We, at databrackets, have compared popular security standards and frameworks (mandatory and voluntary). Our analysis focuses on practical aspects you need to consider before implementing the controls under each framework.
To begin our comparison, we looked at Google Trends for the interest in these security frameworks over the last decade.
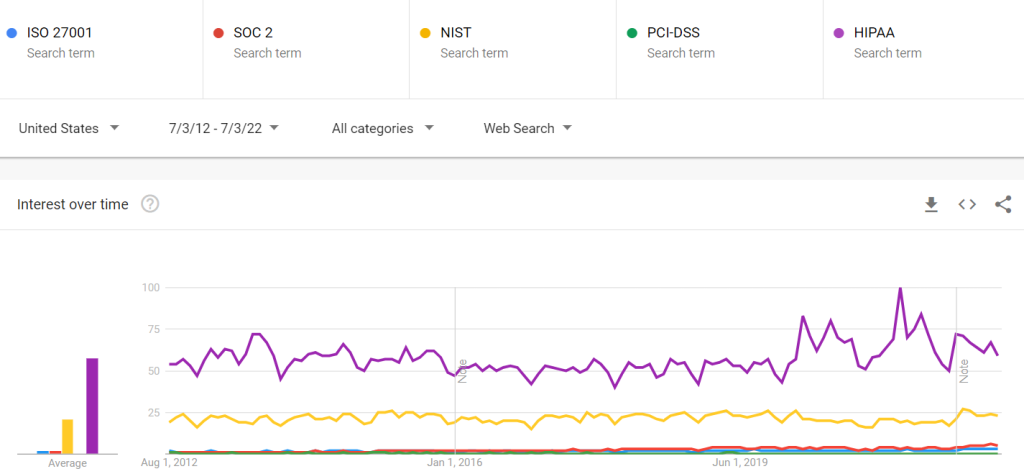
Comparing Security Frameworks
The comparison parameters in the charts below focus on the information you need to get an overview of the security standards and their relevance to your organization.
Key Features | ISO 27001 | SOC 2 | NIST Standards | PCI-DSS | HIPAA / HITECH | Other Standards/ Frameworks (including FedRamp, CSA, HITRUST, Shared Assessments, etc.) | Notes |
|---|---|---|---|---|---|---|---|
Certification | Yes | Yes | Not Applicable. You can get attested for compliance by a third-party. | Yes | There is no agency authorized to certify HIPAA compliance. | Yes | You need to engage the certifying bodies/ approved vendors. |
Approach | Risk-based | Controls-based | Controls-based | Controls-based | Controls-based | Maps to individual frameworks of each standard body | |
Principle | Information Security Management Systems | Trust Services Criteria & Ethics | Control Families | PCIDSS standard | HIPAA rules including Technical, Administrative and Physical Safeguards | Depends on the individual frameworks of each standard | Technology platform specific controls are not covered by the standards /certification bodies |
Certification Method | Authorized Certification Bodies | Authorized CPA Firm (Readiness Assessment can be done by a vendor) | Self (Audit and Attestation can be done by a third-party) | Authorized firm who have PCI-QSA Certified | Self (Audit and Attestation can be done by a third-party) | Third-party vendors | Third-parties require accreditation to issue certification |
Best Suited For | Service Organization | Service/Product Organization | Different industries require different levels/standards of compliance | Service Organization | Healthcare, SaaS, and any organization handling Protected Health Information of US Citizens inclduing vendors handling PHI | Service/Product Organization | Some sort of security and data privacy certification is becoming a part of most industries |
Popular in … | International | Companies operating in North America | US Federal/ Commercial / Manufacturing | International | USA | Companies operating in North America | |
Customer Acceptance (Customer Requirements) | Preferred (Mandatory in some cases) | Preferred (Mandatory in some cases) | Not Mandated | Preferred (Mandatory in some cases) | Mandatory | Depends on the Industry and marketplace where business is conducted | |
Duration | Point-in-time | 6-month period(Type 2) | Point-in-time | 3-6 Months | Point-in-time | Point-in-time | Surveillance audit is in place for most of the certifications |
Certification Frequency | Every 3 years with annual surveillance audits | Annual | Not Applicable | Annual | Annual | Mostly Annual | |
Cost | $$ | $$$ | $$ | $$$ | $$ | $$$ (HITRUST certifications cost 50k -200k) | Engaging an experienced vendor helps to ensure documentation and audit support. This saves cost in the long run. |
Below is a quick summary of each security standard and framework:
NIST Security Standards are based on best practices from several security resources, organizations, and publications. They were designed as a framework for federal agencies and programs requiring security measures. Several non-federal agencies have also implemented these guidelines to showcase that they comply with authoritative security best practices.
NIST Special Publication 800–53 is the most popular among the NIST security series. It provides the steps in the Risk Management Framework for security control selection for federal information systems. This is in accordance with the security requirements in Federal Information Processing Standard (FIPS) 200. The NIST Cybersecurity Framework (NIST CSF) has also attracted a lot of interest and attention from a variety of industries.
NIST has released the final version of Special Publication (SP) 800–219, Automated Secure Configuration Guidance from the macOS Security Compliance Project (mSCP). Security Professionals can leverage the macOS Security Compliance Project (mSCP) to secure and assess macOS desktop and laptop system security in an automated manner.
ISO 27001, is a more risk-based standard for organizations of all shapes and sizes. Although there are more than a dozen standards in the ISO/IEC 27000 family, ISO/IEC 27001 is well known for defining the requirements for an information security management system (ISMS). ISO 27001 enables and empowers organizations of any kind to manage the security of assets such as financial information, intellectual property, employee details, or information entrusted to third parties. The latest update to ISO 27001 is scheduled to be released in late 2022.
reports assess the security controls of a Service Organization in accordance with AICPA’s Trust Services Principles: Security, Availability, Processing Integrity, Confidentiality and Privacy.
SOC 2 compliance is often included as the eligibility criteria for SaaS and other service providers as they bid for B2B contracts. Type 1 and Type 2 reports meet the needs of a broad range of B2B customers who want assurance about the security of their customer data.
HITRUST stands for the Health Information Trust Alliance. A HITRUST certification by the HITRUST Alliance enables vendors and covered entities to demonstrate compliance with HIPAA requirements based on a standardized framework.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a federal law that requires the creation of national standards to protect sensitive patient health information from being disclosed without the patient’s consent or knowledge.
The Department of Health and Human Services (HHS) Office of Civil Rights (OCR) allocated a proposed rule for changes to the act in December of 2020 and a Final Rule is expected in 2022 with the following changes:
Increased Patient Access — the HIPAA Right of Access into the HIPAA Privacy Rule allows individuals to be more in control of their health and well-being decisions, which includes but not limited to:.
- Allow patients to inspect the medical record PHI in person and/or take notes or photos
- Reduce the time needed to provide access to PHI from 30 to 15 days
- Allow patients to request a transfer of their PHI to personal health applications.
- To post estimated fee schedules for PHI access and disclosures
The Payment Card Industry Data Security Standard (PCI DSS) is a set of security standards governed by the Payment Card Industry Security Standards Council (PCI SSC). This framework has been designed to secure credit and debit card transactions against data theft. PCI-DSS is a requirement for any organization that processes credit or debit card transactions. PCI certification is also considered the best way to safeguard sensitive data and information.
The Consensus Assessments Initiative Questionnaire (CAIQ) v3.1. offers an industry-accepted way to document what security controls exist in IaaS, PaaS, and SaaS services, providing security control transparency. It provides a set of objective questions to a cloud provider to ascertain their compliance with the Cloud Controls Matrix (CCM).
The Federal Risk and Authorization Management Program (FedRAMP) is a government-wide program in the US that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services. FedRAMP enables agencies to rapidly adapt old, insecure legacy IT to mission-enabling, secure, and cost-effective cloud-based IT.
Shared Assessments provide the best practices, solutions, and tools for third-party risk management to create an environment of assurance for outsourcers and their vendors.
How databrackets can help you comply with security regulations
databrackets specializes in assisting organizations to secure sensitive data and comply with regulatory requirements. By leveraging databrackets’ SaaS assessment platform, awareness training, and policies & procedures, our customers and partners are meeting the growing demands for data security and evolving compliance requirements more efficiently. Contact us here to learn more.