Security Operations Center – SOC
Security Operations Center is a centralized unit that monitors, detects, and responds to cybersecurity incidents using a combination of technology solutions and a strong set of processes to safeguard your organization from emerging cyber threats.
SOC-as-a-Service
The team within an organization responsible for detecting, preventing, investigating, and responding to cyber threats is known as a Security Operations Center (SOC). A SOC should monitor an organization’s network 24 hours a day, 7 days a week, and address potential threats to sensitive data, computing systems, and other digital assets.
Gartner recently identified a burgeoning cybersecurity market known as managed detection and response (MDR). It is critical to identify threats but be prescriptive, and a SOC must also supply incident response (IR). This includes the collection and analysis of data to identify suspicious activity and improve the organization’s security. Threat data is collected from firewalls, intrusion detection systems, intrusion prevention systems, security information and event management (SIEM) systems, and threat intel. SOC also initiates the incident response process and manages and owns the threat management activities, such as alert validation, incident detection and response, incident impact assessment, vulnerability management, threat detection, and hunting.

The Working of Security Operations Center
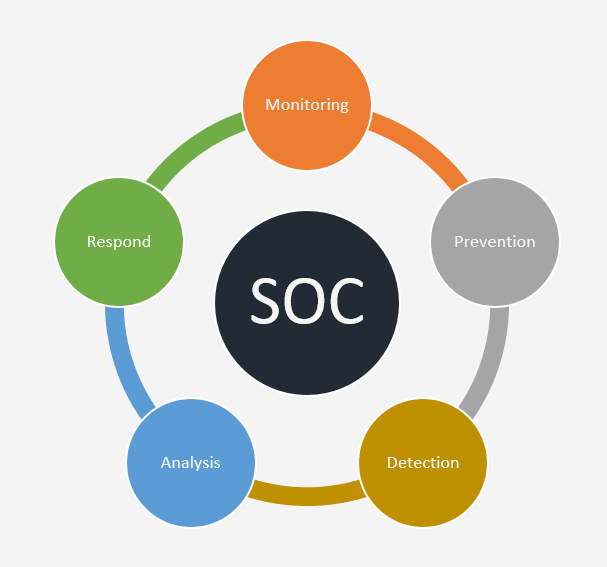
The goal of SOC is to monitor, prevent, detect, analyze and respond to Cybersecurity incidents.
Monitoring
SOC uses tools that can scan the network 24/7 to flag any abnormalities or suspicious activities. Monitoring the network 24/7 helps notify threats immediately, giving them the best chance to prevent or mitigate harm. Monitoring tools can include a SIEM or an EDR, the most advanced of which can use behavioral analysis to “teach” systems the difference between regular day-to-day operations and actual threat behavior, minimizing the amount of triage and analysis done by humans.
Prevention
Preventing Cybersecurity attacks is more important when we have a dedicated function in place. This step includes tasks implemented to make successful attacks more difficult, including regularly maintaining and updating existing systems, updating firewall policies, patching vulnerabilities, whitelisting, blocklisting, and securing applications.
Detection
In spite of implementing threat prevention techniques, cyber threat attacks may occur. Detecting the same as soon as they emerge is a key task of a SOC. As soon as an incident is confirmed, the SOC acts as the first responder. The incidents are further analyzed and prioritized.
Analysis
When monitoring tools issue alerts, it is the responsibility of the SOC to look closely at each one, discard any false positives, and determine how aggressive any actual threats are and what they could be targeting. This allows them to triage emerging threats appropriately, handling the most urgent issues first.
Respond
SOC initiates actions like shutting down or isolating endpoints, terminating harmful processes, deleting files, and more. The goal is to respond to the extent necessary to minimize the impact on the business. SOC will work to restore systems and recover any lost or compromised data. In the case of ransomware attacks, viable backups are restored to circumvent the ransomware.
Interested in learning more?
Benefits of having a Security Operations Center
- Real-Time Monitoring – Adversaries don’t work have business hours. So, 24/7 monitoring is a must to secure your system. SOC monitoring around the clock keeps the threat radar circulating, hunting out advanced TTPs (Tactic, Techniques & Procedures) to malicious hosts, networks, and cloud artifacts – before a breach occurs.
- Log management and Storage Retention – SOC use software tools that allow IT organizations to monitor their security posture using log files, detect and respond to Indicators of Compromise (IoC) and conduct forensic data analysis and investigations into network events and possible attacks.
- Proactive Threat Hunting – Cutting-edge, criminal hacking tactics are increasingly difficult to detect, which means that network configurations need to be continually adjusted based on the newest and wiliest cyberthreats. SOC plays a major role in adapting to the new technologies and still hunts for threats evaded through traditional methods. This involves the use of relevant threat-intelligence sources, applying machine learning and user behavior analytics, and keep watching in search for real security incidents that impact customers
- Reduce Dwell Time & Financial Impact – Dwell time is the period an attacker goes undetected on the network after initial access has occurred. Each minute an attacker dwells inside of the network, the greater the potential for damage. SOC plays a vital role here by reducing the dwell time and the financial impact it can cause.
- Strategic Consulting – The first step in establishing an organization’s SOC is defining a strategy that incorporates business-specific goals.
- Compliance Management – A SOC must be expected to operate with the utmost regard for compliance, whether HIPAA, HITECH, PCI DSS, FFIEC, GLBA, or any other standards to which highly regulated industries must conform.
- Reduce Cybersecurity Headcount Costs – Finding skilled candidates and hiring internally for most cyber-related positions is a difficult task due to the lack of security professionals available for hire. Partnering with a SOC enables your business immediate access to security expertise without the financial burden of hiring internally.
- Remote Home Worker Threat Coverage – As the number of remote home workers increases, the likelihood of more cyber security threats also increases. With SOC, the coverage of such threats coming from a greater network perimeter is also possible

Why databrackets?

databrackets is the leading provider of security and compliance solutions. The company offers a wide range of security solutions to SMEs, MSPs, and various industries. Cloud-based Security Operations Centre (SOC) delivers 24/7 advanced, next-generation managed threat detection to detect, analyze, and respond to cybersecurity incidents using a combination of technology solutions and a strong set of processes to safeguard your organization from emerging cyber threats.
Our Security Operations Center (SOC) is pivoted on advanced technology innovations and a highly skilled team that operates round-the-clock. Together, they work cohesively to monitor, prevent, detect, analyze and respond to cyber security incidents. The solution provides various capabilities, including MDR, SIEM, behavioral analytics, real-time alerting, log analysis with machine learning and AI.
The company’s pay-as-you-go business model would help organizations obtain security and compliance management solutions and services as per their requirements.