 ISO 27001 is a globally respected information security standard. It is officially referred to as ‘ISO/IEC 27001’ and is part of the ISO/IEC 27000 family of standards for information security management. It is designed, updated and regulated by the International Organization for Standardization.
ISO 27001 is a globally respected information security standard. It is officially referred to as ‘ISO/IEC 27001’ and is part of the ISO/IEC 27000 family of standards for information security management. It is designed, updated and regulated by the International Organization for Standardization.
While ISO 27001 Certification is popular for the enhanced level of security it ensures in an organization’ Information Security Management System (ISMS), it is also preferred by Senior Management because of the contracts they can apply for with an ISO 27001 Certificate. Organizations around the world prefer to work with B2B partners and vendors who comply with ISO 27001 controls. They tend to include this certification or a proof of compliance in their RFQs / RFPs.
The latest ISO 27001 update in 2022 introduced several changes starting with the name. The current edition of this standard is now referred to as ‘ISO/IEC 27001:2022’. Organizations certified against the 2013 revision (the previous edition) have till Oct 21, 2025 to transition to the new update.
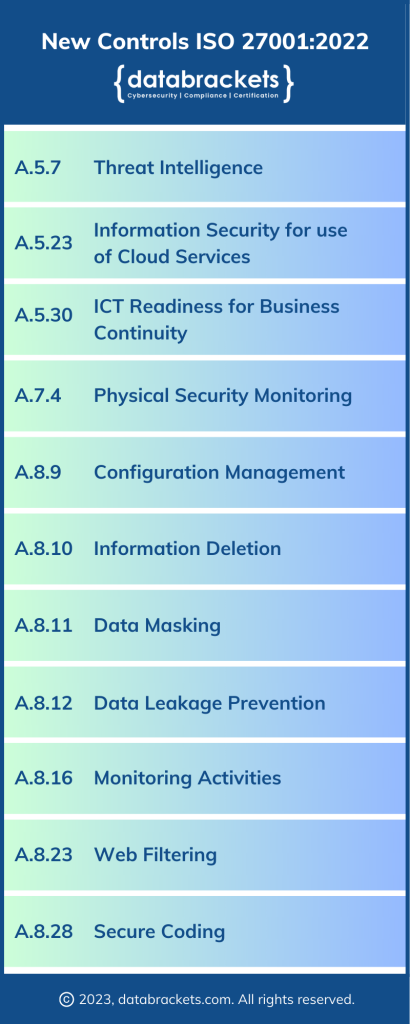
While the Structure of ISO 27001 has not changed, major changes have been introduced in Annex A, starting with the introduction of 11 new controls. Other changes include splitting one control, renaming 23 controls and merging 53 controls. Let’s explore the controls added to ISO 27001 in the 2022 update.
Threat Intelligence:
Threat intelligence is the process of gathering, analyzing, and sharing information about potential and actual cybersecurity threats. It involves collecting data from various sources, including vulnerability databases, vendor-supplied patches, external threat feeds, social media, and other open-source intelligence (OSINT) tools, and using it to identify and mitigate potential risks to your organization’s network, systems, and data. You can use threat intelligence for various functions, including identifying and blocking malware, tracking and analyzing the activities of cybercriminals, detecting and responding to security incidents, and improving your security posture. Effective threat intelligence helps organizations better understand the nature and scope of potential threats and improve their ability to respond to them.
Information Security for use of Cloud Services:
Information security is crucial when using cloud services because these services involve storing and processing sensitive data on third-party servers that are not under your direct control. The security of your data and systems depends on the security measures put in place by your cloud service provider. Cloud service providers typically offer a range of security features, including encryption, access control, firewalls, intrusion detection and prevention, and regular security audits. The shared security responsibilities of the cloud model requires customers to evaluate the efficacy of the security features offered and ensure their policies and procedures are in sync with the level of security you have promised your clients.
In addition to relying on the security measures provided by your cloud service provider, you can take several steps to further enhance the security of your data and systems in the cloud. These may include implementing multi-factor authentication, using strong passwords and regularly changing them, limiting access to sensitive data, monitoring user activity, and periodically reviewing and updating your security policies and procedures.
ICT Readiness for business continuity:
ICT (Information and Communication Technology) readiness refers to the preparedness of an organization’s technological infrastructure and systems to respond to unexpected events or disruptions, such as natural disasters, cyber-attacks, or power outages. On the other hand, business continuity refers to an organization’s ability to continue its essential functions and operations during such events, minimizing the impact of the disruption on its operations, customers, and stakeholders. ICT readiness is crucial for business continuity because it enables organizations to maintain communication, data, and information flows even in challenging circumstances. Some ways in which ICT readiness can support business continuity are:
-
Data backup and recovery
-
Remote Access
-
Redundancy and failover systems
-
Cybersecurity
Physical Security Monitoring:
Physical security monitoring is a critical component of an organization’s information security management system (ISMS) in compliance with ISO 27001. It is the process of monitoring, evaluating, and controlling physical access to an organization’s premises, data centers, and other critical areas that house sensitive information. Physical security monitoring aims to prevent unauthorized access, theft, damage, or destruction of an organization’s assets, including its people, facilities, and equipment. Some of the key components of physical security monitoring for ISO 27001 include:
-
Access control
-
Security surveillance
-
Monitoring and Physical barriers such as fences, walls, gates, or locks
-
Alarm systems such as fire alarms, intrusion detection systems, or panic
-
Incident response procedures
-
Training and Awareness
Configuration Management:
Configuration Management is critical for ensuring the security of an organization’s information assets, including hardware, software, and data. In ISO 27001, Configuration Management is part of the Information Security Management System (ISMS) defined in clause 7.5.1. Its purpose is to ensure that information systems and assets are identified, controlled, and maintained throughout their life cycle. This includes identifying and documenting the configuration of information systems, maintaining the integrity of information assets, and ensuring that changes to information systems are properly authorized and controlled.
The configuration management process typically involves the following steps:
-
Identification
of all hardware and software components
-
Establishing a baseline
configuration for each component
-
Implementing controls
to ensure that all changes made to the system components are authorized, documented, and tracked.
-
Monitoring the system
components and configurations to ensure they comply with the established baseline configuration.
-
Reporting on the configuration management
process and its effectiveness to ensure that the organization’s information system remains secure and in compliance with applicable laws, regulations, and standards.
Information Deletion:
Information deletion is an essential component of information security. It involves securely and permanently removing information from all storage devices, including hard drives, USB drives, memory cards, and other digital storage media.
ISO 27001 provides guidelines on how organizations can ensure that information is deleted securely. These guidelines include the following:
-
Defining deletion procedures
, including identifying the types of information that need to be deleted, the methods of deletion, and the roles and responsibilities of individuals involved in the deletion process.
-
Use secure deletion methods
that render the information unrecoverable. This can include overwriting the information with random data, physically destroying the storage device, or using specialized software to erase the data securely.
-
Ensure secure disposal of storage devices
through physical destruction or secure disposal methods that prevent the information from being recovered.
-
Maintain records of all deletion activities
, including the type of information deleted, the date and time of deletion, the method used, and the individuals involved in the deletion process.
Data masking:
Data masking is a security technique used to protect sensitive data by replacing it with a fake value while keeping its original format and structure intact. The purpose of data masking is to prevent unauthorized access to sensitive information, such as personally identifiable information (PII) or confidential business data.
To implement data masking for ISO 27001, organizations can use a variety of techniques, such as:
-
Substitution
involves replacing sensitive data with a fictitious value, such as a random string of characters or a fake name.
-
Shuffling
involves reordering the values of a dataset while maintaining its overall structure.
-
Encryption
involves transforming sensitive data into an unreadable format, which can only be accessed with a decryption key.
-
Redaction
involves removing sensitive information from a document or file. For example, blacking out a customer’s social security number on a printed document.
Data Leakage Prevention:
Data leakage prevention (DLP) is a critical component of information security management in ISO 27001. It refers to the process of identifying, monitoring, and controlling sensitive data that may be at risk of being disclosed or exposed to unauthorized parties.
To prevent data leakage, an organization can implement various technical and procedural controls such as:
-
Network segmentation:
Network segmentation is a technique that divides a network into smaller subnetworks, which helps to control the flow of data between different segments. By segmenting the network, an organization can create a boundary that can be monitored and controlled to prevent unauthorized data transfer.
-
Access control:
Access control is a mechanism that ensures that only authorized personnel can access sensitive data. This can be done by using strong authentication mechanisms, such as two-factor authentication, and by implementing strict access control policies.
-
Data encryption:
Data encryption is the process of transforming data into an unreadable format, which can only be decrypted with a secret key. By encrypting sensitive data, an organization can prevent unauthorized access to the data in case of data leakage.
-
Data loss prevention software:
Data loss prevention (DLP) software is designed to monitor and control the flow of sensitive data within an organization. DLP software can detect and prevent unauthorized data transfer, block access to unauthorized devices, and provide alerts for suspicious activities.
-
Employee training:
Employees are often the weakest link in an organization’s security chain. Providing employees with regular training on data security policies, procedures, and best practices can help prevent data leakage.
Monitoring Activities:
Monitoring activities are essential to maintaining the effectiveness of the ISMS and ensuring that information security risks are identified and addressed promptly. Here are some of the monitoring activities that organizations should consider while implementing controls to comply with ISO 27001:
-
Security Incident Monitoring
to identify potential threats or vulnerabilities and to take steps to prevent them from occurring in the future.
-
Access Control Monitoring
to ensure that policies are working as intended to detect and prevent any unauthorized access attempts or other security breaches
-
Monitoring Compliance
with the organization’s policies and procedures, as well as with legal and regulatory requirements
-
Vulnerability Scanning
to identify and address vulnerabilities before they can be exploited
-
Monitoring System Logs
for unusual activity that could indicate a security breach
-
Risk Assessment
to ensure that the organization’s information security remains effective in the face of evolving threats
Web Filtering:
Web filtering is a mechanism used to control or restrict access to websites and online content based on predefined policies and prevent a security risk to an organization’s information systems. It is one of the controls that can be implemented to protect an organization’s information assets from unauthorized access, use, disruption, disclosure, modification, or destruction.
ISO 27001 requires that organizations establish policies and procedures for web filtering to protect their information assets from security threats such as malware, phishing, and other cyber attacks. These policies should be designed to meet the organization’s specific security needs and regularly reviewed and updated to reflect changes in the threat landscape.
Web filtering can be implemented using a variety of techniques, such as content filtering, URL filtering, and IP filtering. Content filtering involves examining the content of web pages and filtering out unwanted or harmful content based on predefined criteria such as keywords, categories, and file types. URL filtering involves blocking or allowing access to specific websites based on their URL address or domain name. IP filtering involves blocking or allowing access based on the IP address of the user’s computer or the website they are trying to access.
Web filtering policies should be implemented to strike a balance between security and user productivity. The policies should be reasonable, effective, and practical while allowing users to access the resources they need to do their jobs. ISO 27001 also requires organizations to provide awareness training to employees on the risks associated with browsing the web and the importance of following web filtering policies.
Secure Coding: Secure coding is a software development practice that aims to minimize the risk of vulnerabilities and weaknesses that could be exploited by attackers. It refers to the practice of writing software code that is resilient against security vulnerabilities.
When it comes to secure coding, ISO 27001 emphasizes the importance of incorporating security measures into the software development lifecycle (SDLC) from the outset. This means ensuring that security considerations are integrated into every phase of the SDLC, including requirements gathering, design, coding, testing, and maintenance.
To comply with the ISO 27001 standard, organizations must implement secure coding practices that include:
-
Secure design principles:
Software design must include security considerations from the outset, including secure architecture, security protocols, and security controls.
-
Threat modeling:
The software must be analyzed for potential vulnerabilities and threats, and appropriate security controls must be implemented to mitigate those threats.
-
Code review:
All code must be thoroughly reviewed to identify and address potential vulnerabilities and weaknesses.
-
Testing:
The software must undergo rigorous testing to identify and address potential security issues before it is released.
-
Secure coding standards:
Developers must adhere to established secure coding standards such as the OWASP Top 10 to ensure that the code is developed in a secure and consistent manner.
-
Training:
All developers must be trained in secure coding practices to ensure they know the latest threats and best practices.
databrackets and ISO 27001:2022
databrackets has a team of certified ISO Lead Auditors. We are accredited to certify organizations who clear the final assessment for their ISO/IEC 27001 Certificate. However, our entire range of services for ISO 27001 includes:
All our ISO services involve the use of our secure, user-friendly online assessment platform called ‘dbACE’. To help organizations who have a strong IT team and who only need a checklist to get ready for the final assessment, we have a DIY (Do It Yourself) assessment toolkit with all the clauses and controls stipulated by ISO 27001:2022. Customers need to upload their data along with evidence and mark the clause/controls’ ‘implementation’ status for Stage 1 and Stage 2 Assessments.
Our auditors conduct an impartial assessment based on the evidence provided and record their findings on our platform. This helps them communicate the results and seek corrective measures wherever necessary – all in one location. The dbACE interface makes the turnaround quicker and saves time, effort and, thereby, costs. The documentation for the audit from start-to-finish takes place on this platform. This includes the final report that reflects the status of the customer’s adherence to ISO 27001 standards and guidelines.
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.