Organizations frequently face a tough choice between SOC 2 and ISO 27001 certifications as a means to showcase their security maturity. Comparing the two security standards can be tough and the decision-making process can be complex, as each certification brings its own set of advantages and challenges. As certified security experts who regularly work with both frameworks, we will discuss details about each security standard to help you make an informed choice that aligns with your business objectives, industry standards, and the risk tolerance demanded by your customers.
What is SOC 2?
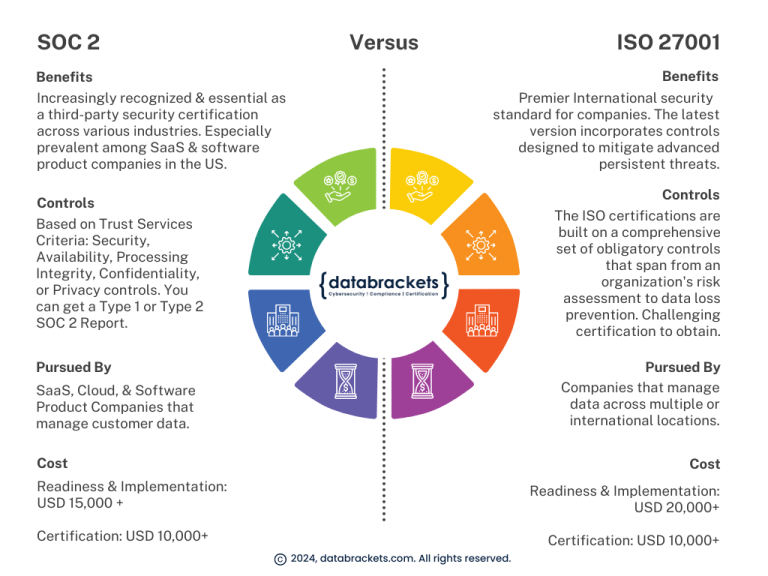
SOC 2 (System and Organization Controls 2) is a security standard for service organizations, developed by the American Institute of CPAs (AICPA). The SOC 2 framework is applicable to all technology service providers or SaaS Product companies that work with customer data. It specifies aspects of security that they need to follow while managing customer data.
SOC 2 Certification is based on 5 Trust Services Criteria: security, availability, processing integrity, confidentiality and privacy of customer data. The SOC 2 framework does not provide a specific list of controls and tools. It merely cites the criteria required to maintain a high level of information security. It is up to each organization to establish the practices and processes relevant to their own objectives and operations. A SOC 2 report provides detailed information about the controls and processes in place, along with an auditor’s opinion on their effectiveness.
What is ISO 27001?
ISO 27001 is a globally respected information security standard. It was designed, regulated and continues to be updated by the International Organization for Standardization. It is officially referred to as ‘ISO/IEC 27001’ and is part of the ISO/IEC 27000 family of standards.
Even though ISO 27001 isn’t a legal mandate, organizations around the world prefer to work with B2B partners and vendors who are ISO 27001 certified. Its popularity is attributed to the fact that ISO 27001 controls evaluate the strength of an organization’s Information Security Management System (ISMS) and the 2022 version is designed to prevent advanced persistent threats.
Comparing SOC 2 and ISO 27001
SOC 2 (System and Organization Controls 2) and ISO 27001 are two different frameworks B2B companies use for assessing the ISMS of potential vendors and partners. While they share some similarities, they also have distinct differences. Here’s a comparison of SOC 2 and ISO 27001 in terms of their similarities and differences.
Similarities between SOC 2 and ISO 27001
1. Information Security Focus:
Both SOC 2 and ISO 27001 are focused on information security management. They aim to ensure the confidentiality, integrity, and availability of sensitive data and systems.
2. Risk Management: Both frameworks emphasize the importance of identifying, assessing, and mitigating information security risks. They require organizations to have risk management processes in place.
3. Third-Party Audits:
Both SOC 2 and ISO 27001 certifications involve third-party audits conducted by independent auditors or certification bodies to verify compliance with their respective standards.
4. Control Objectives: Both frameworks provide a set of control objectives or requirements that organizations must meet to achieve certification. These control objectives address various aspects of information security.
5. Continuous Improvement:
Both SOC 2 and ISO 27001 promote a culture of continuous improvement by requiring organizations to regularly assess and update their security measures.
Differences between SOC 2 and ISO 27001
1. Scope
SOC 2: Primarily focuses on service organizations, particularly those that provide services to other businesses like SaaS providers. SOC 2 reports are often used by customers to evaluate the security of service providers.
ISO 27001: Can be applied to any type of organization, including service providers and manufacturing companies. It is not limited to service organizations.
2. Origin of the Framework
SOC 2: Developed by the American Institute of CPAs (AICPA) and is widely recognized in the United States.
ISO 27001: Developed by the International Organization for Standardization (ISO) and is an international standard recognized globally.
3. Certification versus Attestation
SOC 2: SOC 2 is not technically a certification; it is officially called a SOC 2 Examination. A SOC 2 Audit results in an attestation report, which provides information about the controls in place but does not result in certification. Organizations receive a SOC 2 Type 1 or Type 2 report.
ISO 27001: Results in certification, indicating that an organization’s Information Security Management System (ISMS) complies with the ISO 27001 standard. Organizations receive ISO 27001 certification.
4. Control Framework
SOC 2: It does not provide a specific control framework but relies on predefined trust service criteria (e.g., security, availability, processing integrity, confidentiality, and privacy) that organizations must address.
ISO 27001: Provides a comprehensive set of controls and control objectives which organizations have to implement.
5. Reporting Structure
SOC 2: Typically results in a Type 1 or Type 2 report that outlines the controls in place and their effectiveness during a specific period (Type 1 for a point in time, Type 2 for a period of time).
ISO 27001: Results in a certificate issued by a certification body indicating that an organization’s ISMS complies with ISO 27001. It does not provide specific details on individual control effectiveness.
6. Cost
SOC 2 : Readiness & Implementation Cost: Starting at $15,000 +
Certification Cost: Starting at $10,000 +
ISO 27001: Readiness & Implementation Cost: Starting at $20,000 +
Certification Cost: Starting at $10,000 +
7. Time
SOC 2: Readiness & Implementation: 3-4 months for SMBs, maybe longer for large enterprises
Certification: 3-6 months depending on the period of observation and 4-8 weeks subsequently for testing and reporting
ISO 27001: Readiness & Implementation: 3-4 months for SMBs, maybe longer for large enterprises
Certification: 3-6 weeks
In summary, both SOC 2 and ISO 27001 are valuable frameworks for managing information security, but they differ in terms of scope, origin, certification vs. attestation, control framework, and reporting structure. Organizations should choose the framework that aligns best with their specific needs, industry, and geographic considerations. Additionally, some organizations may choose to pursue both certifications to meet the needs of different stakeholders.
How databrackets can help you with SOC 2
databrackets works in conjunction with certified CPA firms to prepare our customers to get ready for a SOC 2 Examination and obtain a SOC 2 report. Some of the services by our security experts are:
Readiness Assessment & Recommendations
Testing of Controls, Vulnerability Assessment and Security Risk Assessment
Support to draft the Management Assertion for your SOC 2 Report
SOC 2 Examination by a certified CPA includes
Selecting the Trust Services Criteria
Finalizing the SOC 2 Audit Period
Scoping of the systems and applications
Sampling & reviewing the evidence and policies & procedures
Interviewing process owners
Analyzing the results
Documenting and reporting
The CPA that you chose to work with can access all your evidence in a streamlined manner on dbACE – our GRC Platform.
How databrackets can help you with ISO 27001
databrackets has a team of certified ISO Lead Auditors. We help organizations achieve their ISO goals by supporting them with:
ISO 27001 Certification
Do-It-Yourself ISO 27001 assessment toolkit
In our DIY (Do It Yourself) assessment toolkit all the clauses and controls stipulated by ISO 27001 standards are uploaded on our GRC Platform – dbACE. Customers need to upload their data along with evidence and mark the clause/controls’ ‘implementation’ status for Stage 1 and Stage 2 Assessments.
Our ISO Lead auditors conduct an impartial assessment based on the evidence provided and record their findings on dbACE. This helps them communicate the results and seek corrective measures wherever necessary – all in one location. The dbACE interface makes the turnaround quicker and saves time, effort and, thereby, costs. The documentation for the audit from start-to-finish takes place on this platform. This includes the final report that reflects the status of the customer’s adherence to ISO 27001 standards and guidelines.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Meeting if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Srini Kolathur
Srini is the Director of databrackets.com. He is a results-driven security and compliance professional with over 25 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, CMMC, FedRAMP, NIST Security Standards, HIPAA, Security Risk Assessments, among others. His accreditations include Certified CMMC Assessor, CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE. He has verified all the technical information in this blog and co-authored it with Aditi Salhotra.