 Organizations of all sizes are vulnerable to data theft and loss. Vulnerability is regardless of the asset at risk – consumer information, intellectual property, or private corporate files. The United States federal government and its commercial contractors have long relied on the National Institute of Standards and Technology (NIST) to provide information security standards and recommendations. This blog will analyze NIST security standards and compliance to help improve your cybersecurity program.
Organizations of all sizes are vulnerable to data theft and loss. Vulnerability is regardless of the asset at risk – consumer information, intellectual property, or private corporate files. The United States federal government and its commercial contractors have long relied on the National Institute of Standards and Technology (NIST) to provide information security standards and recommendations. This blog will analyze NIST security standards and compliance to help improve your cybersecurity program.
NIST creates information security standards and guidelines, including minimum requirements for federal systems. However, such standards and procedures shall not apply to national security systems without the express approval of relevant federal officials exercising policy authority over such systems.
NIST compliance is essentially meeting the requirements of one or more NIST standards. The organization’s principal function is to provide guidelines (especially for security controls) applicable to various businesses and agencies. NIST is releasing several security standards widely used worldwide in response to the rising demand in the security sector.
Although NIST has been active for some time, the NIST CSF (Cybersecurity Framework) was born out of the 2014 Cybersecurity Enhancement Act passed in December of that year. The NIST Cybersecurity Framework (CSF) is one of their most popular security standards. This widely accepted framework provides organizations with guidance to help organizations manage cybersecurity risk.
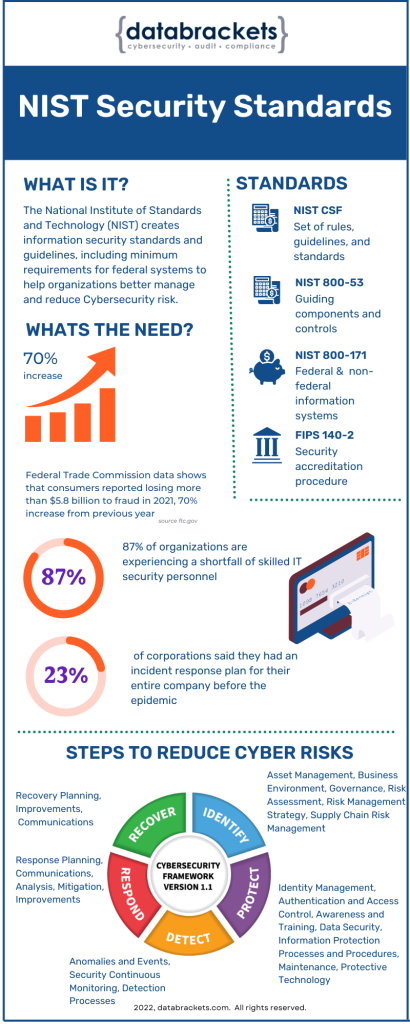
What Are NIST Security Standards?
Businesses increasingly realize that network security requirements are a vital component of a contemporary organization and critical to its survival.
According to IBM, only 23% of corporations said they had an incident response plan for their entire company before the pandemic, indicating that businesses were unprepared for cyberattacks.
Cyberattacks are now more common than ever due to the pandemic. Businesses must act to safeguard themselves and their customers.
Companies are searching for direction in their cybersecurity and are hoping that frameworks like NIST can deliver it.
What Is NIST?
The National Bureau of Standards, as it was known until 1988, was established in 1901 as a non-regulatory organization. The main aim was to produce standards in a variety of fields. This included manufacturing, environmental research, public safety, nanotechnology, information technology, and others.
Since its inception, NIST’s mandate has expanded to include an increasing number of businesses, including cybersecurity (under IT). NIST standards, particularly their cybersecurity framework, are meant to be voluntary guidelines for all organizations, with the exception of those engaged in government contracts, which must follow them.
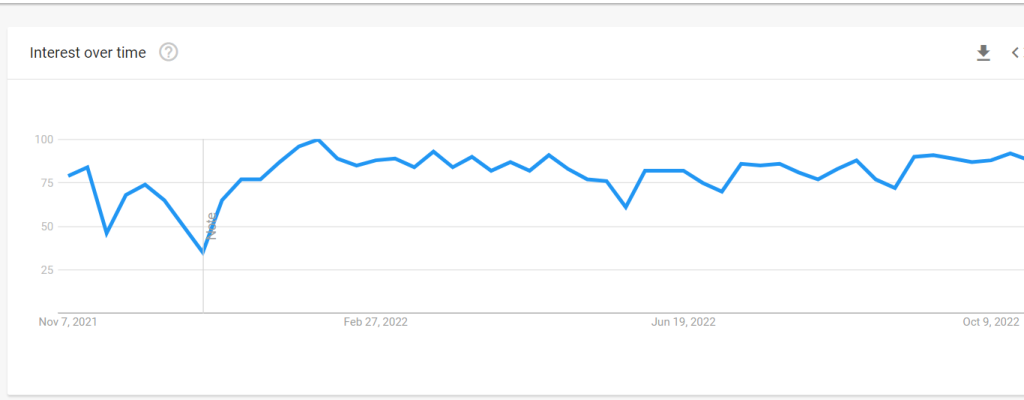
‘NIST’ has reached the highest search interest in August-September ’22 since February ’22, edging towards an all-time high on Google Search in the U.S. This is mainly due to its convening requirement to create a risk-based approach for organizations to improve their security posture.
Key NIST Security Standards
NIST CSF
The NIST Cybersecurity Framework (NIST CSF) is the benchmark for designing a cybersecurity program. This framework, developed by the National Institute of Standards and Technology, tackles the absence of standards in cybersecurity by providing a consistent set of rules, guidelines, and standards for enterprises to adopt across the board.
The NIST cybersecurity framework effectively organizes and develops an organization’s cybersecurity program. It is a set of guidelines and best practices designed to assist organizations in developing and improving cybersecurity posture. The framework proposes a series of suggestions and standards to help your organization better prepare to recognize and detect cyber-attacks and rules for responding to, preventing, and recovering from cyber disasters.
The NIST CSF specifies your organization’s security procedures to protect digital assets from unwanted access. It does not create new security requirements or solutions that organizations must implement. Rather, the framework provides organizations with the best cybersecurity practices.
These practices are the five basic functions listed below:
Identify: Raise awareness within your organization about the need to manage cybersecurity risk. Then, determine the systems and data needed to safeguard your organization.
Protect: Put in place security measures to protect your systems and data from attackers. These steps may include cybersecurity solutions, organization-wide security policy, and data management training for staff.
Detect: Good cybersecurity necessitates increased visibility into enterprise networks, systems, and devices—a well-planned cybersecurity strategy, including protocols and tools for detecting cybersecurity incidents.
Respond: Create crisis plans to eliminate threats and quickly mitigate harm.
Recover: Implement a disaster recovery policy to restore data and services disrupted by your cyberattack, learn and grow from every cybersecurity event, and communicate your findings throughout your organization.
The framework also offers four tiers for assessing an organization’s cybersecurity posture.
Tier 1 – Partial: The organization does not adhere to a minimum cybersecurity requirement and does not have a written security plan. Cybersecurity measures are frequently improvised and established in response to a previous occurrence.
Tier 2 – Risk-informed: Although there are no organizational-wide cybersecurity safeguards, the organization is aware of cyber supply chain threats. Some cybersecurity measures are in place but not implemented at all levels of the business.
Tier 3 – Repetitive: The firm formalizes implementing a company-wide cybersecurity policy, which is reviewed and modified to reflect the ever-changing technological world.
Tier 4 – Adaptable: The organization’s cybersecurity policy is constantly adjusted to line with industry standards and developing technology.
NIST 800-53
The National Institute of Standards and Technology created the NIST 800-53 standard and compliance framework for cybersecurity. An ongoing framework seeks to dynamically develop standards, controls, and evaluations by risk, cost-effectiveness, and capabilities.
The NIST 800-53 framework offers a base of guiding components, strategies, systems, and controls that can neutrally support any organization’s cybersecurity needs and priorities.
NIST 800-171
The NIST 800-171 document specifies how federal contractors and subcontractors should maintain Controlled Unclassified Information (CUI). It is also intended for non-federal information systems and organizations.
Executive Order 13556, signed by President Obama in 2010, mandated that all federal agencies in the United States preserve CUI more stringently. Following several high-profile breaches of government entities, the federal government increased its focus on cybersecurity. The goal was to create a consistent strategy for data sharing and transparency that calls for adherence by all agencies.
As a result, the Federal Information Security Modernization Act (FISMA) was passed in 2014, followed by NIST 800-53 and NIST 800-171 in 2017. Since then, various iterations and upgrades to NIST 800-171 have been released to keep CUI safe inside the government contractor ecosystem.
FIPS 140-2
The Federal Information Processing Standard 140-2 (FIPS 140-2) is an information technology security accreditation procedure that verifies that private-sector cryptographic modules meet well-defined security standards.
Other standards
Firms not subcontracted by a government contractor or employed directly by the government do not require NIST CSF compliance. However, many of its procedures and activities apply to other laws that require compliance, including HIPAA, PCI, and PII.
NIST Compliance for Federal Agencies
All organizations conducting business with the federal government, including academic institutions that receive federal funds, must conform to the NIST criteria to qualify for government contracts.
Anyone processing, storing, or transmitting potentially sensitive information for the Department of Defense (DoD), General Services Administration (GSA), NASA, or other federal or state agencies must adhere to NIST compliance guidelines.
Executive Order 13800 made the CSF mandatory for all federal entities in the United States. However, compliance with the NIST CSF is optional for commercial firms, while many private sector organizations prefer to employ these standards, which are routinely updated to combat changing cybersecurity threats.
NIST Compliance for the Private Sector
Compliance with NIST standards is optional for private-sector companies that do not compete for government contracts. Nonetheless, adopting NIST standards has various advantages that make the proposal well worth exploring.
The flexible nature of the NIST cybersecurity framework can be highly valuable when an organization is attempting to chart its path to better protecting its critical infrastructure, implementing effective security measures, and reducing the risk of cyber assaults.
If you follow NIST principles, you don’t have to start from scratch when designing your cybersecurity strategy. Adopting NIST shows that your company is serious about data security and developing robust security procedures.
If you answered yes to any of the following questions, NIST compliance is a good next step for your company:
Do you handle HIPAA-compliant data?
Do you manage regulated, unclassified information regularly?
Do you have a large number of third-party vendors and contractors?
Will you ever compete for a contract with the United States government?
Do you want to work as a service provider or a small company contractor in national security?
Do you work on projects adhering to the Federal Information Security Management Act (FISMA)?
Seeking NIST compliance does not have to be as difficult and time-consuming as it may appear. NIST compliance criteria have become industry standards, particularly for mitigating cybersecurity risks such as data breaches. As the COVID-19 outbreak subsides and the organization resumes normal operations, databrackets can assist you in remaining competitive.
Comparing NIST with other standards
Compliance standards and frameworks such as NIST CSF, ISO 27001, and SOC2 guarantee the integrity and protection of your organization’s data as well as the data of your customers.
However, these regulations are not similar, and it’s not always clear which one applies to your company. To determine which is ideal for you, let’s compare these frameworks. To know more, please visit our blog
Cost of complying with NIST security standards
Organizations often spend between $5,000 and $15,000 to be assessed for NIST compliance. If problems that need to be fixed are discovered during the examination, they can cost between $35,000 and $115,000 to remedy.
How databrackets can help you comply with NIST security regulations?
We offer an A2LA-accredited comprehensive suite of self-assessment and consulting services to help you navigate the NIST Cybersecurity framework requirements.
We have compared well-known security frameworks and standards with the help of our partners and consultants. Our analysis and assessment focus on practical elements you should consider before implementing the controls in place for each framework.
For more information, get in touch with our specialist to learn how databrackets can put your organization’s compliance in order right away.