CMMC is not just about having the right tools and controls in place—it’s about proving it. Documentation serves as your organization’s evidence that your security processes are not only implemented but are also repeatable and they mature over time. It serves as the critical bridge between what you do and what you can prove. It is the basis of the trust clients place in you.
As a Certified CMMC Registered Practitioner Organization (RPO), we’ve guided diverse organizations through the certification journey, and one truth remains constant: documentation is not merely administrative overhead but rather the foundation of sustainable compliance. Your documentation ecosystem demonstrates that security practices are not ad-hoc efforts but deliberate, repeatable processes that mature over time.
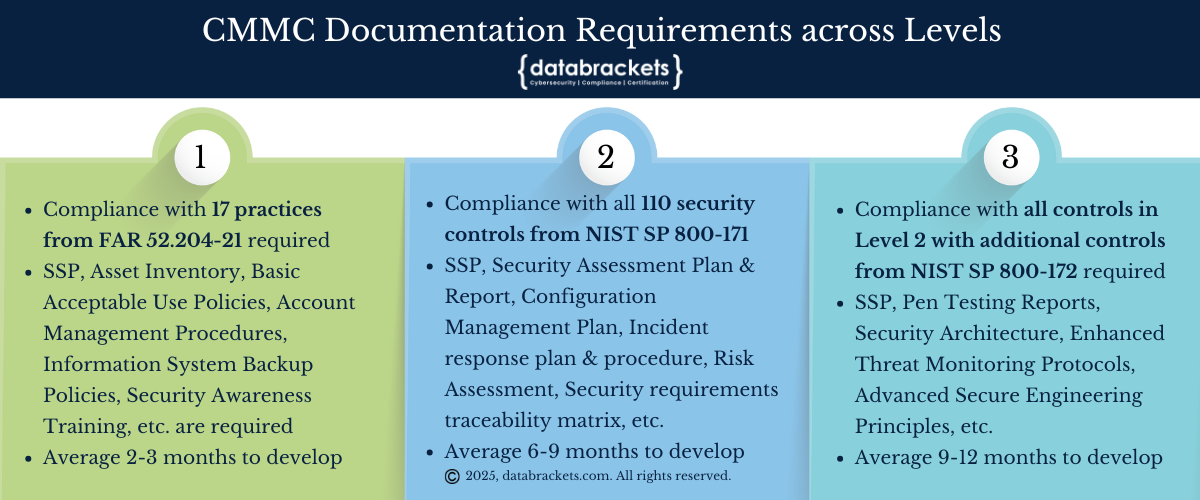
CMMC Documentation Requirements across Levels
CMMC Level 1: Foundational Cyber Hygiene
At Level 1, organizations must address 17 practices from FAR 52.204-21. While this level allows for annual self-assessments, documentation remains crucial:
Essential Documents for Level 1:
System Security Plan (SSP) documenting security requirements, system boundaries, and operational environment
Asset inventory including hardware, software, and network components
Basic acceptable use policies
Account management procedures
Information system backup policies
Security awareness training materials
Development Timeline: For Level 1, we recommend allocating approximately 2-3 months for documentation development.
CMMC Level 2: Advanced Cyber Hygiene
Level 2 compliance addresses 110 practices across 14 domains aligned with NIST SP 800-171 and requires more robust documentation:
Essential Documents for Level 2:
Comprehensive System Security Plan with detailed control implementations
Security Assessment Plan and Report
Configuration management plan
Incident response plan and procedures
Risk assessment documentation
Security requirements traceability matrix
Continuous monitoring strategy
Development Timeline: Level 2 documentation typically requires 6-9 months of development. Organizations should establish a dedicated compliance team with representation from IT, operations, and management. We recommend allocating at least one full-time equivalent (FTE) resource for organizations with up to 250 employees, and additional resources for larger organizations.
Practice-to-Documentation Mapping
Here’s a snapshot of typical documentation required across a few core domains:
Domain | Practice Example | Essential Documentation |
Access Control | Limit system access to authorized users | Access control policy, user provisioning procedure, access review logs, role definitions |
Incident Response | Establish operational incident-handling capability | Incident Response Plan, detection procedures, post-incident review templates, communication protocols |
Risk Management | Periodically assess risk to organizational operations | Risk Assessment methodology, Risk Register, vulnerability management procedure, treatment plans |
Configuration Management | Establish baseline configurations | Configuration Management Plan, baseline templates, change management logs, configuration review records |
CMMC Level 3: Expert Cyber Hygiene (Reserved for Critical Systems)
Level 3 builds upon Level 2 by adding practices from NIST SP 800-172, requiring sophisticated documentation:
Essential Documents for Level 3:
Enhanced SSP with advanced security implementations
Security architecture documentation
Supply chain risk management plan
Advanced threat detection and response procedures
Personnel security documentation
Security Engineering principles documentation
Penetration testing reports
Development Timeline: Level 3 documentation development typically spans 9-12 months and requires specialized expertise. Organizations should allocate 2-3 FTE resources with cybersecurity expertise, supplemented by external consultants with specific domain knowledge.
System Security Plan (SSP): The Cornerstone Document
The System Security Plan (SSP) serves as the central document in your CMMC documentation suite. A properly developed SSP:
1. Defines System Boundaries: Clearly articulates what is in-scope and out-of-scope for certification
2. Maps Control Implementation: Documents how each CMMC requirement is addressed
3. Identifies Responsibilities: Clarifies organizational roles in maintaining security
4. References Supporting Documentation: Creates a cohesive documentation ecosystem
A well-crafted SSP includes:
System characterization with clear boundaries
Data flow diagrams illustrating CUI pathways
Organizational security roles and responsibilities
Detailed control implementation statements
References to supporting documentation
System interconnection details
Status of each security requirement
Rather than seeing the SSP as a single document, consider it a navigational guide that points to your broader documentation environment—policies, procedures, configurations, and evidence. Learn How to create an SSP for CMMC & avoid the pitfalls. If you would like to receive a free SSP Template, you can email us at sales@databrackets.com.
SSP Development Best Practices:
Begin with a comprehensive system inventory and data flow mapping
Document both technical and non-technical controls
Include implementation status for each control
Reference specific policies, procedures, and configurations
Update regularly as systems or processes change
CMMC Evidence Collection and Management
Documentation must be supported by evidence demonstrating that controls are implemented as described. Effective evidence collection requires:
Evidence Management System: We recommend implementing a dedicated compliance management tool that:
Maps evidence to specific CMMC practices
Tracks evidence collection status
Maintains evidence history
Supports assessment workflow
Automates evidence refresh cycles
Types of Evidence to Collect for CMMC:
Implementation Evidence: Configuration screenshots, system-generated reports
Process Evidence: Completed forms, approval records, meeting minutes
Effectiveness Evidence: Audit logs, test results, security metrics
Evidence Collection Cadence:
High-volatility controls (e.g., access reviews): Monthly collection
Medium-volatility controls (e.g., security configurations): Quarterly collection
Low-volatility controls (e.g., physical security): Semi-annual collection
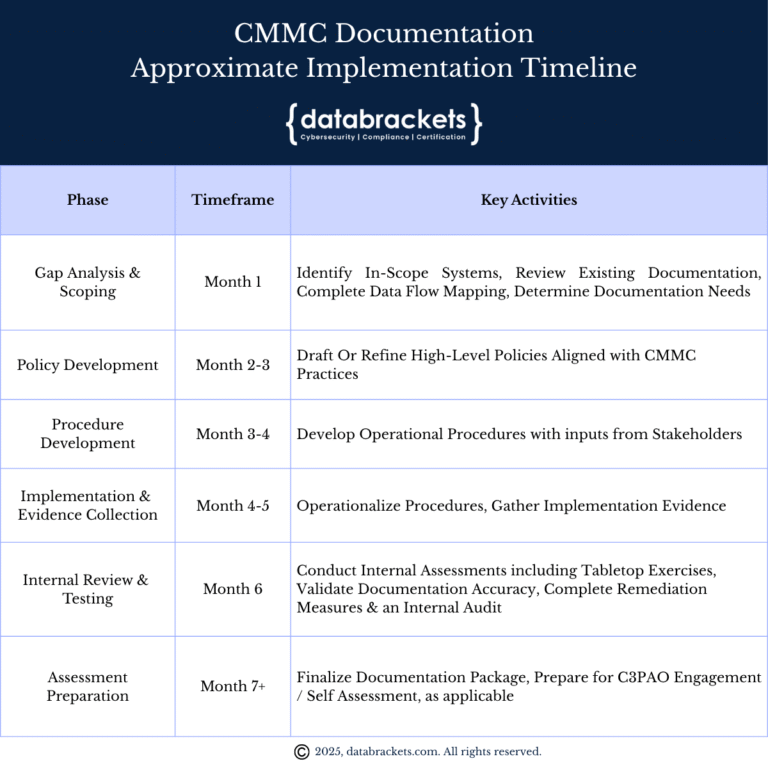
CMMC Documentation: Approximate Implementation Timeline
Based on our implementation experience, organizations should approach documentation development according to the approximate timeline in the table below.
Small organizations may compress this timeline, while larger enterprises with complex environments might need additional time, particularly for procedure development and evidence collection.
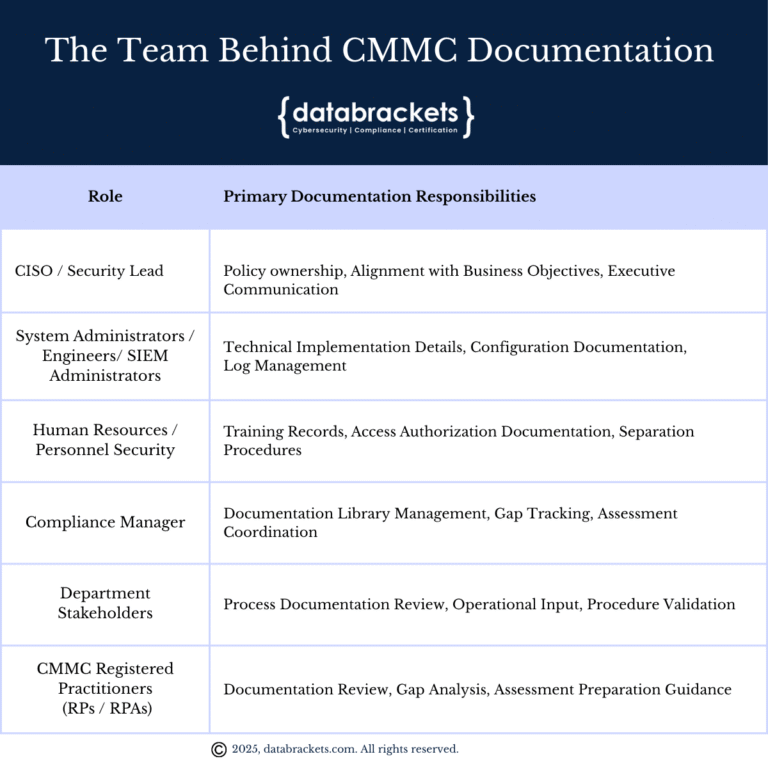
The Team Behind CMMC Documentation
Effective documentation requires cross-functional involvement. We recommend establishing the key roles in the table below.
During initial development, we recommend that you allocate approximately 20-30% of your compliance team’s time to documentation efforts. Once established, ongoing maintenance typically requires 10-15% of allocated resources.
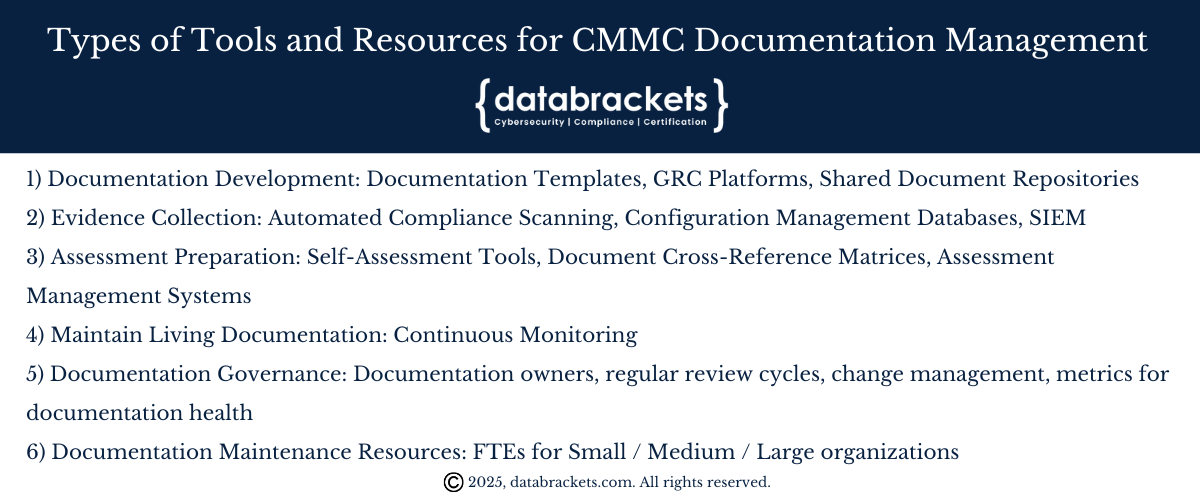
Tools and Resources for CMMC Documentation Management
Based on our implementation experience, the information in the infographic can significantly enhance documentation efficiency
Documentation Development:
GRC Platforms: Compliance management systems with built-in CMMC frameworks
Shared Document Repositories: Cloud-based collaboration tools with version control
Documentation Templates: CMMC-specific templates aligned with assessment guidance
Evidence Collection:
Automated Compliance Scanning: Tools that generate and capture compliance evidence
Security Information and Event Management (SIEM): For centralized log collection and analysis
Configuration Management Databases: For maintaining accurate system inventory
Assessment Preparation:
Self-Assessment Tools: Internal review capabilities aligned with CMMC Assessment Guides
Document Cross-Reference Matrices: Mapping evidence to specific CMMC practices
Assessment Management Systems: Platforms for managing assessment workflow
Maintaining Living Documentation: CMMC documentation is not a one-time project but a continuous program.
Documentation Governance:
Appoint documentation owners for each major document category
Establish regular review cycles (typically quarterly for procedures, annually for policies)
Implement a change management process for documentation updates
Conduct periodic tabletop exercises to validate documentation accuracy
Establish metrics for documentation health (coverage, freshness, accuracy)
Documentation Maintenance Resources: For ongoing documentation maintenance, organizations typically need to allocate:
Small organizations (< 25 employees): 0.1-0.25 FTE
Medium organizations (25-500 employees): 0.5-1 FTE
Large organizations (> 500 employees): 1-3 FTE
Technology Enablers for CMMC Documentation Excellence
When selecting technology for CMMC documentation, organizations must prioritize solutions appropriate for CUI protection. The right tools enhance development, management, and assessment preparation while maintaining proper security controls:
GRC Platforms specifically designed for CMMC and federal compliance:
Xacta by Telos (purpose-built for government compliance)
Archer (with FedRAMP authorization)
ComplyUp (CMMC-focused compliance management)
Exostar’s CMMC Compliance solution
Policy Management Systems appropriate for CUI environments:
PowerDMS (with appropriate security configurations)
ConvergePoint (leveraging secure SharePoint deployments)
Microsoft 365 GCC for document management
Secure Evidence Collection tools with appropriate federal authorizations:
SIEMs: Splunk Government or IBM QRadar (FedRAMP authorized versions)
Vulnerability management: Tenable.gov or Qualys FedRAMP offerings
Configuration management: Microsoft SCCM or Ansible Automation Platform (properly secured)
Secure diagramming: Microsoft Visio with appropriate storage controls
Documentation Collaboration solutions suitable for CUI :
Microsoft Teams/SharePoint GCC environments
FedRAMP-authorized collaboration platforms
For organizations handling CUI, standard commercial or cloud-based solutions often require special configurations or may be entirely unsuitable. When evaluating any technology for CMMC documentation management, verify FedRAMP authorization status or equivalent security controls designed specifically for CUI protection.
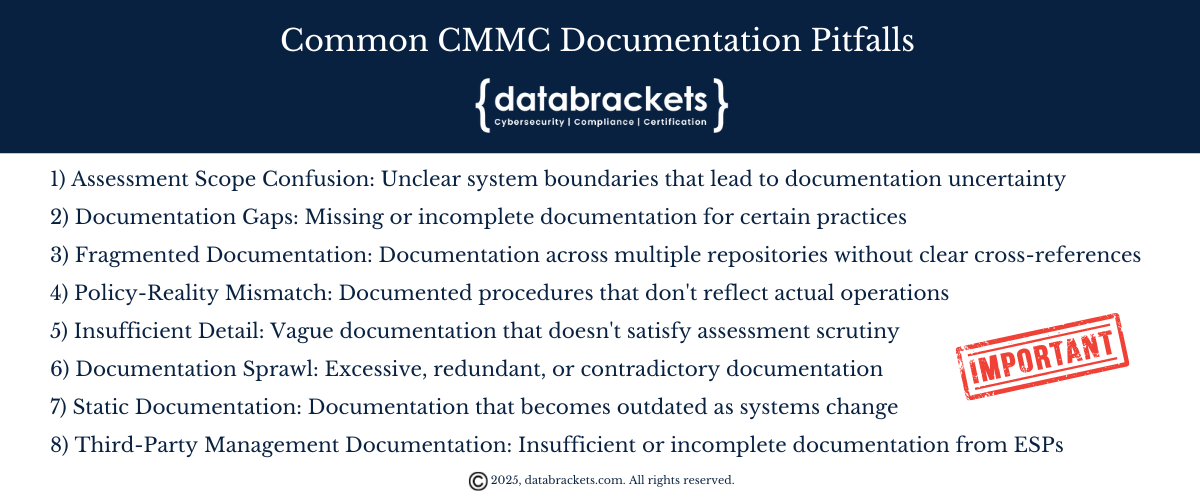
Common CMMC Documentation Pitfalls and Solutions
Based on our experience guiding organizations through certification, here are critical pitfalls to avoid:
1. Assessment Scope Confusion
Pitfall: Unclear system boundaries that lead to documentation uncertainty
Solution: Begin your documentation journey with precise boundary definition and data flow mapping to ensure appropriate scope. Create a visual system boundary diagram that clearly delineates CUI environments from general business systems.
2. Documentation Gaps
Pitfall: Missing or incomplete documentation for certain practices
Solution: Develop a comprehensive requirements traceability matrix that maps each CMMC practice to specific documentation.
3. Fragmented Documentation
Pitfall: Documentation that exists across multiple repositories without clear cross-references leading to gaps
Solution: Establish a centralized documentation index that maps each requirement to specific documents, regardless of storage location. Tools like document management systems with tagging capabilities or even a well-structured spreadsheet can serve as this critical index.
4. Policy-Reality Mismatch
Pitfall: Documented procedures that don’t reflect actual operations
Solution: Involve operational staff in documentation development and regularly validate that documentation matches implementation
5. Insufficient Detail
Pitfall: Vague documentation that doesn’t satisfy assessment scrutiny
Solution: Include specific configurations, responsibilities, and implementation details in all documentation
6. Documentation Sprawl
Pitfall: Excessive, redundant, or contradictory documentation
Solution: Implement a documentation hierarchy with clear cross-references between related documents
7. Static Documentation
Pitfall: Documentation that becomes outdated as systems change
Solution: Integrate documentation review into change management processes. Implement evidence refresh cycles based on volatility—reviewing authentication configurations quarterly. Create an “evidence calendar” that schedules refresh activities throughout the year to prevent assessment-time scrambling.
8. Third-Party Management Documentation
Pitfall: Insufficient or incomplete documentation from ESPs and other vendors in your supply chain.
Solution: Develop standardized questionnaires, contract language, and monitoring procedures for vendors with access to your systems or CUI. Document your vendor assessment methodology and maintain evidence of regular vendor security reviews. Ensure you follow proper protocols for documentation to be submitted by ESPs (External Service Providers). ESPs include CSPs, MSPs and MSSPs in the CMMC Ecosystem.
CMMC Documentation as Strategic Investment
The better documented your controls are, the more consistent, scalable, and defensible your cybersecurity posture becomes. The CMMC documentation you develop delivers value far beyond compliance:
It enhances operational consistency by establishing clear expectations
It accelerates incident response through documented procedures
It simplifies onboarding by providing clear security guidance
It builds institutional knowledge that persists through staff changes
It demonstrates security diligence to partners and customers
As Certified CMMC Registered Practitioners, we’ve seen how organizations that invest in developing comprehensive, practical documentation not only achieve certification more efficiently but also experience tangible operational benefits. Well-structured documentation provides clarity, consistency, and continuity that extends far beyond the assessment process.
The documentation journey requires significant investment in time and resources, but when executed with proper planning and expertise, it yields returns that extend throughout your organization’s security program and operational efficiency.
By embracing documentation as a cornerstone of your security program rather than merely a compliance checkbox, your organization can build a foundation for cybersecurity excellence that supports not just certification goals, but broader business objectives in an increasingly threatening digital landscape.
Key Takeaways
Documentation for CMMC must demonstrate repeatable, consistent security practices rather than just describing tools or isolated controls, because assessors look for evidence that cybersecurity processes are embedded and operational over time.
Even for CMMC Level 1, where self-assessment suffices, foundational artifacts like the System Security Plan (SSP), asset inventories, and key policy documents are necessary to substantiate compliance rather than being optional paperwork.
Assigning clear roles across cybersecurity, IT, and business units ensures that CMMC documentation reflects actual practice ownership. This prevents gaps between written procedures and what your organization actually does.
Planning CMMC documentation creation and maintenance as a distinct workstream with dedicated resource allocation reduces last-minute rushes and improves quality, because ongoing maintenance becomes significantly less burdensome once the baseline is established.
Treating CMMC documentation “as evidence” rather than “as an archive” shifts your perspective toward collecting verifiable artifacts and records that substantiate control implementation during assessments.
Using tools and templates to manage document versioning, evidence logs, and cross-referencing between policies and controls helps ensure consistency and supports assessors’ expectations for organized, audit-ready records.
Anticipating common pitfalls—such as fragmented documentation, ambiguous procedures, or mismatches between policy and practice—enables teams to remediate them early, saving time in preparation and reducing risks of assessment delays.
How databrackets can help you with your CMMC Journey
databrackets is an authorized C3PAO and independent consulting organization for CMMC. We offer Certification OR Readiness and Consulting services for CMMC. To avoid a conflict of interest and abide by CMMC’s independence requirements, we do not offer both services to the same client.
We are an ideal partner for either service since we bring over 15 years of proven expertise in helping organizations achieve compliance or certification with the most rigorous cybersecurity and data privacy standards, including ISO 27001, SOC 2, HIPAA, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, and CMMC. We are an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
Schedule a Consultation to work with us as your C3PAO for CMMC Certification or as your Compliance Partner to help you prepare for it.
A. Why Choose databrackets as your C3PAO
1. Proven Multi-Framework Expertise
What makes databrackets particularly valuable is our extensive experience across complementary frameworks, including NIST SP 800-171, NIST SP 800-53, SOC 2, ISO 27001, HIPAA, and NIST Cybersecurity Framework. We are also an authorized certifying body for ISO 27001 and 3PAO for FedRAMP.
This breadth of knowledge enables our assessment teams to understand how CMMC controls integrate with your existing compliance efforts and identify synergies that strengthen your overall security posture.
2. Technical Environment Proficiency
databrackets’ assessment team of CCAs and CCPs has the specialized technical competence essential for accurate CMMC evaluations. Our experience spans diverse technological environments, from traditional on-premises infrastructures to complex cloud deployments, ensuring we can effectively assess whatever technical landscape your organization operates in.
3. Strategic Timeline Management
With proven capability in managing sophisticated assessments spanning the typical 4–8-week timeframe, databrackets understands how to minimize disruption to your operations while ensuring comprehensive evaluation of all 110 NIST SP 800-171 security controls.
As a authorized C3PAO with extensive cybersecurity and compliance experience, databrackets offers a deep understanding of the CMMC assessment process. This comprehensive expertise enables us to conduct thorough assessments with clear explanations of findings and methodologies, resulting in more insightful evaluations for organizations seeking certification.
To inquire about our C3PAO Services, contact our team at sales@databrackets.com or schedule a free consultation.
B. Why Choose databrackets for Your CMMC Compliance Journey
We specialize in transforming CMMC compliance from a daunting obstacle into a strategic business enabler.
Proven Track Record: Over 15 years supporting organizations across diverse industries with complex compliance requirements
Comprehensive Approach: End-to-end support from initial assessment through ongoing compliance
Industry Recognition: Authorized certifying body for ISO 27001 and 3PAO for FedRAMP
Strategic Partnership: We don’t just help you achieve compliance—we help you leverage it for competitive advantage.
Our Comprehensive CMMC Compliance Services include:
1. Strategic Planning & Assessment:
CMMC readiness assessments and comprehensive gap analysis
CUI system boundary definition and scoping guidance
Network architecture documentation and CUI flow diagrams
Risk assessment and vendor compliance evaluations
2. Implementation & Documentation Support:
System Security Plan (SSP) development and customization
Complete policy and procedure documentation suite
FIPS validation documentation and shared control matrices
Evidence collection strategies and management systems
3. Assessment Preparation:
Mock assessments and readiness validation
CMMC documentation optimization and organization
Personnel training and assessment preparation
C3PAO coordination and selection support
4. Ongoing Compliance:
Continuous monitoring and compliance maintenance
Annual affirmation support and triennial assessment preparation
Change management and configuration control guidance
Customized CUI awareness training programs
For immediate assistance with your CMMC compliance journey, contact our certified experts at sales@databrackets.com or schedule a free consultation.
Helpful Resources:
Summary
To summarize,
CMMC documentation functions as evidence of security practice maturity, showing not only that controls exist on paper but also that they are consistently executed and maintained across your organization.
The requirements vary by certification level, with Level 1 emphasizing foundational cyber hygiene and self-assessment artifacts, and higher levels demanding comprehensive process documentation, evidence logs, and formalized policy suites.
Effective documentation must reflect how your organization actually operates, which means aligning written procedures with everyday practices and eliminating discrepancies between what is documented and what is implemented.
Building documentation is a team effort that benefits from clear role ownership, ensuring that stakeholders from security, IT, and business units contribute accurate content and own ongoing maintenance responsibilities.
Investing in tools and structured templates that support version control, evidence indexing, and cross-referencing improves documentation quality and makes audit readiness more manageable.
Anticipating and addressing common pitfalls—such as fragmented records, unclear procedures, and gaps between policy and practice—reduces assessment friction and helps prevent certification delays.
Treating documentation as a living set of artifacts, with planned upkeep and evidence updates over time, positions your compliance efforts for both initial certification and ongoing adherence to CMMC expectations.