You’ve spent months implementing security controls to prepare for your CMMC Certification. Your policies are polished. Your System Security Plan (SSP) is complete. Now comes the moment of truth: the official CMMC assessment. For many defense contractors, the assessment itself is shrouded in mystery.
What really happens behind closed doors?
How do assessors think?
What separates organizations that sail through certification from those that struggle?
As a Certified Third-Party Assessment Organization (C3PAO), databrackets brings deep expertise from years of conducting security assessments across multiple rigorous frameworks. This blog is intended to help you prepare for your CMMC Assessment and understand the process.
The CMMC Assessment Mindset:
Understanding What Assessors Really Look For
Before we dive into the mechanics, you need to understand the fundamental principle that drives every CMMC assessment: documentation must demonstrate implementation. CMMC assessments follow a rigorous methodology where documentation, implementation evidence, and operational reality must all align. Assessors verify that your security controls are properly documented, correctly implemented, and actually protect Controlled Unclassified Information (CUI) as specified in your policies and procedures.
The Three Pillars of CMMC Assessment Evidence
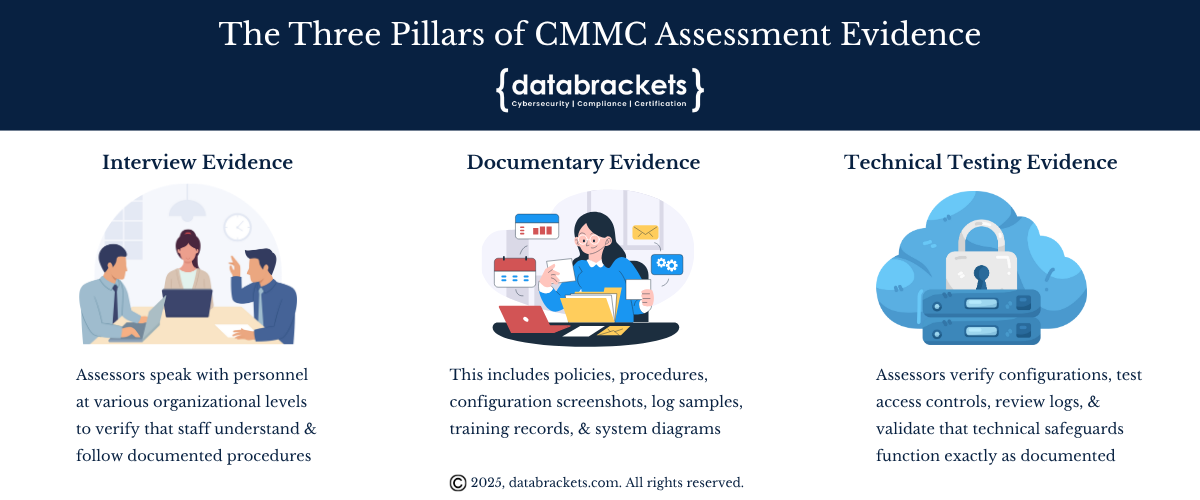
Every security requirement is evaluated through three complementary lenses, and all three must align:
1. Interview Evidence: Assessors speak with personnel at various organizational levels to verify that staff understand and follow documented procedures. These conversations reveal whether your security practices operate as documented. A receptionist’s understanding of visitor escort procedures must align with your written visitor management policy, just as your security officer’s incident response knowledge must match your documented procedures.
2. Documentary Evidence: This includes policies, procedures, configuration screenshots, log samples, training records, and system diagrams. Documentation is the foundation of CMMC compliance—it establishes what you’ve committed to implement. Your documents must be comprehensive, current, and must accurately describe your actual implementation. Without proper documentation, implementation cannot be validated.
3. Technical Testing Evidence: Assessors directly examine your systems, networks, and security tools to verify that what’s documented is actually implemented and configured correctly. They verify configurations, test access controls, review logs, and validate that technical safeguards function exactly as documented. This testing confirms that your documented practices are reflected in your actual system configurations.
The organizations that succeed understand this trinity: documentation establishes requirements, implementation fulfills those requirements, and testing validates the alignment between documentation and implementation. All three elements must be present and consistent.
CMMC Pre-Assessment Phase: Setting the Stage for Success
The assessment begins long before assessors arrive. The pre-assessment phase establishes the foundation for everything that follows.
1. Scoping Precision: Define Your Boundaries Clearly
Assessment scope determines which systems, facilities, and personnel fall under evaluation. Imprecise scoping leads to expensive surprises mid-assessment. You must identify:
Every information system that processes, stores, or transmits CUI
All physical locations where CUI resides or is accessed
Network connections between in-scope and out-of-scope systems
Cloud services and managed service providers handling CUI
Personnel with CUI access or security responsibilities
Common scoping mistakes include:
Forgetting about backup systems or disaster recovery environments
Overlooking development or testing systems that handle production CUI
Missing administrative systems used by personnel with CUI access
Failing to document cloud provider responsibilities accurately
One way to ensure you’re on track is to create visual network diagrams showing exactly where your CUI boundary begins and ends. Include all data flows, external connections, and security controls at boundary points. Assessors will request these immediately, and clarity here prevents scope creep during assessment.
2. The Pre-Assessment Questionnaire: Your First Impression
The C3PAO will send a detailed questionnaire requesting information about your organization, systems, and security program. This isn’t busywork—your responses shape the assessor’s approach and timeline.
Critical Pre-Assessment Information:
Organization structure and key personnel roles
System inventory with technology details
Network architecture and security boundaries
External service providers and their responsibilities
Assessment logistics (facilities, equipment, personnel availability)
Incomplete or vague responses create confusion and extend assessment duration. Be specific. If assessors can’t understand your environment from your questionnaire responses, they’ll spend assessment time seeking clarity rather than validating controls.
3. Document Organization: Build Your Evidence Library
Assessors will request extensive documentation. Having everything organized and instantly accessible demonstrates professionalism and accelerates the process.
Organize evidence by NIST SP 800-171 control family:
Access Control (AC)
Awareness and Training (AT)
Audit and Accountability (AU)
Configuration Management (CM)
Identification and Authentication (IA)
Incident Response (IR)
Maintenance (MA)
Media Protection (MP)
Personnel Security (PS)
Physical Protection (PE)
Risk Assessment (RA)
Security Assessment (CA)
System and Communications Protection (SC)
System and Information Integrity (SI)
For each control, prepare:
Policy excerpts relevant to the requirement
Detailed procedures showing implementation steps
Configuration evidence (screenshots, exports, settings)
Log samples demonstrating monitoring
Training records proving personnel awareness
Incident documentation showing response capability
One way to stay organized is to create an evidence index spreadsheet mapping each NIST SP 800-171 requirement to specific file locations. When assessors request evidence for Access Control requirement 3.1.5, you should produce it within minutes, not hours.
Assessment Week: Navigating the Four-Phase CMMC Evaluation
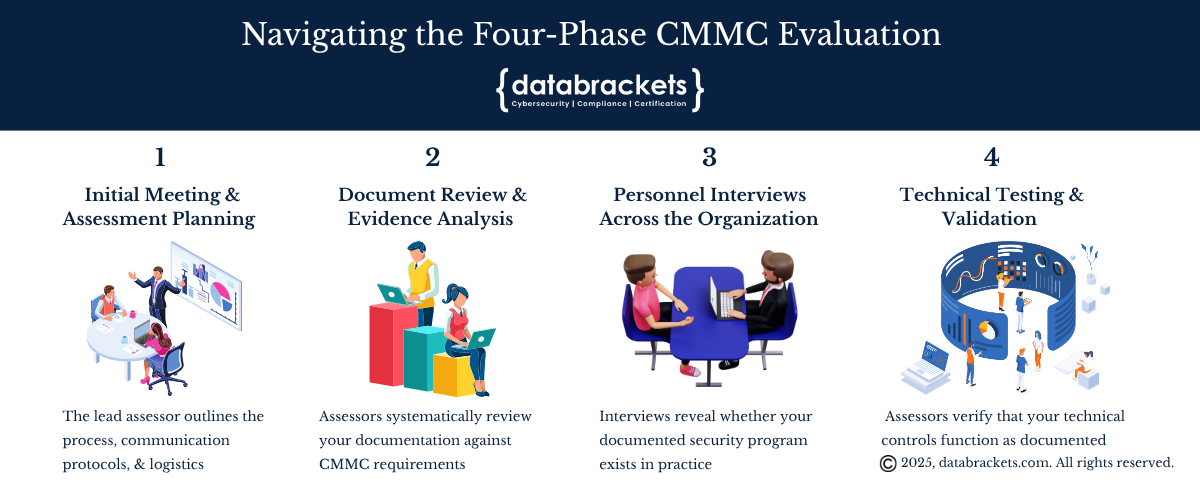
Understanding the assessment structure helps you prepare appropriately and manage the experience effectively.
Phase 1: Initial Meeting and Assessment Planning
The assessment formally begins with an initial meeting where the C3PAO lead assessor outlines the process, establishes communication protocols, and confirms logistical details.
What Happens in Phase 1:
Assessor team introductions and role clarifications
Assessment methodology and timeline review
Scope confirmation and boundary validation
Evidence submission process explanation
Communication protocols and escalation procedures
Facility access and system access arrangements
Your Objectives:
Ensure all key personnel attend and understand their roles
Clarify any scope questions before assessment activities begin
Confirm assessor access to systems and facilities
Establish primary points of contact for each control domain
Set realistic expectations for assessment duration and intensity
You need to ensure that your Assessment Official is present to demonstrate organizational commitment. Prepare a brief presentation showing your security program highlights. This isn’t required, but it helps assessors understand your environment and shows confidence in your preparation.
Phase 2: Document Review and Evidence Analysis
Assessors systematically review your documentation against CMMC requirements. This phase typically occurs early in the assessment and informs subsequent interviews and testing.
What Assessors Examine in Phase 2:
System Security Plan completeness and accuracy
Policy documentation covering all 14 control families
Procedural guidance for personnel implementing controls
Network architecture diagrams and data flow documentation
Risk assessment results and mitigation strategies
Configuration standards and baseline documentation
Training program materials and completion records
Common Documentation Deficiencies:
Generic policies that don’t reflect your actual environment
Procedures lacking sufficient implementation detail
Network diagrams missing critical components or connections
Incomplete training records or outdated materials
Risk assessments without clear mitigation plans
Policies contradicting actual practices
Your documentation should tell a coherent story. If your access control policy states that multifactor authentication (MFA) is required for remote access, your configuration screenshots should confirm this, your procedures should explain how it’s implemented, and interviews should reveal that users understand the requirement.
When assessors identify documentation gaps, you need to respond professionally. Acknowledge the finding, provide any additional relevant information, and resist the urge to be defensive. Remember that assessors are there to objectively verify CUI protection—their role is independent validation, not advocacy for your success or failure.
Phase 3: Personnel Interviews Across the Organization
Interviews reveal whether your documented security program exists in practice. Assessors will speak with personnel at multiple organizational levels, not just IT staff.
Who Gets Interviewed:
Executive leadership (security program commitment and oversight)
Security officers and IT administrators (technical implementation)
HR personnel (personnel security and onboarding/offboarding)
Regular employees (security awareness and CUI handling)
Physical security staff (visitor management and facility controls)
Vendors and contractors (third-party security responsibilities)
Typical Interview Questions:
For Access Control:
“How do you obtain access to systems containing CUI?”
“What happens when an employee changes roles or leaves?”
“Describe the process for requesting elevated privileges.”
“How do you know which files contain CUI?”
For Incident Response:
“What would you do if you discovered a potential security breach?”
“Who do you contact, and what’s the timeline?”
“Can you show me where the incident response procedures are located?”
“Have you participated in incident response drills or exercises?”
For Physical Security:
“How do visitors gain access to facilities with CUI?”
“What controls prevent unauthorized access to restricted areas?”
“How are visitors monitored during their time in the facility?”
CMMC Interview Success Strategies
1. Be Honest and Direct: If you don’t know something, say so rather than guessing. “I don’t know, but I can find out” is far better than incorrect information. Assessors appreciate honesty and can distinguish between knowledge gaps and systemic problems.
2. Speak to Your Experience: Describe what you actually do, not what you think assessors want to hear. If you’ve never had a security incident, explain your preparedness rather than inventing scenarios. Authenticity matters.
3. Reference Documentation When Appropriate: It’s perfectly acceptable to refer to procedures during interviews. No one expects perfect recall of every policy detail. Knowing where to find information demonstrates competence.
4. Demonstrate Security Awareness: Even if you’re not in IT, you should understand basic CUI handling requirements, your role in protecting sensitive information, and whom to contact with questions. Security isn’t just IT’s responsibility—it’s organizational.
5. Stay Calm and Professional: Assessment can feel intense, especially if assessors probe an area where you’re less confident. Take a breath, listen carefully to the question, and respond thoughtfully. If you need clarification, ask.
Phase 4: Technical Testing and Validation
This is where assessors verify that your technical controls function as documented. No amount of impressive documentation compensates for non-functional controls.
What Gets Tested:
1. Access Control Mechanisms
User authentication processes and multifactor authentication
Privileged account management and monitoring
Password complexity and account lockout settings
Session timeout configurations
Remote access controls and VPN security
2. Network Security Controls
Firewall rules and network segmentation
Intrusion detection/prevention systems
Wireless network security
External connection security
Boundary protection effectiveness
3. Encryption Implementation
Data at rest encryption (disk, database, file-level)
Data in transit encryption (TLS versions, cipher suites)
FIPS 140-2 validation for cryptographic modules
Key management processes
Certificate management and expiration monitoring
4. Logging and Monitoring
Audit log generation and collection
Security event monitoring and alerting
Log retention periods and protection
Log review processes and documentation
Time synchronization across systems
5. Configuration Management
System hardening against security benchmarks
Patch management processes and currency
Configuration baseline documentation
Change control procedures
Software whitelist/blacklist enforcement
6. Backup and Recovery
Backup frequency and scope
Backup encryption and storage security
Recovery testing documentation
Alternate storage location for backup media
Technical Testing Pitfalls
Technical testing often reveals gaps that organizations didn’t anticipate during implementation. Here are the most common pitfalls that lead to findings during the validation phase:
1. The “It Works in Production” Assumption: Just because a control worked when you implemented it doesn’t mean it works now. Security drift occurs. Configuration changes happen. Verify everything before assessment.
2. Incomplete FIPS Validation: Encryption modules must be FIPS 140-2 validated. Having certificates isn’t enough—you need the actual FIPS validation documentation from NIST’s Cryptographic Module Validation Program (CMVP). Many organizations discover mid-assessment that their encryption doesn’t meet requirements.
3. Log Retention Gaps: CMMC requires audit log retention, but many organizations haven’t configured this properly. Logs might generate but auto-delete after days rather than the required retention period. Assessors will verify actual log storage, not just generation.
4. Forgotten Systems: Backup systems, out-of-band management systems, and development environments often get overlooked during implementation but are in scope for assessment. Assessors will test these systems too.
CMMC Testing Day Success Strategies
Preparation and availability are key to smooth technical validation. Implement these strategies to facilitate efficient testing and demonstrate your controls effectively:
Prepare Demonstration Accounts: Create test user accounts that assessors can use for testing without disrupting production. Demonstrate access control failures (locked accounts after failed login attempts) and successes (proper access granting).
Have Technical SMEs Available: Your network administrator, system administrators, and security engineers should be available during testing. Questions will arise that require technical expertise to answer accurately.
Document Workarounds and Exceptions: If any systems have approved exceptions or compensating controls, ensure assessors understand these before testing. Context prevents misunderstandings.
Practice Demonstrating Controls: Before assessment, practice showing how each technical control works. Can you quickly demonstrate how your firewall blocks unauthorized traffic? Can you show log retention policies in action? Fumbling through demonstrations wastes time and creates doubt.
Handling Findings: Turning Challenges into Opportunities
Even well-prepared organizations receive findings during assessment. Understanding how findings work and how to respond strategically makes the difference between successful certification and delays.
Understanding CMMC Certification Assessment Findings:
Met (Satisfactory) The control is fully implemented, functions effectively, and evidence clearly demonstrates compliance. This is your goal for all 110 requirements.
Not Met (Deficiency) The control is either not implemented, doesn’t function as required, or lacks sufficient evidence. Not Met findings must be addressed either through immediate remediation or inclusion in a Plan of Action and Milestones (POA&M).
Not Applicable: The control doesn’t apply to your environment. For example, if you don’t use wireless networks, wireless security requirements might be Not Applicable. However, assessors must agree with your determination—you can’t unilaterally declare controls Not Applicable.
Your Strategic Response to Findings:
Immediate Clarification: Sometimes findings result from miscommunication or incomplete evidence presentation. If an assessor identifies a deficiency but you have evidence that addresses it, provide that information immediately. Don’t wait until the report is finalized.
Additional Evidence You may have the control implemented but didn’t present the right evidence. If assessors mark incident response as deficient because they haven’t seen documentation of incidents, provide your incident log showing tracking and resolution, even if incidents are minor.
Acknowledge and Plan If the finding is legitimate, acknowledge it professionally. Explain whether you plan to remediate immediately or include it in your POA&M. Demonstrating a clear path forward shows maturity and commitment.
Understand Scoring Impact Different controls carry different point values based on security impact. Critical controls (those protecting against high-impact threats) have higher point values. Understand which findings most affect your overall score and prioritize accordingly.
The POA&M Strategy: Plans of Action and Milestones allow organizations to achieve Conditional certification while addressing specific gaps, but they come with strict requirements.
POA&M Eligibility Requirements
Minimum 80% assessment score (88 of 110 practices Met)
Only non-critical requirements can be placed on POA&M
Specific encryption exceptions allow POA&M treatment
Clear remediation plan with milestones required
POA&M Best Practices
Be Realistic About Timelines: You have 180 days to close all POA&M items and complete a closeout assessment. Set achievable milestones. Overpromising and underdelivering results in expired certification.
Assign Clear Ownership: Each POA&M item needs a responsible person and necessary resources. Generic assignments like “IT Department” lack accountability.
Document Progress: Maintain detailed records of remediation activities. Your closeout assessment will require evidence that POA&M items are truly resolved, not just marked complete.
Prioritize Based on Risk: Address highest-risk gaps first. If your POA&M includes both security awareness training gaps and encryption deficiencies, encryption should take priority due to its direct impact on CUI protection.
Consider Strategic POA&M Use: Some organizations strategically use POA&Ms for controls requiring significant time or resources to implement fully. Rather than delaying certification, they achieve Conditional status and methodically address remaining items. This approach works if you have a solid remediation plan and organizational commitment.
Post-Assessment: Maximizing Your Certification Value
After completing all assessment activities, the C3PAO provides detailed results.
CMMC Assessment Report Contents:
Overall score and certification determination
Individual control findings (Met, Not Met, Not Applicable)
Evidence reviewed and testing performed
Observations and recommendations
POA&M items if applicable
CMMC Certification Outcomes:
Final Level 2: All 110 requirements Met or appropriately marked Not Applicable. Your certification is valid for three years with annual affirmation requirements. You can immediately compete for contracts requiring CMMC Level 2 certification without restrictions.
Conditional Level 2: You achieved the 80% threshold but have controls on POA&M. You can begin contract work but must complete POA&M remediation within 180 days and pass a closeout assessment to transition to Final status.
Not Achieved: Below 80% threshold or critical requirements deficient. You must remediate significant gaps and undergo reassessment. This outcome is rare for organizations that adequately prepare but can occur if major systemic issues exist.
Closeout Assessment for POA&M Items: If you receive Conditional certification, the closeout assessment validates your POA&M remediation. This isn’t a full reassessment—it focuses specifically on previously deficient controls.
Closeout Assessment Process:
C3PAO schedules assessment within your 180-day window
You provide evidence demonstrating remediation
Assessors verify each POA&M item is resolved
Upon successful closeout, you receive Final certification status
Closeout Preparation:
Test remediated controls thoroughly before closeout
Document all implementation steps taken
Update your SSP and procedures to reflect changes
Ensure personnel understand and can demonstrate new practices
Gather fresh evidence showing effective operation
Leveraging Your CMMC Certification
Immediate Actions to be completed:
Update your SPRS with your certification status
Notify current customers and contracting officers
Highlight certification in capability statements and proposals
Update marketing materials and website
Issue press release announcing your achievement
Strategic Advantages of getting Certified:
Priority consideration for contracts requiring CMMC
Competitive differentiation from non-certified competitors
Stronger position in negotiating with primes
Foundation for additional certifications (ISO 27001, SOC 2)
Improved organizational security posture and risk reduction
Maintaining your CMMC Certification
Certification isn’t a finish line—it’s a commitment to ongoing security. Understanding maintenance requirements prevents surprises.
Annual Affirmation Requirements: Organizations with Level 2 certification must affirm their continued compliance annually through SPRS. This isn’t just a formality—it’s a formal attestation that your security posture remains at certification levels.
What an Affirmation Involves:
Senior official reviews security program status
Verification that all controls remain effective
Confirmation that no material changes have degraded security
Formal attestation in SPRS
When to Reconsider An Affirmation: If you implemented significant changes like major system upgrades, network reconfigurations, personnel turnover affecting security roles, etc. you may need an internal assessment before affirming. False affirmations carry serious consequences.
Managing Change Without Losing Compliance
Organizations evolve. Systems change. Personnel transition. Managing these changes while maintaining CMMC compliance requires deliberate processes.
High-Impact Changes That Require Attention
Network architecture modifications affecting CUI boundaries
New cloud services or managed service providers
Major application deployments or retirements
Facility moves or expansions
Significant personnel turnover in security roles
Mergers, acquisitions, or organizational restructuring
Change Management Best Practices
Assess the impact on CMMC requirements before implementing changes
Update SSP documentation to reflect modifications
Retrain personnel on new procedures
Test affected controls after implementation
Document changes for future assessment preparation
Preparing for your Triennial CMMC Reassessment
Your certification expires after three years, requiring a full reassessment. Smart organizations begin preparation 12-18 months before expiration.
What you need to do 18 Months Before your CMMC Certification Expires:
Conduct internal compliance review
Identify any drift from certified state
Plan remediation for identified gaps
Budget for reassessment costs
What you need to do 12 Months Before your CMMC Certification Expires:
Engage C3PAO for reassessment scheduling
Update all documentation to current state
Conduct mock assessment
Address any discovered deficiencies
What you need to do 6 Months Before your CMMC Certification Expires:
Finalize assessment scheduling
Complete final preparation activities
Ensure all evidence is current and organized
Brief personnel on reassessment process
The availability of a C3PAO remains constrained. Schedule your reassessment early. Waiting until months before expiration limits options and creates unnecessary pressure.
Common CMMC Assessment Challenges
& How to Overcome Them
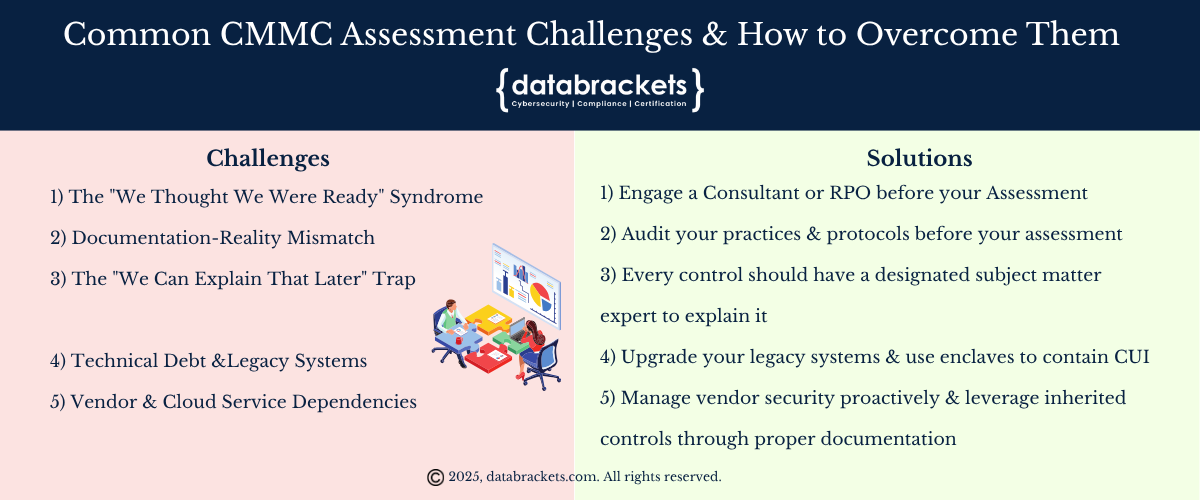
Challenge 1: The “We Thought We Were Ready” Syndrome
Many organizations believe they’re prepared but discover significant gaps during assessment. This often stems from misunderstanding requirements or overestimating implementation completeness.
Solution: Engage a CMMC Compliance Consultant or a Registered Practitioner Organization (RPO) for an independent readiness assessment before scheduling your C3PAO assessment. An objective third-party evaluation identifies issues while you still have time to address them. Remember: C3PAOs cannot provide readiness consulting to organizations they assess, so you need to separate readiness and certification services.
Challenge 2: Documentation-Reality Mismatch
Policies document ideal practices, but reality often diverges. Assessors quickly identify when documented procedures don’t match actual behavior.
Solution: Audit your practices before assessment. Shadow your team. Observe how they really work. Update documentation to reflect reality, or change practices to match documentation. Mismatches always surface during assessment, so address them proactively.
Challenge 3: The “We Can Explain That Later” Trap
During assessment, organizations sometimes promise to provide evidence or explanations “later” rather than having information readily available. This creates negative impressions and extends assessment timelines.
Solution: Prepare thoroughly. Every piece of evidence should be accessible within minutes. Every control should have a designated subject matter expert who can explain it immediately. If you don’t know something, acknowledge it—but don’t repeatedly defer basic questions.
Challenge 4: Technical Debt and Legacy Systems
Many organizations operate legacy systems that don’t easily support modern security controls. These systems become assessment challenges when they handle CUI.
Solution: Address this early. Options include:
Upgrading or replacing legacy systems before assessment
Implementing compensating controls with assessor approval
Isolating legacy systems from CUI processing
Using enclaves to contain CUI within secured environments
Documenting technical limitations and mitigation strategies
Don’t surprise assessors with legacy system challenges during assessment. Discuss approaches beforehand to ensure alignment on acceptable solutions.
Challenge 5: Vendor and Cloud Service Dependencies
Your security posture depends partly on vendors and cloud providers. When they fall short, your certification suffers.
Solution: Manage vendor security proactively:
Include security requirements in vendor contracts
Obtain vendor security documentation and certifications
Document shared responsibility models clearly
Verify vendor claims through independent assessment
Have backup plans if vendors can’t meet requirements
For cloud services, leverage inherited controls through proper documentation. If AWS handles physical security for your cloud infrastructure, document this clearly and obtain AWS compliance documentation supporting your requirements.
Your Next Steps: Moving From Preparation to Certification
You now understand what happens during CMMC assessment and how to excel at each stage. The question isn’t whether to pursue certification—it’s when to begin.
If You’re Early in Your Journey: Focus on compliance preparation first. Engage an RPO for gap analysis and implementation support. Build your security program methodically. Don’t rush to assessment before you’re ready—failure wastes time and money.
If You’re Nearing Readiness: Schedule a mock assessment to validate preparation. Address any identified gaps. Organize your evidence library. Brief your team on assessment expectations. Then engage a C3PAO to schedule your formal assessment.
If You’re Ready Now: Contact databrackets to discuss C3PAO assessment services. With limited C3PAO availability and high demand, scheduling early ensures you secure assessment slots that align with your contract timelines.
If You’re Uncertain: Schedule a consultation with our team. We can help you understand where you are in the journey, what preparation remains, and what timeline makes sense for your situation. This initial discussion is complimentary and creates no obligation.
Key Takeaways
CMMC readiness requires tight alignment between policies, implemented controls, and real-world practices, as assessors validate that security measures operate exactly as documented.
Effective preparation starts early with accurate scoping, clear system boundaries, and well-organized evidence mapped directly to CMMC and NIST SP 800-171 requirements.
The assessment evaluates controls through documentation review, personnel interviews, and technical validation, making consistent execution across all three critical for success.
Staff at every level must understand their security responsibilities, as assessors rely on interviews to confirm that procedures are actively followed, not just written.
Technical gaps are a common risk, so organizations should proactively test configurations, logging, encryption, and access controls before the assessment begins.
Successful organizations manage findings strategically by addressing gaps quickly, using POA&Ms appropriately, and planning for ongoing compliance beyond initial certification.
How databrackets Can Help In Your CMMC Journey
databrackets is an authorized C3PAO and independent consulting organization for CMMC. We offer Certification OR Readiness and Consulting services for CMMC. To avoid a conflict of interest and abide by CMMC’s independence requirements, we do not offer both services to the same client.
We are an ideal partner for either service since we bring over 15 years of proven expertise in helping organizations achieve compliance or certification with the most rigorous cybersecurity and data privacy standards, including ISO 27001, SOC 2, HIPAA, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, and CMMC. We are an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
Schedule a Consultation to work with us as your C3PAO for CMMC Certification or as your Compliance Partner to help you prepare for it.
A. Why Choose databrackets as your C3PAO
1. Proven Multi-Framework Expertise
What makes databrackets particularly valuable is our extensive experience across complementary frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and NIST Cybersecurity Framework. We are also an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
This breadth of knowledge enables our assessment teams to understand how CMMC controls integrate with your existing compliance efforts and identify synergies that strengthen your overall security posture.
2. Technical Environment Proficiency
databrackets’ assessment team of CCAs and CCPs has the specialized technical competence essential for accurate CMMC evaluations. Our experience spans diverse technological environments, from traditional on-premises infrastructures to complex cloud deployments, ensuring we can effectively assess whatever technical landscape your organization operates in.
3. Strategic Timeline Management
With proven capability in managing sophisticated assessments spanning the typical 4–8-week timeframe, databrackets understands how to minimize disruption to your operations while ensuring comprehensive evaluation of all 110 NIST SP 800-171 security controls.
As a authorized C3PAO with extensive cybersecurity and compliance experience, databrackets offers a deep understanding of the CMMC assessment process. This comprehensive expertise enables us to conduct thorough assessments with clear explanations of findings and methodologies, resulting in more insightful evaluations for organizations seeking certification.
To inquire about our C3PAO Services, contact our team at sales@databrackets.com or schedule a free consultation.
B. Why Choose databrackets for Your CMMC Compliance Journey
We specialize in transforming CMMC compliance from a daunting obstacle into a strategic business enabler.
Proven Track Record: Over 14 years supporting organizations across diverse industries with complex compliance requirements
Comprehensive Approach: End-to-end support from initial assessment through ongoing compliance
Industry Recognition: Authorized certifying body for ISO 27001 and 3PAO for FedRAMP
Strategic Partnership: We don’t just help you achieve compliance—we help you leverage it for competitive advantage.
Our Comprehensive CMMC Compliance Services include:
Strategic Planning & Assessment:
CMMC readiness assessments and comprehensive gap analysis
CUI system boundary definition and scoping guidance
Network architecture documentation and CUI flow diagrams
Risk assessment and vendor compliance evaluations
Implementation & Documentation Support:
System Security Plan (SSP) development and customization
Complete policy and procedure documentation suite
FIPS validation documentation and shared control matrices
Evidence collection strategies and management systems
Assessment Preparation:
Mock assessments and readiness validation
CMMC documentation optimization and organization
Personnel training and assessment preparation
C3PAO coordination and selection support
Ongoing Compliance:
Continuous monitoring and compliance maintenance
Annual affirmation support and triennial assessment preparation
Change management and configuration control guidance
Customized CUI awareness training programs
Schedule a Consultation to understand how we can customize our services to meet your specific CMMC requirements and timeline.
For immediate assistance with your CMMC compliance journey, contact our certified experts at sales@databrackets.com or schedule a free consultation.
Helpful Resources:
https://databrackets.com/blog/how-to-select-the-right-c3pao-for-your-cmmc-certification/
https://databrackets.com/blog/cmmc-compliance-versus-certification/
https://databrackets.com/blog/your-cmmc-roadmap/
Summary
To summarize,
This blog about preparing for CMMC certification is a structured, organization-wide effort that goes far beyond completing documentation. It requires aligning policies, technical controls, and daily operational practices so that security measures are consistently implemented and demonstrable under assessment.
Successful preparation begins with early planning, accurate scoping, and clear ownership of systems and data handling processes. Organizing evidence, validating configurations, and ensuring staff understand their security responsibilities reduces assessment risk and prevents last-minute gaps.
The assessment itself evaluates documentation, interviews, and technical validation together, meaning weaknesses in any area can affect outcomes. Organizations that test controls in advance, train personnel effectively, and address gaps proactively are better positioned to achieve certification.
CMMC should be viewed as an ongoing compliance commitment rather than a one-time milestone. Continuous monitoring, disciplined change management, and regular internal reviews help maintain certification readiness and support long-term cybersecurity maturity.
Srini Kolathur
Srini is the Director of databrackets.com. He is a results-driven security and compliance professional with over 25 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, CMMC, FedRAMP, NIST Security Standards, HIPAA, Security Risk Assessments, among others. His accreditations include Certified CMMC Assessor, CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE. He has verified all the technical information in this blog and co-authored it with Aditi Salhotra.