SOC 2 (System and Organization Controls 2) is an auditing procedure focused on data privacy. It has been developed by the American Institute of Certified Public Accountants (AICPA) and is designed to evaluate how companies manage customer data and ensure that they uphold information security, privacy, and integrity. SOC 2 compliance is essential while handling customer data, because it demonstrates an organization’s ability to manage data responsibly and securely.
SOC 2 is based on AICPA’s Trust Service Criteria (TSC) : Security, Availability, Processing Integrity, Confidentiality, and Privacy. It provides standards that guide organizations in safeguarding customer data from breaches, unauthorized access, and loss. Achieving SOC 2 compliance signals to clients, partners, and stakeholders that your company prioritizes data protection.
Purpose of SOC 2
The primary purpose of SOC 2 is to ensure that service providers handle and protect client data properly and in line with stringent standards. Specifically, SOC 2 aims to:
Provide Assurance to Customers: SOC 2 reports demonstrate to clients that the organization has established effective controls to protect data, ensuring trust and confidence.
Protect Sensitive Data: SOC 2 ensures that organizations use proper security protocols to prevent data breaches and unauthorized access, thereby safeguarding confidential information.
Mitigate Operational Risks: By aligning with SOC 2 standards, organizations can reduce risks associated with security incidents, downtime, and service disruptions.
Overall, SOC 2 helps organizations create a solid security foundation, ensuring data integrity, confidentiality, and accountability.
Organizations and Personnel Involved in SOC 2
SOC 2 compliance is assessed by external auditors who are licensed to perform SOC 2 examinations. Here’s an overview of the authorities involved:
American Institute of Certified Public Accountants (AICPA): AICPA is the body that developed the SOC 2 framework. It outlines the criteria and guidance used by auditors to assess compliance with SOC 2 standards.
Certified Public Accountants (CPAs) or External Auditors: An accredited CPA firm or external auditor conducts SOC 2 assessments. The auditor evaluates whether the company’s controls align with the Trust Service Criteria and prepares a SOC 2 report detailing the findings.
Internal Compliance Teams: Internal compliance teams work to prepare the organization for a SOC 2 audit by conducting internal reviews and risk assessments and ensuring that all controls are functional and they meet SOC 2 requirements.
The SOC 2 Framework – AICPA’s 5 Trust Service Criteria
SOC 2 focuses on five Trust Service Criteria (TSC), each of which plays a crucial role in determining how data is managed and protected. These are:
Security: Security is the foundational component of SOC 2, often referred to as the “common criteria.” This involves ensuring that information and systems are protected against unauthorized access. It includes measures such as firewalls, encryption, multi-factor authentication (MFA), and physical security.
Availability: The Availability criteria ensure that systems and data are accessible when required by customers. This means maintaining uptime standards, utilizing backup solutions, and having robust disaster recovery measures to mitigate potential disruptions.
Processing Integrity: Processing Integrity ensures that system operations are complete, valid, and accurate. It means that all transactions and processes function as intended, ensuring there are no errors or unauthorized changes that could affect the accuracy of customer data.
Confidentiality: The Confidentiality criterion focuses on ensuring that sensitive information is accessible only by authorized personnel and that all methods for data storage, access, and sharing are secure. It includes the use of encryption and strict access controls.
Privacy: The Privacy criteria govern how personally identifiable information (PII) is managed and protected. This includes obtaining informed consent from individuals, properly handling data collection, and adhering to privacy preferences specified by clients.
Industries that can benefit from SOC 2
SOC 2 compliance is specially relevant for service providers handling sensitive customer information. Here’s a look at the industries that benefit most from SOC 2 compliance:
Cloud Service Providers: Cloud companies, SaaS providers, and data centers handle large volumes of customer data, which often includes confidential and sensitive information. SOC 2 compliance assures customers that these providers have strong data protection measures in place.
Financial Services: Banks, fintech companies, and investment firms are required to adhere to stringent data security standards to protect financial transactions and customer records. SOC 2 ensures these organizations have controls in place to mitigate risks like unauthorized access and data breaches.
Healthcare Technology: Healthcare companies that provide patient management systems, electronic health records (EHRs), or telehealth platforms need SOC 2 to ensure that all health data is protected. SOC 2 compliance complements HIPAA requirements, demonstrating the implementation of strong security practices.
Technology and IT Consulting Firms: IT consultants, managed service providers (MSPs), and other tech companies working on digital transformation and handling client data must implement robust security measures. SOC 2 compliance proves that they meet standards for security and privacy.
E-commerce and Online Retail: E-commerce companies collect payment information, customer details, and behavioral data. SOC 2 helps assure customers that their financial data and personal details are being securely processed and protected.
Legal and Professional Services: Law firms, accountants, and other professional services manage confidential client data, including legal documents, contracts, and tax information. SOC 2 certification ensures that adequate controls are in place to keep data safe and uphold client trust.
Telecommunications: Telecom companies handle data that includes user communications, call records and other sensitive data. SOC 2 compliance helps maintain privacy and data protection, preventing unauthorized access to customer records.
Penalties for Non-Compliance with SOC 2
While SOC 2 itself does not enforce legal penalties, the consequences of failing to achieve or maintain compliance can be significant:
Loss of Business Opportunities: SOC 2 compliance is often a prerequisite for contracts or partnerships, especially for B2B companies working with enterprises. Non-compliance may result in loss of clients or missed business opportunities.
Increased Risk of Data Breaches: Failure to implement adequate security measures as required by SOC 2 may lead to data breaches, exposing sensitive customer information. This can lead to financial liabilities, costly settlements, and increased risk of cyberattacks.
Damage to Reputation: Non-compliance can lead to reputational damage, as customers and stakeholders expect strong data protection measures. A lack of SOC 2 certification could imply that the company does not prioritize data security, leading to a loss of trust.
Customer Liability: In the event of a breach involving sensitive customer information, customers may hold the organization liable, which could lead to costly litigation and compensation. SOC 2 certification can help limit liability by demonstrating that appropriate safeguards are in place.
Employee Responsibilities under SOC 2
Employees are integral to maintaining SOC 2 compliance. Here are key responsibilities that all staff should adhere to:
Follow Security Policies and Procedures: Employees must strictly follow the organization’s security protocols, including password management, MFA (multi-factor authentication), and secure data access policies.
Maintain Data Confidentiality: Employees must understand the importance of confidentiality when dealing with customer data. Ensure that all data is accessed and shared only as required and is restricted to authorized personnel only.
Report Security Incidents: If employees notice any unusual activity, such as unauthorized data access attempts or phishing emails, it must be reported immediately to the information security officer or compliance team.
Control Access to Systems: Only use approved devices and secure networks to access company systems. Employees must adhere to role-based access controls, ensuring data is accessed only on a need-to-know basis.
Use Data Encryption and Secure Communication Channels: Always use encryption to protect data while sharing externally or storing it in a cloud environment. Secure communication tools should be used to share sensitive information.
Participate in Regular Training: Stay informed about the latest security threats, policies, and procedures through regular security awareness training. Employees must know how to identify threats like phishing or malware and respond accordingly.
Best Practices for SOC 2 Compliance
Follow a Strong Access Control Policy: Limit access to information based on roles and responsibilities. Only employees who need specific data should have access to it. This prevents unauthorized access and reduces security risks.
Implement Multi-Factor Authentication (MFA): MFA should be used wherever possible to ensure that unauthorized individuals cannot access company systems, even if they know a password. This is crucial for enhancing security.
Encrypt Data at Rest and in Transit: Whether data is being stored or transmitted, it should be encrypted to protect it from unauthorized access. Encryption ensures that even if data is intercepted, it remains unreadable.
Backup Data Regularly: Maintain regular backups to ensure data availability in case of a disruption or breach. Backups help maintain business continuity by providing quick data recovery options.
Monitor and Audit Systems Continuously: Regular monitoring and auditing are essential to maintaining compliance with SOC 2. Log all access to systems and perform internal audits to identify weaknesses and ensure compliance.
Recognize Social Engineering Threats: Employees should be trained to identify and avoid social engineering tactics like phishing. Stay cautious with unsolicited requests for information or emails with suspicious links.
Ensure Vendor Compliance: Review and ensure that any third-party vendors you work with are compliant with SOC 2 standards. Vendor compliance is critical to ensuring that no weak link compromises your organization’s information security.
SOC 2 is an essential standard that ensures organizations have the right controls in place to protect sensitive information, maintain customer trust, and manage operational risks. Its criteria—Security, Availability, Processing Integrity, Confidentiality, and Privacy—cover the key elements required to maintain robust data protection practices.
Every employee plays a critical role in maintaining SOC 2 compliance. By following information security policies, controlling data access, and reporting any incidents, employees help secure the organization against data breaches and maintain a high standard of trust with clients and partners.
Adopting SOC 2 standards isn’t just about achieving certification—it’s about building a security-first culture, maintaining business resilience, and being proactive in managing risks.
How databrackets can help you prove your compliance with SOC 2
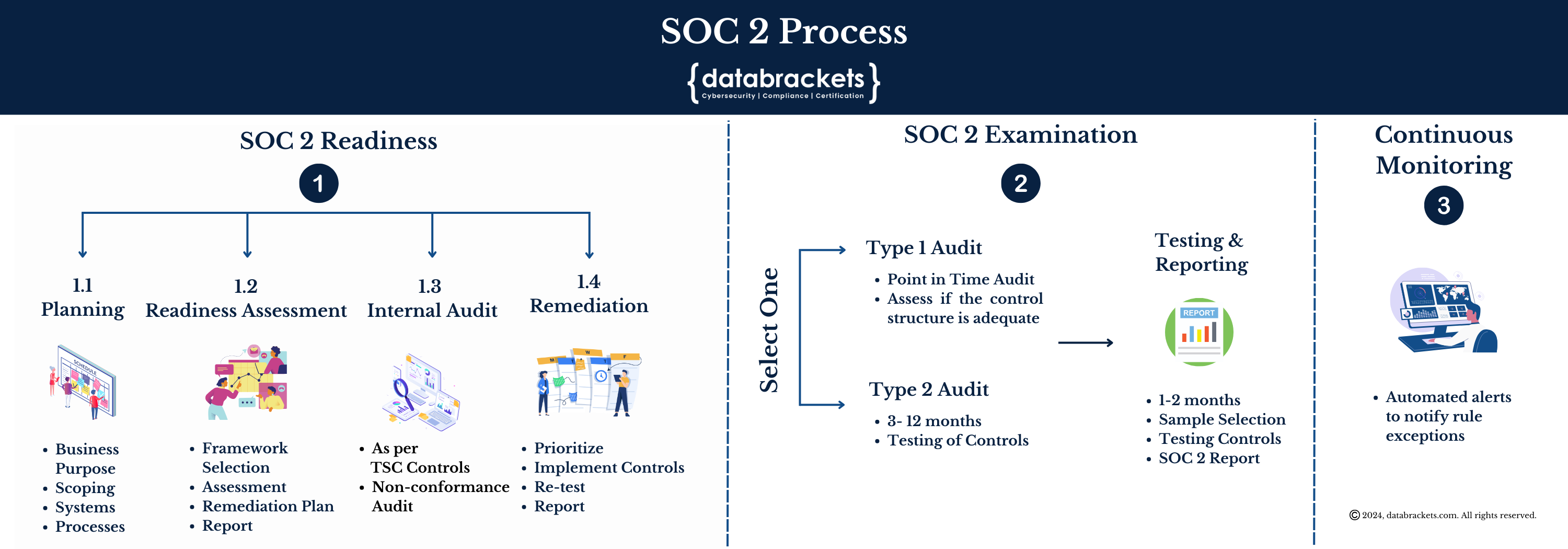
At databrackets, we are a team of certified and experienced security experts with over 12 years of experience across industries. We have helped organizations of all sizes comply with cybersecurity best practices and prepare for their SOC 2 audit. We can help you prove your compliance with SOC 2 by working as your readiness partner. We offer 3 Engagement Options – our DIY Toolkits (ideal for MSPs and mature in-house IT teams), and Hybrid or Consulting Services for Compliance / Security Standards.
databrackets as your SOC 2 Compliance Readiness Partner

Working with a SOC 2 Compliance Readiness Partner can help you save a significant amount of time, money and resources. Our security experts have extensive experience working with clients across industries with the sole purpose of helping to position your organization for a successful SOC 2 audit. The tasks that we undertake, as your SOC 2 Compliance Readiness Partner include:
Initial Consultation and Scoping
Educating the Client
Gap Analysis
Control Mapping
Documentation Review and Development
Remediation Planning
Implementation Support
Internal Audit
Readiness Assessment Report
Ongoing Support and Monitoring
The data of our SOC 2 Readiness clients is maintained in a structured format on our GRC platform – dbACE and is accessible to the CPA that you chose to work with. You can refer to the controls, Trust Services Criteria and the 2 sections of your SOC 2 Report which you need to submit – the Management’ Assertion and a Description of your System, using your unique login. We also collaborate with certified CPA firms whom you can choose to work with, if you decide to do so. Hence, working with a Readiness Partner helps you to not only prepare for SOC 2 Certification but also ensures that your security controls are implemented adequately, and you have evidence to prove their effectiveness.
Overview of databrackets
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc. We are an authorized certifying body for ISO 27001 and a Registered Practitioner Organization for CMMC. We also have partnerships to help clients prepare for and obtain other security certifications.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Srini Kolathur
Srini is the Director of databrackets.com. He is a results-driven security and compliance professional with over 25 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, CMMC, FedRAMP, NIST Security Standards, HIPAA, Security Risk Assessments, among others. His accreditations include Certified CMMC Assessor, CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE. He has verified all the technical information in this blog and co-authored it with Aditi Salhotra.