In today’s defense contracting landscape, cybersecurity compliance has become non-negotiable. With the Department of Defense (DoD) implementing the Cybersecurity Maturity Model Certification (CMMC) framework, contractors handling sensitive information must demonstrate robust security practices. At the heart of this compliance effort lies the System Security Plan (SSP) – a critical document that serves as the foundation for your CMMC certification journey.
This blog will walk you through the process of creating an effective SSP for CMMC, breaking down the essential components, key roles and responsibilities, and practical implementation strategies to ensure your organization stays compliant and secure.
Before diving into SSP development, it’s essential to understand the CMMC ecosystem’s two distinct role categories:
- Authorized Consultants: RPs, RPAs who can help you prepare for your assessment or certification. An RPO is an organization that consists of RPs and RPAs.
- Authorized C3PAOs and the DIBCAC: They perform the formal assessments. Supporting the certification process are Certified CMMC Professionals (CCPs), Certified CMMC Assessors (CCAs), and Lead Assessors who conduct the actual evaluations.
As an RPO for CMMC, we at databrackets have guided organizations through the CMMC preparation and compliance process and helped them create and align their SSP with their actual practices while meeting the requirements of the standard. If you would like to receive a free SSP Template, you can email us at sales@databrackets.com
*Please note: The updated CMMC standard launched in 2024 is based on NIST SP 800-171 Revision 2. While this standard has been updated by NIST to NIST SP 800-171 Revision 3, CMMC continues to follow the structure and controls outlined in NIST SP 800-171 Rev 2.
What is a System Security Plan (SSP) and Why Does It Matter?
A System Security Plan is an official document that provides a detailed overview of your organization’s security posture. For CMMC compliance, an SSP outlines how your organization implements and maintains security controls to protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI).
The SSP is not merely a compliance checkbox; it’s a strategic document that:
Demonstrates your organization’s approach to protecting sensitive information
Maps out system boundaries and security controls
Documents roles, responsibilities, and accountability for security measures
Serves as a reference during security assessments and audits
Provides a foundation for continuous security improvement
For contractors pursuing CMMC Level 2 certification (where most CUI handling occurs), developing an SSP is mandatory. It’s typically the first document assessors will review during the certification process, making it a cornerstone of your compliance strategy.
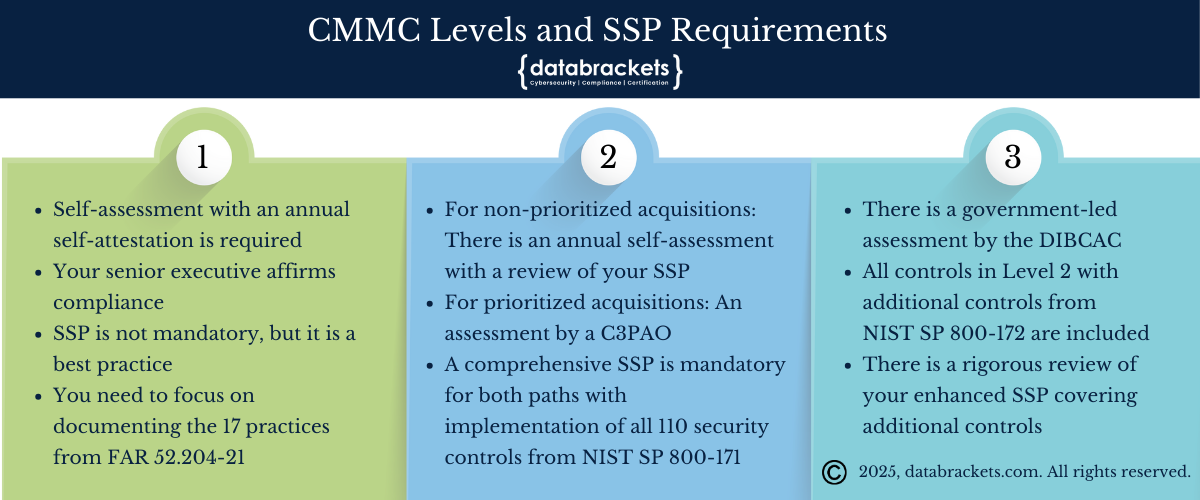
CMMC Levels and SSP Requirements
CMMC features three maturity levels, each with different SSP requirements and assessment paths:
Level 1 (Foundational)
Focuses on protecting Federal Contract Information (FCI)
Based on 17 controls from FAR 52.204-21
The Assessment Path
Self-assessment with annual self-attestation; No C3PAO involvement required
Your senior executive affirms compliance
SSP is not mandatory, but it is a best practice
Focus on documenting the 17 basic safeguarding practices
Level 2 (Advanced)
Designed to protect Controlled Unclassified Information (CUI)
Requires implementation of all 110 security controls from NIST SP 800-171
A comprehensive SSP is mandatory & it must document all security practices and their implementations
The Assessment Paths
For non-prioritized acquisitions: Annual self-assessment with SSP review
For prioritized acquisitions: Third-party assessment by C3PAO
Comprehensive SSP is mandatory for both paths
POA&Ms allowed for select controls with time-bound remediation (up to 180 days)
Must achieve at least 80% compliance score for conditional certification and a 100% score for critical controls
Triennial certification with annual affirmation
Level 3 (Expert)
For contractors handling high-priority CUI
Includes additional requirements from NIST SP 800-172
Requires an enhanced SSP that addresses additional controls
Government-led assessments by the DIBCAC
The Assessment Path
Government-led assessment by the Defense Industrial Base Cybersecurity Assessment Center (DIBCAC)
Must first achieve a perfect score on Level 2 certification by a C3PAO for systems in Level 3 scope
Rigorous review of enhanced SSP covering additional controls
Specialized expertise is typically required
POA&Ms allowed if at least 80% of Level 3 security requirements are met
Triennial certification with annual affirmation
By understanding which assessment path applies to your organization, you can tailor your SSP development approach and determine the appropriate type of assistance to seek.
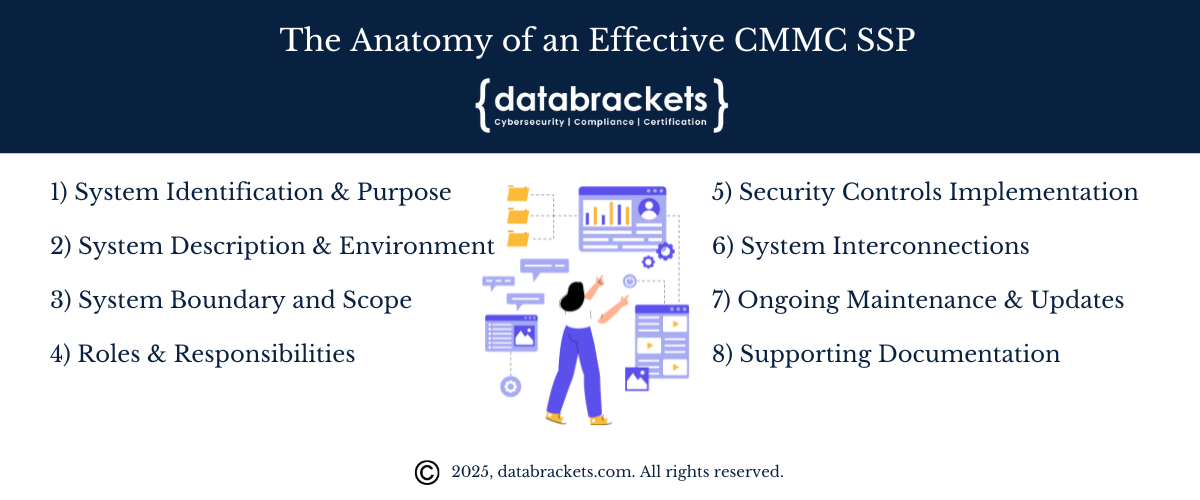
The Anatomy of an Effective CMMC SSP
Creating a thorough SSP requires attention to detail and proper structure. Here’s a breakdown of the essential components your SSP should include:
1. System Identification and Purpose
Organization information (name, address, CAGE code, DUNS number)
System name and purpose
Authorization boundaries
2. System Description and Environment
System overview and architecture
Network topology and diagrams
Hardware and software inventory
System interconnections and data flows
Physical environment and facilities
3. System Boundary and Scope
Clear definition of assessment scope based on CMMC categories:
CUI Assets
Security Protection Assets
Contractor Risk Managed Assets
Specialized Assets
Out-of-Scope Assets
Data types and classification
User categories and access requirements
4. Roles and Responsibilities
Organizational structure for security management
Key security personnel and their responsibilities:
Executive Leadership (CIO, CISO, CEO)
CMMC Program Manager/Compliance Officer
System Owners
Security Administrators
End Users
Contact information for key personnel
Approval authorities and escalation paths
5. Security Controls Implementation
Detailed documentation of all 110 NIST SP 800-171 controls for Level 2
For each control, include:
Implementation description
Responsible parties
Technical and administrative measures
Evidence of implementation
Assessment status (implemented, partially implemented, planned)
Documentation of shared responsibility with service providers
6. System Interconnections
External systems and connections
Connection security controls
Agreements and contracts with external entities
7. Ongoing Maintenance and Updates
Review and update the schedule
Change management procedures
Version control information
8. Supporting Documentation
References to related policies and procedures
Plans of Action and Milestones (POA&Ms) for any gaps
Risk assessment documentation
Configuration management plan
Incident response procedures
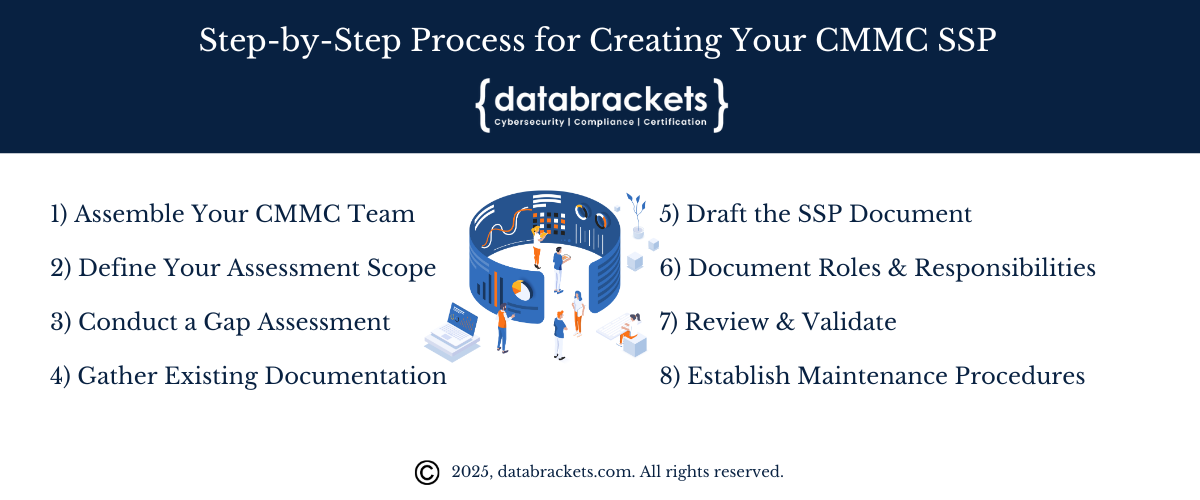
Step-by-Step Process for Creating Your CMMC SSP
Now that we understand the components, let’s explore a practical approach to creating your SSP for CMMC:
Step 1: Assemble Your CMMC Team
Before diving into documentation, establish a cross-functional team that includes:
Executive sponsor to provide leadership support and resources
IT security professionals who understand your technical environment
Business process owners who can identify where CUI/FCI exists
Compliance specialists familiar with CMMC and NIST requirements
Consider engaging appropriate external help (RP, RPA, or RPO) based on your CMMC level
*Please refer to the Key roles and responsibilities for your CMMC SSP in this blog to understand the tasks to be performed by different personnel.
Step 2: Define Your Assessment Scope
Identify all systems that process, store, or transmit CUI/FCI
Map data flows to understand how information moves through your environment
Categorize assets according to the CMMC Assessment Scope Guide
Create detailed network diagrams showing system boundaries
Document all interconnections with external systems
Step 3: Conduct a Gap Assessment
Perform a thorough self-assessment against NIST 800-171 controls
Identify existing security measures and documentation
Determine gaps in both implementation and documentation
Prioritize findings based on risk and compliance impact
Create POA&Ms for any identified gaps
Step 4: Gather Existing Documentation
Collect current policies, procedures, and security documentation
Review for accuracy, completeness, and alignment with CMMC requirements
Identify areas where documentation needs updating or creation
Organize materials to support SSP development
Step 5: Draft the SSP Document
Use a structured template aligned with NIST SP 800-18 Rev. 1 guidance
Start with the system description, scope, and boundaries
Document each security control implementation in detail
Reference supporting documentation for each control
Ensure all CMMC assessment objectives are addressed
Step 6: Document Roles and Responsibilities
Clearly define security roles throughout the organization
Assign responsibility for each control implementation
Document accountability and oversight structures
Include contact information for key personnel
Step 7: Review and Validate
Conduct internal reviews with stakeholders
Perform technical validation to ensure controls work as documented
Update documentation based on findings
Conduct a formal approval process with leadership
Step 8: Establish Maintenance Procedures
Define a regular schedule for SSP reviews and updates
Implement a change management process
Assign responsibility for ongoing maintenance
Document version control procedures

Key Roles and Responsibilities in CMMC SSP Development
Creating and maintaining an effective SSP requires clear assignment of roles and responsibilities. Here are the critical players in your CMMC compliance effort:
1. Executive Leadership
Responsibilities:
Evaluate the business impact of CMMC compliance
Provide strategic direction and budgetary support
Designate a CMMC Program Manager
Approve and endorse company-wide CMMC policies
Ensure adequate resources for implementation
2. CMMC Program Manager/Compliance Officer
Responsibilities:
Lead the overall CMMC compliance effort
Coordinate SSP development and maintenance
Oversee POA&M development and implementation
Liaise with assessment organizations (based on CMMC level – RP for Level 1, RPA or C3PAO for Level 2, DIBCAC for Level 3)
Interface with CMMC Third-Party Assessment Organizations (C3PAOs), if applicable
Monitor continuous improvement efforts
Track and report compliance status
3. System Owner
Responsibilities:
Define system boundaries and components
Provide technical details for SSP documentation
Implement security controls within their systems
Coordinate security assessments and testing
Maintain system documentation and evidence
4. Security Control Assessor
Responsibilities:
Conduct internal assessments of security controls
Validate control implementation effectiveness
Document assessment results
Provide recommendations for remediation
Support external assessments and audits
5. Information Owner
Responsibilities:
Identify and classify sensitive information
Define data protection requirements
Ensure appropriate handling of CUI
Review and approve access controls
Validate data flow documentation
6. End Users
Responsibilities:
Follow security policies and procedures
Complete the required security training
Report security incidents
Handle sensitive information according to guidelines
Participate in security awareness programs
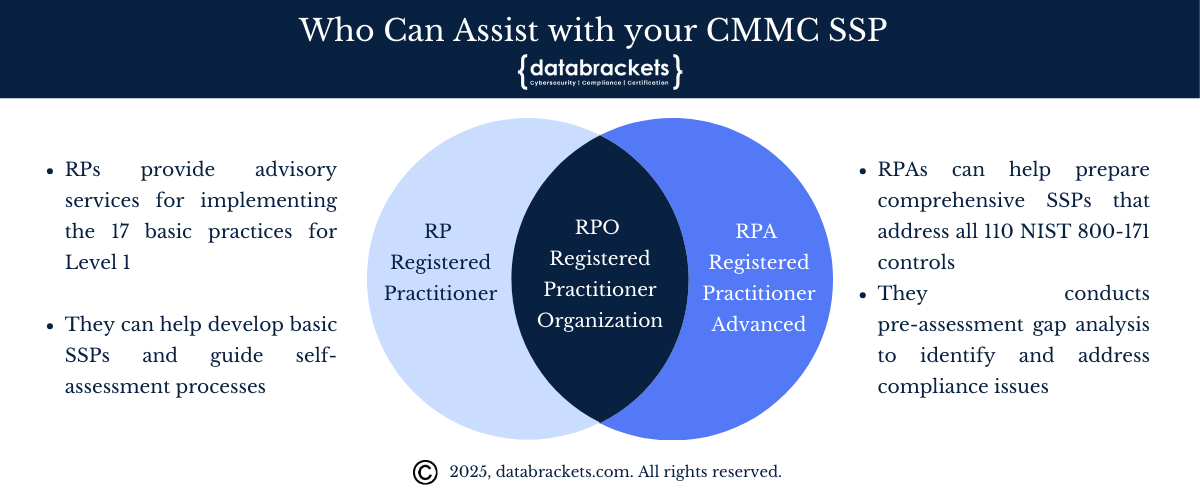
Who Can Assist with your CMMC SSP
Depending on your CMMC level and specific needs, different types of professional assistance are available to help with your SSP development:
Registered Provider (RP)
Appropriate for Level 1 compliance assistance
Can help develop basic SSPs and guide self-assessment processes
Provides advisory services for implementing the 17 basic practices
Assists with documenting implementation and preparing for annual self-attestation
Registered Practitioner Advanced (RPA)
Suitable for Level 2 organizations (especially those with non-prioritized acquisitions requiring self-assessment)
Helps prepare comprehensive SSPs that address all 110 NIST 800-171 controls
Conducts pre-assessment gap analysis to identify and address compliance issues
Assists with appropriate documentation of assessment objectives
Registered Provider Organization (RPO)
Can support organizations at all CMMC levels
Provides more comprehensive services with teams of qualified practitioners
Must have at least one Registered Practitioner (RP) associated with the organization
Offers specialized expertise across security domains
Helps integrate compliance with broader security and business objectives
Can help with remediation of identified gaps
Cannot perform official certification assessments
When to Engage Professional Assistance
Early planning stage: Get help defining your scope and assessment boundaries
Gap assessment: Bring in experts to identify compliance gaps objectively
Documentation development: Utilize specialists for developing compliant SSPs
Pre-assessment preparation: Conduct mock assessments before formal evaluation
Remediation support: Address identified gaps with expert guidance
Working with qualified professionals can significantly streamline your CMMC journey. Consider engaging assistance well before your required compliance date to ensure adequate time for remediation and documentation.
Common Pitfalls to Avoid in SSP Development
When creating your SSP, be aware of these common challenges:
1. Inadequate Scoping
Issue: Incorrectly identifying system boundaries or missing critical components
Solution: Use the CMMC Scoping Guide to thoroughly analyze your environment and include all relevant assets
2. Generic Documentation
Issue: Using boilerplate language without customizing to your actual implementation
Solution: Provide specific, detailed descriptions of how each control is implemented in your environment
3. Missing Assessment Objectives
Issue: Addressing only the high-level controls without the detailed assessment objectives
Solution: Review NIST SP 800-171A to ensure all assessment objectives are covered
4. Unclear Responsibilities
Issue: Failing to assign specific responsibilities for security controls
Solution: Clearly document who is responsible for implementing, maintaining, and monitoring each control
5. Incomplete Evidence References
Issue: Not linking controls to supporting evidence or documentation
Solution: Create comprehensive evidence mapping that connects each control to specific policies, procedures, or technical implementations
6. Overlooking External Service Providers
Issue: Not documenting shared responsibility with cloud or managed service providers
Solution: Clearly document which controls are implemented by external providers and verify their compliance status
Tips for SSP Maintenance and Continuous Improvement
Creating your SSP is just the beginning. Maintaining it effectively requires ongoing attention:
1. Regular Reviews and Updates
Schedule quarterly reviews of your SSP
Update after significant system changes
Conduct annual comprehensive assessments
Document all changes with version control
2. Integration with Change Management
Link your SSP to your change management process
Evaluate security impacts before implementing changes
Update documentation as part of change implementation
Maintain traceability between changes and documentation
3. Continuous Control Validation
Regularly test security controls to ensure effectiveness
Update documentation based on test results
Implement continuous monitoring where possible
Track metrics to demonstrate control performance
4. Documentation Management
Establish a central repository for all compliance documentation
Implement access controls for sensitive documentation
Use document management tools to track versions and changes
Create links between related documents for easy reference
Beyond Compliance to Security Maturity
While creating an SSP for CMMC compliance may seem overwhelming, it represents an opportunity to strengthen your organization’s security posture. By developing a comprehensive, accurate, and detailed SSP, you’re not just checking a box for DoD contracts—you’re building a foundation for robust cybersecurity that protects your organization and your customers.
Remember that your SSP is a living document that should evolve with your organization and the threat landscape. By establishing clear roles and responsibilities, maintaining thorough documentation, and continuously improving your security practices, you’ll be well-positioned for CMMC certification and long-term security success.
Start your SSP development process today by assembling your team, defining your scope, and conducting an initial gap assessment. With methodical planning and execution, you can navigate the CMMC certification process successfully and demonstrate your commitment to protecting sensitive defense information.
Helpful Resources and Templates
To assist you in your SSP development journey, here are direct links to valuable resources mentioned throughout this guide:
Official Documentation & Templates
NIST SP 800-18: Guide for Developing Security Plans – Foundational guidance on SSP development
NIST SP 800-172 – Enhanced security requirements for Level 3
DoD CMMC Documentation – Official DoD CMMC resources
The Cyber AB Marketplace – Official directory of RPOs, C3PAOs, and other CMMC ecosystem participants
Additional Resources
DoD Cyber Exchange – Repository of security requirements and guidance
NIST Cybersecurity Framework – Complements CMMC implementation
Federal Register CMMC Final Rule – Official CMMC rule documentation
This blog post is intended as general guidance and does not constitute legal advice. Organizations should consult with qualified CMMC professionals to ensure their specific compliance needs are addressed appropriately.
Key Takeaways
Creating an SSP is foundational to CMMC compliance because it documents how your organization protects Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) through explicit, actionable security practices.
The SSP requirements differ by maturity level: at Level 1 it’s optional but a best practice, at Level 2 it’s mandatory and must fully document implementation of the 110 NIST SP 800-171 controls, and at Level 3 it expands to encompass enhanced controls from NIST SP 800-172.
A robust SSP must clearly define scope and boundaries of systems and data in the assessment, including where CUI resides, how systems interconnect, and what environment they operate in, forming the basis for assessor evaluation.
The document should include a detailed description of roles and responsibilities, assigning accountability for security control implementation, maintenance, and oversight across the organization.
Each security control must be described in terms of how it is implemented in practice, who is responsible, and what evidence supports its existence and effectiveness, avoiding generic or boilerplate language.
Developing an SSP involves conducting a gap assessment against CMMC requirements, gathering existing policies and artifacts, and methodically addressing both implementation and documentation shortcomings before drafting the final plan.
Ongoing maintenance procedures for review, update, and version control are critical so the SSP remains current as systems, processes, or threats evolve, rather than becoming stale after initial publication.
Anticipating and addressing common pitfalls—such as incomplete scoping, unclear responsibilities, missing evidence links, or unaddressed assessment objectives—improves the likelihood of a successful CMMC assessment.
Engaging appropriate qualified internal or external expertise early—such as compliance officers, IT security personnel, or registered practitioners—can streamline scoping, documentation accuracy, and overall SSP quality.
How Experts at databrackets can help you
Create your CMMC SSP
Our team of security experts has supported organizations across a wide variety of industries for over 15 years to align their processes with security frameworks like ISO 27001:2022, SOC 2, FedRAMP, CMMC, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, HIPAA, etc. We are an authorized certifying body for ISO 27001, an authorized C3PAO for CMMC and an authorized 3PAO for FedRAMP. We also have partnerships to help clients prepare for and obtain other global security certifications.
We specialize in assisting organizations navigate the complexities of NIST SP 800-171 Revision 2, a critical component for securing Department of Defense (DoD) contracts. Our team specializes in providing practical, effective guidance that transforms CMMC compliance from a daunting obstacle into a strategic business enabler. If you would like to receive a free SSP Template, you can email us at sales@databrackets.com
Given below is our comprehensive suite of deliverables to help you prove your compliance with CMMC 2.0
Readiness & Implementation Support
Network Diagram
CUI Flow Diagram
CUI System Boundary
FIPS Validation Diagram
Shared control matrix
Creating your SSP
Customized Information Security Policy
Data Breach Policy
Vulnerability Scan Report
Vendor Compliance Assessment
Advisory Services and Audit Support
Customized CUI Awareness Training (Optional / On-Demand)
Other Customized Policies & Procedures
Schedule a Consultation if you would like to understand how we can customize our services to meet your specific requirements.
Summary
To summarize,
An SSP is the central compliance document in CMMC that formally describes how your organization implements and maintains required security controls to protect Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), making it indispensable for certification readiness.
CMMC 2.0 defines different SSP expectations by level: at Level 1 it’s a recommended practice, at Level 2 it becomes mandatory with detailed documentation of all 110 NIST SP 800-171 controls, and at Level 3 it must also capture enhanced requirements from NIST SP 800-172.
A well-structured SSP clearly outlines scope and system boundaries by identifying the information systems, assets, and CUI flows that fall within assessment boundaries, helping both internal teams and assessors understand what is in-scope.
Defining roles and responsibilities for security governance and control implementation ensures clarity on accountability for each element of your cybersecurity posture, which strengthens both documentation accuracy and operational execution.
Each security control in the SSP should be described in terms of its actual implementation, including control activities, responsible parties, supporting evidence, and current status, rather than generic statements that don’t map to real practice.
Developing an SSP is most effective when preceded by a gap assessment, which compares existing documentation and security practices against CMMC requirements to surface discrepancies and plan remediations before drafting.
The SSP should reference and integrate supporting documentation such as policies, procedures, Plans of Action and Milestones (POA&Ms), and risk assessments to demonstrate cohesive evidence of compliance and readiness for assessment.
Maintaining the SSP as a living document with regular reviews, updates tied to system changes, version control, and integration with change management processes preserves its relevance and audit readiness over time.
Recognizing and avoiding common pitfalls — such as inadequate scoping, generic wording, missing assessment objectives, unclear responsibilities, and unlinked evidence — improves documentation quality and reduces assessment friction.