges for
NIST SP 800-171 and CMMC
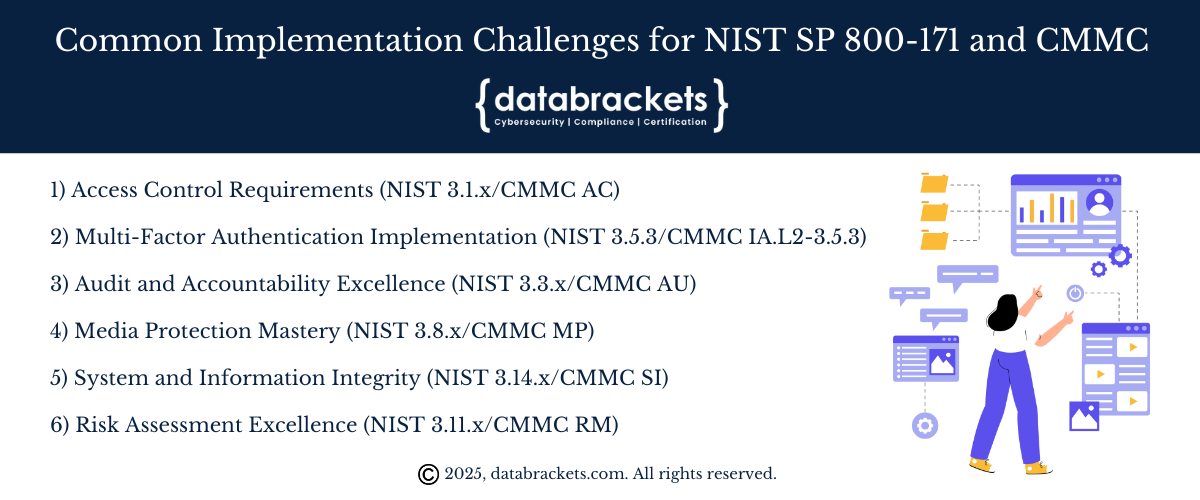
When implementing NIST SP 800-171 or CMMC, organizations encounter specific challenges that require targeted solutions:
Challenge 1: Access Control Requirements (NIST 3.1.x / CMMC AC)
Access control is one of the most complex implementation areas, requiring both technical and administrative solutions to ensure security and compliance.
Strategic Solution: Enforce the Principle of Least Privilege Through a Systematic Approach
Define and document user access requirements(NIST 3.1.1 / CMMC AC.1.001) Identify and record the types of information and system access each user or role requires, based on business and security needs.
Restrict access based on authorized user functions(NIST 3.1.2 / CMMC AC.1.002) Limit system access to only the specific transactions and functions users are authorized to perform.
Implement separation of duties to reduce risk(NIST 3.1.3 / CMMC AC.L2-3.1.3) Design roles and responsibilities so no single individual can execute critical functions independently, minimizing the potential for fraud or abuse.
Establish procedures for managing privileged accounts(NIST 3.1.5 / CMMC AC.L2-3.1.5) Develop and enforce specialized processes to control, monitor, and audit privileged user access.
Challenge 2: Multi-Factor Authentication Implementation (NIST 3.5.3 / CMMC IA.L2-3.5.3)
Multi-factor authentication (MFA) is required by NIST SP 800-171 control 3.5.3 and CMMC practice IA.L2-3.5.3 for both privileged accounts and remote user access. Implementation can be challenging due to legacy systems, integration complexities, and user experience concerns.
Strategic Solution: Implement MFA in a Phased and Compliant Manner
Enforce MFA for all privileged accounts as a top priority(NIST 3.5.3 / CMMC IA.L2-3.5.3)
Extend MFA to all forms of remote access, including VPNs, web applications, and cloud-based systems.
Use FIPS-compliant authenticators in accordance with NIST guidelines to ensure secure authentication.
Document any MFA exceptions and implement compensating security controls.
Integrate MFA with identity and access management (IAM) systems to maintain usability and system integrity.
Challenge 3: Audit and Accountability Excellence (NIST 3.3.x / CMMC AU)
Robust audit and accountability controls are critical for detecting and responding to security events. These require reliable infrastructure, consistent data collection, and secure log management.
Infrastructure Solution: Build a Compliant and Scalable Logging Environment
Implement centralized logging across all relevant systems(NIST 3.3.1 / CMMC AU.L2-3.3.1)
Ensure audit logs capture essential elements, including timestamps, user activity, and system events(NIST 3.3.2 / CMMC AU.L2-3.3.2)
Protect log data from unauthorized access or modification(NIST 3.3.8 / CMMC AU.L2-3.3.8)
Define and enforce log retention schedules in accordance with regulatory or contractual requirements(NIST 3.3.9 / CMMC AU.L2-3.3.9)
Challenge 4: Media Protection Mastery (NIST 3.8.x / CMMC MP)
Media protection is often difficult to operationalize due to the physical nature of devices and the sensitivity of Controlled Unclassified Information (CUI) stored on them.
Comprehensive Solution: Establish Media Protection Controls Across the Lifecycle
Apply physical and technical safeguards to all media containing CUI(NIST 3.8.1 / CMMC MP.L2-3.8.1)
Develop and follow documented sanitization procedures for various media types(NIST 3.8.3 / CMMC MP.L2-3.8.3)
Maintain auditable records of media sanitization actions and outcomes(NIST 3.8.9 / CMMC MP.L2-3.8.9)
Train personnel in proper media handling procedures, and validate compliance to minimize risk
Challenge 5: System and Information Integrity (NIST 3.14.x / CMMC SI)
Maintaining system and data integrity requires proactive vulnerability management and continuous monitoring.
Systematic Solution: Establish a Comprehensive Integrity Assurance Program
Identify, report, and remediate system flaws in a timely manner(NIST 3.14.1 / CMMC SI.L2-3.14.1)
Perform regular vulnerability scans and document remediation efforts(NIST 3.14.2 / CMMC SI.L2-3.14.2)
Implement and maintain anti-malware tools(NIST 3.14.4 / CMMC SI.L2-3.14.4)
Continuously monitor and respond to security alerts and threat advisories(NIST 3.14.3 / CMMC SI.L2-3.14.3)
Challenge 6: Risk Assessment Excellence (NIST 3.11.x / CMMC RM)
Effective risk assessment supports informed decision-making and requires specialized expertise and consistent implementation.
Strategic Solution: Operationalize Risk Assessment at the Enterprise Level
Conduct routine vulnerability assessments and risk analyses(NIST 3.11.1 / CMMC RM.L2-3.11.1)
Prioritize and remediate vulnerabilities based on contextual risk and impact(NIST 3.11.3 / CMMC RM.L2-3.11.3)
Develop and maintain an enterprise risk management framework, incorporating risk acceptance, mitigation, and transfer strategies
Schedule periodic risk assessments, documenting findings and corrective actions
Learn more about Overcoming 10 Critical Pitfalls for CMMC
Preparing for Regulatory Changes to
NIST SP 800-171 and CMMC
Cybersecurity standards continue evolving in response to emerging threats and technological changes. Organizations must prepare for upcoming regulatory developments:
NIST SP 800-171 Revision 3 Impact
NIST released Revision 3 of Special Publication 800-171 in 2023, introducing significant updates:
Enhanced CUI Protection: Strengthened requirements for securing controlled unclassified information
Framework Alignment: Greater alignment with NIST’s Cybersecurity Framework
Implementation Guidance: More detailed guidance for complex control implementation
Supply Chain Focus: Additional requirements for supply chain risk management
Future CMMC Evolution
The release of NIST SP 800-171 Revision 3 will impact future CMMC requirements:
Requirement Integration: DoD has indicated future CMMC versions will incorporate Revision 3 requirements
Timeline Monitoring: Organizations should monitor both NIST and CMMC program offices for implementation announcements
Assessment Preparation: Contractors should prepare for potential changes to CMMC assessment requirements
Strategic Planning for Regulatory Changes
To effectively manage ongoing regulatory evolution:
Responsibility Assignment: Designate personnel for continuous regulatory monitoring
Industry Engagement: Participate in industry forums and DoD outreach events
Program Flexibility: Build adaptability into compliance programs to accommodate new requirements
Expert Relationships: Develop partnerships with compliance experts providing guidance on emerging requirements
Your Strategic Path to Compliance Excellence
The path to successful NIST SP 800-171 and CMMC compliance begins with understanding their complementary relationship and leveraging their synergies for maximum efficiency. Organizations that use NIST SP 800-171 Rev 2 as their strategic foundation for CMMC preparation achieve superior outcomes with reduced costs, accelerated timelines, and increased certification success rates.
Success requires comprehensive gap assessment, strategic implementation planning, enhanced documentation development, and thorough assessment preparation. By leveraging the identical technical requirements between NIST SP 800-171 Rev 2 and CMMC Level 2, organizations can optimize their compliance investments while building sustainable competitive advantages in the Defense Industrial Base.
Organizations that successfully implement these frameworks experience multiple strategic benefits: improved overall security posture protecting against evolving cyber threats, significantly reduced risk of costly data breaches and security incidents, enhanced competitive positioning for defense contracts requiring cybersecurity certification, and streamlined preparation for future regulatory requirements and industry standards evolution.
Your Strategic Next Steps:
Conduct Comprehensive Assessment: Perform thorough NIST SP 800-171 Rev 2 gap assessment identifying implementation and documentation gaps.
Develop an Integrated Implementation Plan: Address both NIST and CMMC requirements through a coordinated approach.
Enhance Documentation Standards: Ensure documentation meets CMMC evidence expectations.
Prepare for Assessment Success: Conduct mock evaluations and systematic remediation verification.
Engage Expert Support: Leverage qualified expertise to accelerate complex implementation areas.
The future of defense cybersecurity compliance lies not in choosing between frameworks but in understanding how they work together to create comprehensive, verified protection for controlled, unclassified information. Organizations that successfully implement these frameworks experience improved security posture, reduced breach risk, and competitive advantage in the Defense Industrial Base.
Your competitive advantage depends on how strategically you leverage these insights for implementation success. Schedule a Consultation to begin your journey toward compliance excellence and sustained competitive advantage in defense contracting.
Key Takeaways
Complying with NIST SP 800-171 and CMMC is most effective when organizations treat NIST SP 800-171 as the cybersecurity foundation that prepares them for the verification and certification activities required by CMMC.
Understanding that NIST SP 800-171 provides detailed control requirements while CMMC focuses on formal assessment helps organizations avoid redundant work and make efficient progress toward certification.
Leveraging the overlap between the programs allows organizations to streamline documentation efforts, reduce workload, and build a consistent evidence base that supports both compliance and certification objectives.
A systematic compliance roadmap encourages organizations to define scope, assess current maturity, remediate gaps, and validate practices before undergoing formal assessment, strengthening both security and readiness.
Embedding dual compliance into risk management practices enhances organizational resilience by reducing vulnerabilities and reinforcing governance structures that align with defense contracting expectations.
Approaching compliance and certification as ongoing, strategic processes rather than one-time tasks positions organizations to adapt to future regulatory shifts and sustain long-term cybersecurity maturity.
How databrackets can help you on your
NIST SP 800-171 & CMMC Journey
databrackets is an authorized C3PAO and independent consulting organization for CMMC. We offer Certification OR Readiness and Consulting services for CMMC. To avoid a conflict of interest and abide by CMMC’s independence requirements, we do not offer both services to the same client.
We are an ideal partner for either service since we bring over 15 years of proven expertise in helping organizations achieve compliance or certification with the most rigorous cybersecurity and data privacy standards, including ISO 27001, SOC 2, HIPAA, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, and CMMC. We are an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
Schedule a Consultation to work with us as your Compliance partner for NIST SP 800-171, your C3PAO for CMMC Certification or as your Compliance Partner for CMMC.
A. Why Choose databrackets as your C3PAO
1. Proven Multi-Framework Expertise
What makes databrackets particularly valuable is our extensive experience across complementary frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and NIST Cybersecurity Framework. We are also an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
This breadth of knowledge enables our assessment teams to understand how CMMC controls integrate with your existing compliance efforts and identify synergies that strengthen your overall security posture.
2. Technical Environment Proficiency
databrackets’ assessment team of CCAs and CCPs has the specialized technical competence essential for accurate CMMC evaluations. Our experience spans diverse technological environments, from traditional on-premises infrastructures to complex cloud deployments, ensuring we can effectively assess whatever technical landscape your organization operates in.
3. Strategic Timeline Management
With proven capability in managing sophisticated assessments spanning the typical 4–8-week timeframe, databrackets understands how to minimize disruption to your operations while ensuring comprehensive evaluation of all 110 NIST SP 800-171 security controls.
As a authorized C3PAO with extensive cybersecurity and compliance experience, databrackets offers a deep understanding of the CMMC assessment process. This comprehensive expertise enables us to conduct thorough assessments with clear explanations of findings and methodologies, resulting in more insightful evaluations for organizations seeking certification.
To inquire about our C3PAO Services, contact our team at sales@databrackets.com or schedule a free consultation.
B. Why Choose databrackets for Your CMMC Compliance Journey
We specialize in transforming CMMC compliance from a daunting obstacle into a strategic business enabler.
Proven Track Record: Over 14 years supporting organizations across diverse industries with complex compliance requirements
Comprehensive Approach: End-to-end support from initial assessment through ongoing compliance
Industry Recognition: Authorized certifying body for ISO 27001 and 3PAO for FedRAMP
Strategic Partnership: We don’t just help you achieve compliance—we help you leverage it for competitive advantage.
Our Comprehensive CMMC Compliance Services include:
1. Strategic Planning & Assessment:
CMMC readiness assessments and comprehensive gap analysis
CUI system boundary definition and scoping guidance
Network architecture documentation and CUI flow diagrams
Risk assessment and vendor compliance evaluations
2. Implementation & Documentation Support:
System Security Plan (SSP) development and customization
Complete policy and procedure documentation suite
FIPS validation documentation and shared control matrices
Evidence collection strategies and management systems
3. Assessment Preparation:
Mock assessments and readiness validation
CMMC documentation optimization and organization
Personnel training and assessment preparation
C3PAO coordination and selection support
4. Ongoing Compliance:
Continuous monitoring and compliance maintenance
Annual affirmation support and triennial assessment preparation
Change management and configuration control guidance
Customized CUI awareness training programs
For immediate assistance with your CMMC compliance journey, contact our certified experts at sales@databrackets.com or schedule a free consultation.
Helpful Resources:
Summary
To summarize,
This blog outlines how organizations can achieve both NIST SP 800-171 compliance and CMMC certification by understanding the relationship between the two frameworks and aligning their efforts accordingly.
It explains that NIST SP 800-171 provides detailed cybersecurity controls that serve as the foundation for satisfying requirements embedded within CMMC, reducing duplication of effort when both are needed.
The discussion highlights the importance of establishing a structured compliance process that begins with scoping and assessment of current practices, followed by targeted remediation to close gaps relative to the required control set.
Documentation plays a central role in demonstrating readiness and supporting assessment activities, making clear, accurate, and maintainable records essential to both compliance and certification goals.
The blog emphasizes that organizations should validate implemented practices internally and through experienced partners before entering formal evaluation, helping reduce unexpected findings during assessment.
It reinforces that treating compliance and certification as ongoing risk management disciplines, rather than one-time projects, positions organizations to maintain cybersecurity maturity and adapt to evolving requirements over time.
Srini Kolathur
Srini is the Director of databrackets.com. He is a results-driven security and compliance professional with over 25 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, CMMC, FedRAMP, NIST Security Standards, HIPAA, Security Risk Assessments, among others. His accreditations include Certified CMMC Assessor, CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE. He has verified all the technical information in this blog and co-authored it with Aditi Salhotra.