For many cybersecurity frameworks you’ve dealt with, self-attestation is acceptable and gaps may be justified with Plans of Action and Milestones. However, CMMC Level 2 flips the script entirely. There’s no room for “we’re working on it” or “it’s in our roadmap,” and even a POA&M is only permitted for selected controls. In CMMC, every control must be implemented, every gap must be closed before a contract is awarded, and the decision lies entirely in the hands of an independent third party who’s never worked with your organization before. So how do you select the right C3PAO for your organization?
What Makes C3PAOs Unique
C3PAOs serve as the independent gatekeepers of CMMC certification, holding exclusive authority from DIBCAC and CyberAB to validate cybersecurity implementations across the defense industrial base for CMMC Level 2. These specialized organizations undergo rigorous accreditation to earn DoD trust and determine whether contractors can compete for defense contracts.
They operate under strict independence requirements that set them apart from typical cybersecurity consultants. They cannot provide consulting services to organizations they assess, preventing conflicts of interest and ensuring their findings reflect genuine organizational capabilities. This independence imperative means you’ll need separate partners for preparation and assessment—a reality that smart organizations plan for early.
The current landscape reveals a striking imbalance: Less than 100 authorized C3PAOs exist to serve approximately 77,000 Defense Industrial Base companies that require CMMC Level 2 certification. This scarcity means that selecting the right C3PAO isn’t just about finding any available assessor—it’s about strategic partnership planning.
The authorization process for C3PAOs is intentionally rigorous. Organizations must be 100% U.S. citizen-owned, achieve CMMC Level 2 compliance themselves, pass organizational background checks, and maintain specific insurance coverage. They must also employ certified professionals, including CMMC Certified Assessors (CCAs), Lead CCAs, and CMMC Certified Professionals (CCPs) who undergo extensive background investigations. These professionals also have specific roles and are required to have years of experience in cybersecurity before undergoing their CyberAB authorized training and certification. CCAs and Lead CCAs also require other certifications in cybersecurity to qualify as CMMC Assessors.
Understanding C3PAO Assessment Teams and Deliverables
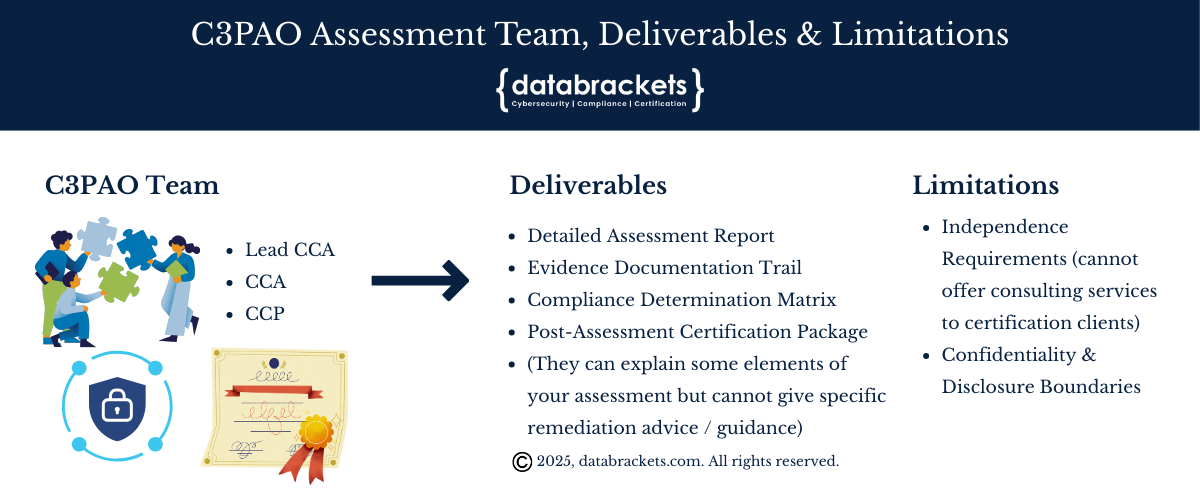
CMMC Certification Assessment Team Structure: C3PAOs deploy carefully structured assessment teams designed to ensure comprehensive evaluation across all CMMC domains. The core team typically includes:
1. Lead Certified CMMC Assessor (Lead CCA): Serves as the primary point of contact and holds ultimate responsibility for assessment methodology, team coordination, and final determinations. Lead CCAs must possess extensive cybersecurity experience, advanced certifications like CISSP or CISM, and undergo rigorous CyberAB training and background investigations.
2. Certified CMMC Assessors (CCAs): Conduct detailed technical evaluations of specific control families and domains. These professionals bring specialized expertise in areas such as access control, incident response, system security, and risk management. Each CCA must demonstrate years of hands-on cybersecurity experience before qualifying for CyberAB certification.
3. Certified CMMC Professionals (CCPs): Support the assessment process through documentation review, interview facilitation, and evidence collection. CCPs often specialize in specific technical environments or industry verticals, ensuring the team can effectively evaluate your unique technological landscape.
C3PAO Assessment Deliverables
The assessment process culminates in comprehensive documentation that becomes part of your permanent CMMC certification record:
1. Detailed Assessment Report: A thorough document examining each of the 110 NIST 800-171 security controls, providing specific findings, evidence reviewed, and compliance determinations. This report must withstand scrutiny from DoD procurement officials and serve as the foundation for certification decisions.
2. Evidence Documentation Trail: Systematic recording of all evidence examined during the assessment, including technical configurations, policy implementations, interview summaries, and supporting artifacts. This creates an auditable trail of professional assessment judgment that validates each compliance determination.
3. Compliance Determination Matrix: A comprehensive mapping of your organization’s implementation status for each required control, clearly identifying areas of full compliance, partial implementation, and any gaps that must be addressed before certification.
4. Post-Assessment Certification Package: Final documentation package submitted to CyberAB that includes assessment findings, C3PAO recommendations, and all supporting evidence necessary for official CMMC certification approval.
Confidentiality and Disclosure Boundaries for C3PAO
C3PAOs operate under strict confidentiality requirements that govern what information they can share and with whom:
What C3PAOs Must Protect: All assessment-related information, including your organization’s security configurations, documentation, interview responses, and internal processes, is considered confidential. C3PAOs cannot share specific details about your cybersecurity posture, implementation approaches, or assessment findings with other clients or unauthorized parties.
Permitted Disclosures: C3PAOs may only share assessment outcomes and certification recommendations with authorized CyberAB officials and as required by regulation, with relevant DoD procurement officials. They cannot provide advanced information about assessment results to anyone not directly assigned to your specific assessment.
Prohibited Information Sharing: C3PAOs are strictly forbidden from discussing your assessment details with competitors, potential clients, or using your assessment experience as marketing material without explicit written consent. They cannot share lessons learned from your assessment with other organizations, even in anonymized formats.
Can C3PAOs Explain Their Recommendations?
Yes, C3PAOs are allowed and expected to explain their findings clearly and provide clear communication throughout the assessment process. However, there are strict limitations on what they can explain.
What C3PAOs CAN Explain:
Why specific practices were scored as MET or NOT MET
What evidence was insufficient or missing
Which controls are critical vs. non-critical
Assessment methodology and scoring rationale
What C3PAOs CANNOT Provide:
Specific remediation advice or guidance on how to fix deficiencies
Implementation recommendations for failed controls
Consulting services on how to resolve issues that disqualified certification
POA&M (Plan of Action & Milestones) Role: C3PAOs can
Identify which controls are eligible for POA&M placement
Explain the POA&M process and 180-day remediation timeline
Describe critical vs. non-critical control distinctions
Cannot provide: Specific remediation strategies or implementation guidance
Timeline: 4-8 weeks for complete assessment activities
Post-Certification Maintenance Requirements: CMMC certification requires ongoing maintenance for two years following initial certification. Organizations must maintain their security posture and may be subject to annual compliance monitoring activities. This ongoing relationship makes C3PAO selection even more critical, as you’ll need a partner capable of supporting long-term compliance verification and potential reassessment activities.
Considerations for Risk Mitigation
C3PAO Unavailability: Given the limited number of authorized C3PAOs and potential market constraints, organizations should develop contingency plans
Primary Mitigation Approach: Identify and pre-qualify 2-3 suitable C3PAOs during your selection process. Maintain relationships with backup options even after selecting your primary assessor.
Contractual Protections: Include service level agreements and availability commitments in your C3PAO contracts. Negotiate clear timelines and backup assessor provisions in case of unexpected unavailability.
Early Warning System: Monitor your chosen C3PAO’s capacity and schedule changes. Maintain regular communication about upcoming assessment needs to identify potential conflicts early.
Market Intelligence: Stay informed about the C3PAO landscape through industry associations and peer networks. New C3PAOs continue entering the market, potentially providing additional options during critical periods.
These deliverables represent more than administrative requirements—they become the permanent record of your organization’s cybersecurity maturity and the basis for ongoing compliance monitoring throughout your certification period.
Critical Selection Criteria for C3PAOs
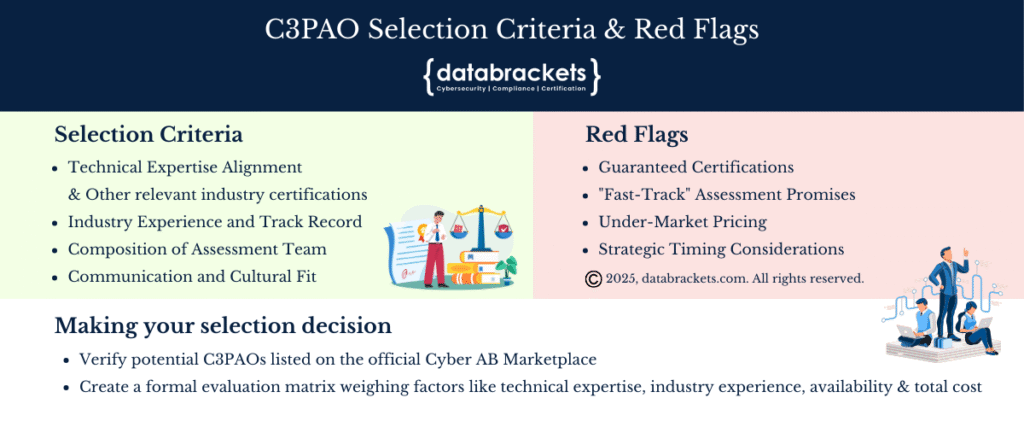
These are the critical selection criteria for C3PAOs
Technical Expertise Alignment: Your C3PAO’s technical competence should match your technological environment. If your organization uses specialized technologies like SQL databases, load balancers, or specific cloud environments like Microsoft GCC-High or Amazon GovCloud, ensure your assessment team includes specialists with proven experience in those areas. Ask direct questions: Does the assessment team hold relevant industry certifications? How many similar technical environments have they assessed?
Industry Experience and Track Record: While all authorized C3PAOs meet baseline requirements, their practical experience varies significantly. Look for organizations with proven track records with frameworks like NIST 800-171, FedRAMP, and ISO 27001. Organizations with longer operational histories often bring institutional knowledge that transcends individual assessors.
Composition of Assessment Team: Understanding who will actually conduct your assessment is crucial. Many C3PAOs rely on contracted CCAs and CCPs rather than full-time employees. While this model can work well, ensure the team has worked together before and understands the continuity of personnel throughout your assessment period.
Communication and Cultural Fit: CMMC regulations are complex and highly technical, making clear communication essential. Choose an assessor who explains processes and terminology clearly and patiently, particularly when determining your required maturity level. The assessment process can be stressful enough without communication barriers.
Red Flags to Avoid
Guaranteed Certifications: Beware of companies offering “guaranteed” CMMC certifications before the official process is completed. No legitimate C3PAO can guarantee certification outcomes, as assessments must evaluate actual implemented controls against objective standards.
“Fast-Track” Assessment Promises: You need to maintain a distance from any C3PAO promising to complete your certification assessment in just a few days or claiming they can “rush” the process. Legitimate CMMC Level 2 assessments are comprehensive evaluations that typically require weeks, not days. A proper assessment involves examining 110 security controls, conducting interviews across your organization, reviewing extensive documentation, and performing technical validation. C3PAOs who promise unrealistic timelines either don’t understand the assessment requirements or plan to cut corners that could jeopardize your certification validity.
Under-Market Pricing: Be cautious of budget C3PAOs offering assessments for under-market value. As with most professional services, you typically get what you pay for. Extremely low pricing may indicate shortcuts in assessment thoroughness or assessor qualifications.
Strategic Timing Considerations: The current market dynamics strongly favor early engagement. Assessment costs may be influenced by “supply and demand” factors, suggesting that getting ready for CMMC certification sooner rather than later could help save money. The limited number of authorized C3PAOs relative to demand means preferred assessment slots are becoming increasingly competitive.
Your Strategy: Since C3PAOs cannot provide remediation consulting, successful organizations develop relationships with both preparation partners and assessment organizations early in their CMMC journey.
Making Your C3PAO Selection Decision: Start by verifying potential C3PAOs are listed on the official Cyber AB Marketplace and look for proper accreditation credentials. Use the marketplace filters to select ‘C3PAO’ under ‘Ecosystem Role’ and ‘Assessment Services’ under ‘Scope of Services’, then refine based on experience level and geographical location.
Consider creating a formal evaluation matrix weighing factors like technical expertise, industry experience, communication quality, availability, and total cost. Remember that the cheapest option is rarely the best value when your ability to compete for defense contracts hangs in the balance.
The Path Forward
Selecting the right C3PAO represents a strategic business decision that extends far beyond vendor selection. Your choice impacts not just certification success, but the quality of insights you’ll gain about your cybersecurity posture and the efficiency of your assessment experience.
The CMMC ecosystem continues evolving as more organizations achieve authorization, and assessment demand grows. Organizations that approach C3PAO selection strategically—understanding the landscape, evaluating carefully, and engaging early—position themselves for smoother certification experiences and stronger competitive positioning in defense procurement.
The stakes are too high and the market too constrained for anything less than a thoughtful, strategic approach to C3PAO selection. Your organization’s future in defense contracting may well depend on getting this choice right.
Key Takeaways
Certified Third-Party Assessor Organizations (C3PAOs) play a central role in the CMMC certification process by serving as the independent entities authorized to validate whether an organization meets the required cybersecurity maturity level.
C3PAOs must remain impartial and cannot provide consulting services to the same organizations they assess, requiring organizations to plan for separate preparation and assessment partners early in their compliance journey.
Selecting the right C3PAO involves evaluating their technical expertise, industry experience, and communication approach to ensure alignment with your organization’s technology stack and maturity requirements.
It’s important to recognize common red flags when evaluating C3PAOs, such as promises of guaranteed certification or lack of demonstrable assessment experience, which can undermine trust and increase risk during the certification process.
Engaging a C3PAO with a proven track record and clear assessment methodology can improve clarity, reduce uncertainty, and support a smoother certification experience.
Organizations benefit from maintaining awareness of the evolving C3PAO marketplace and considering how assessor capabilities, responsiveness, and fit with organizational culture will impact both short-term assessment success and long-term compliance posture.
Why databrackets is an ideal C3PAO
databrackets is an authorized C3PAO with 15 years of cybersecurity and compliance expertise. Our experience with frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and the NIST cybersecurity framework, etc., makes us an ideal choice. We are also a 3PAO for FedRAMP and accredited as a Certifying Body for ISO 27001.
1. Proven Multi-Framework Expertise
What makes databrackets particularly valuable is our extensive experience across complementary frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and NIST Cybersecurity Framework. We are also a 3PAO for FedRAMP and accredited as a Certifying Body for ISO 27001.
This breadth of knowledge enables our assessment teams to understand how CMMC controls integrate with your existing compliance efforts and identify synergies that strengthen your overall security posture.
2. Technical Environment Proficiency
databrackets’ assessment team of CCAs and CCPs has the specialized technical competence essential for accurate CMMC evaluations. Our experience spans diverse technological environments, from traditional on-premises infrastructures to complex cloud deployments, ensuring we can effectively assess whatever technical landscape your organization operates in.
3. Strategic Timeline Management
With proven capability in managing sophisticated assessments spanning the typical 4–8-week timeframe, databrackets understands how to minimize disruption to your operations while ensuring comprehensive evaluation of all 110 NIST SP 800-171 security controls.
As a authorized C3PAO with extensive cybersecurity and compliance experience, databrackets offers a deep understanding of the CMMC assessment process. This comprehensive expertise enables us to conduct thorough assessments with clear explanations of findings and methodologies, resulting in more insightful evaluations for organizations seeking certification.
Helpful Resources:
Summary
To summarize,
Selecting the right C3PAO is a pivotal step in preparing for your CMMC certification because C3PAOs serve as the independent assessors whose evaluations determine whether an organization meets its targeted maturity level.
C3PAOs must maintain impartiality and cannot provide both readiness consulting and assessment services to the same organization, making it important for organizations to plan their preparation and assessment partnerships separately.
A thoughtful selection process considers how well a C3PAO’s expertise, communication style, and approach to assessment align with an organization’s technology, industry context, and maturity objectives.
Being aware of common red flags, such as guarantees of certification or inconsistent assessment methodologies, helps organizations avoid misalignment and potential setbacks during the certification process.
Engaging a C3PAO with a proven track record and clear methodology can support a smoother and more predictable certification experience by reducing uncertainty and improving the quality of feedback.
Organizations benefit from maintaining an understanding of the evolving C3PAO landscape and considering how assessor capabilities will impact both immediate certification outcomes and longer-term compliance posture.
Srini Kolathur
Srini is the Director of databrackets.com. He is a results-driven security and compliance professional with over 25 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, CMMC, FedRAMP, NIST Security Standards, HIPAA, Security Risk Assessments, among others. His accreditations include Certified CMMC Assessor, CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE. He has verified all the technical information in this blog and co-authored it with Aditi Salhotra.