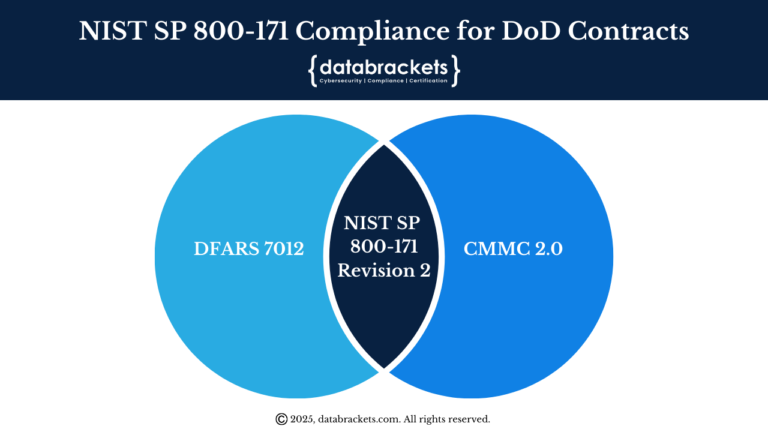
With the upcoming phase-in of the Cybersecurity Maturity Model Certification (CMMC), it’s crucial for contractors to understand the existing regulatory framework, DFARS 7012, which mandates cybersecurity controls for protecting Controlled Unclassified Information (CUI). Before CMMC becomes a requirement in your DoD contract, you need to understand how NIST SP 800-171 Revision 2 is the source for DFARS 7012 & CMMC. Hence, by implementing NIST SP 800-171 Revision 2, you will be poised to bid on a DoD Contract.
Security experts at databrackets have over 12 years of experience in helping organizations meet cybersecurity and data privacy regulatory requirements across a wide variety of standards including ISO 27001:2022, SOC 2, HIPAA, etc. We are also an authorized RPO for CMMC with expertise in helping organizations comply with NIST SP 800-171 Revision 2. We have curated this blog to help organizations understand how structuring their investment in security technology and aligning their security practices with NIST SP 800-171 will help them bid for DoD contracts and be in a position to meet any POA&Ms that may be additionally required by the DoD.
Overview of DFARS 7012
DFARS 7012 (Defense Federal Acquisition Regulation Supplement 7012) is a crucial regulation within the U.S. Department of Defense (DoD) procurement process. It focuses on protecting sensitive defense information, particularly regarding cybersecurity and the safeguarding of Controlled Unclassified Information (CUI). The regulation mandates specific cybersecurity requirements for contractors and subcontractors who handle CUI, ensuring that these entities implement adequate security measures to prevent data breaches and cyber threats that could impact national security.
To Whom DFARS 7012 Applies
DFARS 7012 applies primarily to DoD contractors and subcontractors who handle CUI as part of their contracts. This includes entities involved in defense-related projects, research, and technology development, as well as those providing goods and services directly to the DoD. The regulation applies to both large and small businesses, though small businesses may be subject to some flexibility in terms of compliance expectations.
In particular, DFARS 7012 impacts:
Prime contractors working with the DoD
Subcontractors within the defense supply chain who may have access to or store CUI
Contractors performing tasks such as IT services, cloud services, and software development for DoD-related work
Complying with DFARS 7012
To comply with DFARS 7012 (Defense Federal Acquisition Regulation Supplement 7012), an organization must undertake a series of key activities to ensure cybersecurity and protect Controlled Unclassified Information (CUI) within the Department of Defense (DoD) supply chain. Below is a checklist of actions that an organization should consider:
To ensure compliance with DFARS (Defense Federal Acquisition Regulation Supplement) 7012, organizations must adopt various cybersecurity practices aimed at safeguarding Controlled Unclassified Information (CUI). The following checklist outlines key activities, including the System Security Plan (SSP), that should be undertaken.

Understand DFARS 7012 Requirements
Review DFARS Clause 252.204-7012 to understand the specific cybersecurity requirements and obligations regarding CUI protection.
Identify CUI within your organization and determine where it is stored, processed, or transmitted.
Implement NIST SP 800-171 Revision 2 Controls
Assess cybersecurity posture and identify gaps against the NIST SP 800-171 Revision 2 standards, which DFARS 7012 mandates.
Implement the 14 families of controls outlined in NIST SP 800-171 Revision 2 (e.g., access control, system integrity, incident response, etc.).
Develop & Maintain a System Security Plan (SSP)
Develop an SSP to describe the organization’s security requirements, the controls implemented, and any planned improvements.
Ensure that the SSP details all system components, including hardware, software, and personnel involved in handling CUI.
Review and update the SSP regularly to reflect any changes in security controls or system configurations.
Ensure your SSP is aligned with the NIST SP 800-171 Revision 2 controls and that it’s accessible for audits or inspections by the DoD.
- Conduct Risk Assessments
- Perform risk assessments to identify potential vulnerabilities to CUI and determine the effectiveness of implemented controls.
- Update security measures based on assessment findings to mitigate identified risks.
- Report Cybersecurity Incidents
- Establish and test your incident response plan to address any security breaches or attacks involving CUI.
- If you have a cybersecurity incident, ensure that you report it to the DoD within 72 hours, as required by DFARS 7012, and document all actions taken.
- Provide Cybersecurity Training
- Train employees on cybersecurity best practices, including proper handling and protection of CUI.
- Offer regular refresher training to ensure staff remain aware of evolving threats and compliance requirements.
- Implement Continuous Monitoring and Logging
- Implement continuous monitoring of all systems handling CUI to detect and respond to security threats in real-time.
- Maintain logs of system activity and security events for auditing and forensic purposes.
- Secure Third-Party Relationships
- Evaluate third-party vendors who access CUI to ensure they comply with DFARS 7012 cybersecurity standards.
- Incorporate cybersecurity clauses into contracts with suppliers and subcontractors, ensuring they understand their obligations regarding CUI protection.
- Mark CUI and Establish Handling Procedures
- Establish protocols for marking and identifying CUI in compliance with DoD standards.
- Implement proper procedures for the secure handling, storage, transmission, and disposal of CUI in both digital and physical formats.
- Implement a Compliance Auditing System
- Regularly audit cybersecurity practices and document compliance with DFARS 7012 and NIST SP 800-171.
- Ensure audit findings are addressed, and corrective actions are documented and implemented.
- Prepare for CMMC 2.0 (Cybersecurity Maturity Model Certification)
- Prepare for CMMC 2.0 certification, which will be required in future DoD contracts, ensuring your organization meets the necessary maturity levels.
- Conduct periodic self-assessments to ensure alignment with CMMC and DFARS 7012.
- Implement a Data Backup and Recovery Plan
- Develop and test a disaster recovery and business continuity plan to ensure that CUI can be restored swiftly and accurately in the event of a cyber incident or disaster.
- Ensure all backup systems are secure and regularly tested to verify their reliability.
- Maintain Detailed Documentation
- Keep comprehensive records of all cybersecurity measures, incident reports, training activities, and audits.
- Ensure that documentation is updated regularly and available for inspection by DoD or auditors as required.
CMMC 2.0 and DFARS 7012
With the introduction of the Cybersecurity Maturity Model Certification (CMMC) 2.0 rule, there is a shift in how the Department of Defense (DoD) will assess and enforce cybersecurity requirements for defense contractors. However, DFARS 7012 remains an important regulation, especially in the transition period.
Both CMMC 2.0 and DFARS 7012 are based on the cybersecurity requirements outlined in NIST SP 800-171 Revision 2. Hence, complying with NIST SP 800-171 Revision 2 is the essential starting point for both frameworks, as it establishes the baseline security controls required to protect Controlled Unclassified Information (CUI).
When Does CMMC 2.0 Take Precedence Over DFARS 7012?
The CMMC 2.0 rule is scheduled to become the new cybersecurity standard across the defense industrial base. It will introduce a more rigorous, multi-level certification system for contractors, replacing the previous reliance on self-assessments for compliance with NIST SP 800-171 Revision 2 as mandated by DFARS 7012.
CMMC 2.0 Requirements: As CMMC 2.0 is phased in, contractors who want to work with the DoD will need to be certified at the appropriate CMMC level (Level 2 or Level 3) to win certain DoD contracts. Contracts with Level 1 CMMC Compliance will continue to require self-attestations with stricter regulations.
Contract Language and Transition: The shift to CMMC 2.0 will be implemented through contract language. Once a contract specifically requires CMMC certification as part of its terms, DFARS 7012’s requirements will not apply, and the contractor will be subject to the CMMC certification or an updated self-attestation process instead.
Complying with DFARS 7012 & CMMC 2.0 by being NIST Compliant
Adhering to the guidelines of NIST SP 800-171 Revision 2 is a proactive step for organizations aiming to bid on Department of Defense (DoD) contracts. Compliance not only aligns your cybersecurity posture with federal requirements but also ensures readiness for both DFARS 7012 obligations and the Cybersecurity Maturity Model Certification (CMMC). By meeting these standards, your organization will be better positioned to secure contracts and demonstrate a commitment to safeguarding sensitive information, giving you a competitive edge in the defense contracting space.
How databrackets can help you comply with DFARS 7012,
NIST SP 800-171 & CMMC 2.0
At databrackets, we bring over 12 years of proven expertise in helping organizations achieve compliance with some of the most rigorous cybersecurity and data privacy standards, including ISO 27001:2022, SOC 2, HIPAA, and more. As an authorized Registered Provider Organization (RPO) for CMMC , we specialize in assisting organizations to navigate the complexities of NIST SP 800-171 Revision 2, a critical component for securing Department of Defense (DoD) contracts.
Given below is our comprehensive suite of deliverables to help you prove your compliance with CMMC 2.0
Readiness & Implementation Support
Network Diagram
CUI Flow Diagram
CUI System Boundary
FIPS Validation Diagram
Shared control matrix
SSP
Customized Information Security Policy
Data Breach Policy
Vulnerability Scan Report
Vendor Compliance Assessment
Advisory Services and Audit Support
Customized CUI Awareness Training (Optional / On-Demand)
Other Customized Policies & Procedures
Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Overview of databrackets
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc. We are an authorized certifying body for ISO 27001 and a Registered Practitioner Organization for CMMC. We are also a candidate C3PAO organization for CMMC awaiting our DIBCAC Audit. We have partnerships to help clients prepare for and obtain other security certifications. We are constantly expanding our library of assessments and services to serve organizations across industries.
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.