Verizon’s Data Breach Investigations Report found that 74% of all breaches were a result of human error due to social engineering. This statistic is based on the analysis of 16,312 security incidents and 5,199 breaches. This report puts Ransomware as the cause of 24% of all breaches. It also puts the cost of 95% of all security incidents at $1 million – $2.25 million dollars. Apart from Ransomware, the report states that a variety of different techniques were used to gain entry to an organization, such as exploiting vulnerabilities (5%), phishing (12%), and using stolen credentials (49%).
With over a decade of experience in supporting organizations to meet compliance and cybersecurity requirements, our certified experts have recommended a 2 pronged approach to preventing the devastating impact of Ransomware. It involves using Security Tech with Security Policies and Procedures. This approach is useful against all cyber attacks and data breaches and is in keeping with industry best practices. Before you select Security Tech for your organization, we recommend undergoing a Security Risk Analysis to detect areas of improvement and work with a CISO or vCISO to design a comprehensive cybersecurity strategy.
Preventing the devastating impact of Ransomware has 2 essential elements
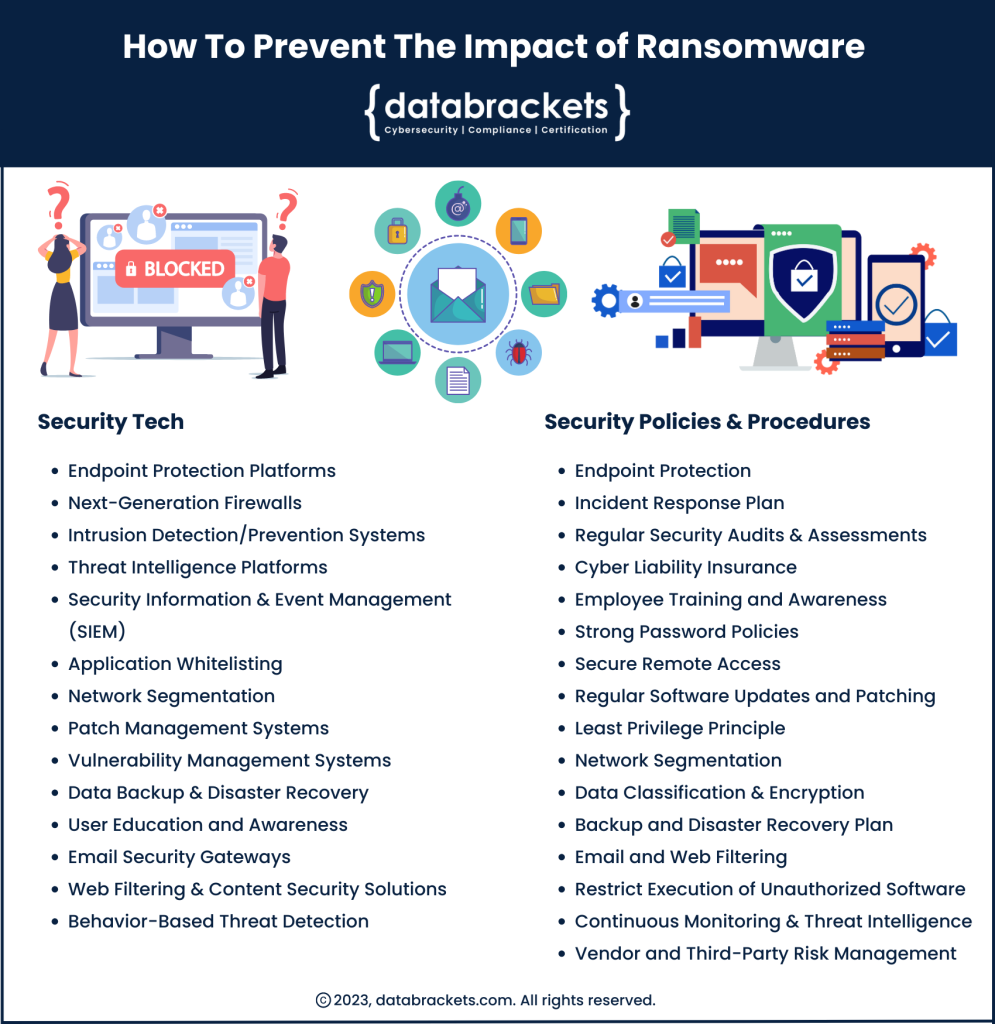
1. Security Tech
2. Security Policies and Procedures
To prevent the impact of ransomware, you need to ensure your cyber security strategy has a perfect sync between these elements. In the infographic above, you will notice several duplications. Organizations need to implement security tech and embed their usage into their security policies and procedures to complete the cycle. By training employees, personnel on contract and vendors who work with sensitive information, you can ensure that potential loopholes are plugged before they can be exploited by hackers.
Explore details of security tech and vendors whom we trust in our previous blog – Technologies To Detect And Prevent Ransomware Attacks. In this blog, we will focus on the second element.
Security Policies and Procedures to Prevent Ransomware
Here are several ways organizations can prevent ransomware through their policies and procedures:
1. Endpoint Protection:
Most ransomware attacks stem from end devices such as laptops, desktops, and mobile devices linked to the organization’s network Implement robust endpoint security solutions, including antivirus and anti-malware software, host-based intrusion detection systems (HIDS), and endpoint detection and response (EDR) tools on all devices connected to the network. These tools can detect and block malicious activities and provide real-time threat intelligence. Regularly update and monitor these solutions to detect and block ransomware threats.
2. Incident Response Plan:
If you fail to plan, you plan to fail. Develop a comprehensive incident response plan that outlines the steps to be taken in case of a ransomware attack. The plan should include roles and responsibilities, communication procedures, and steps for isolating and containing the infection. It should also include backup restoration processes, contact information for relevant stakeholders, notifying appropriate personnel, and engaging with law enforcement, if necessary.
3. Regular Security Audits and Assessments:
Conduct periodic security audits and assessments, including vulnerability scans and penetration tests, to identify and address potential weaknesses in the organization’s security infrastructure. This is critical since the security posture of modern day organizations changes very fast. This helps identify vulnerabilities that could be exploited by the most recent ransomware attackers. It also helps organizations design initiatives for proactive remediation and continuous improvement of security controls.
4. Cyber Liability Insurance:
Consider obtaining Cyber Liability Insurance coverage to help mitigate the financial impact of a ransomware attack. Review the policy terms and conditions carefully to understand what is covered and ensure it aligns with the organization’s specific needs.
5. Employee Training and Awareness:
Educate employees about the risks of ransomware and provide regular training on best practices for email and internet usage. This includes recognizing suspicious links and attachments, following safe browsing practices, avoiding clicking on unknown links, being cautious about downloading files from untrusted sources, practicing good password hygiene and how to identify and respond to potential ransomware threats. This helps create a security-conscious culture within the organization.
6. Strong Password Policies:
Enforce strong password policies that require employees to use complex, unique passwords and change them regularly. Multi-factor authentication (MFA) should also be implemented to add an extra layer of security. Encourage the use of password managers to ensure unique and secure passwords for each account.
7. Secure Remote Access:
Establish strict policies for remote access to organizational systems and data. This may include the use of virtual private networks (VPNs), multi-factor authentication (MFA) to authenticate remote users and other secure remote desktop protocols. Remote access should only be granted to authorized personnel and with appropriate security measures in place. This prevents attackers from exploiting weak or unsecured remote connections.
8. Regular Software Updates and Patching:
Maintain an up-to-date inventory of software and systems. Develop a policy that mandates the timely installation of security patches and updates for operating systems, software applications, and network devices. Many ransomware attacks exploit known vulnerabilities that can be mitigated by keeping software up to date.
9. Least Privilege Principle:
Implement the principle of least privilege, where employees are only given the access rights necessary to perform their job functions. Restricting access limits the impact of a ransomware attack by minimizing the number of systems and data that can be compromised.
10. Network Segmentation:
Ensure that your IT Team or your MSP divides the network into separate zones based on user roles, functions, and levels of sensitivity. Implement firewalls and access controls to restrict unauthorized access. This helps contain the spread of ransomware within the network and minimizes the potential damage caused by an attack.
11. Data Classification and Encryption:
Develop a data classification policy to categorize data based on its sensitivity and importance. Encrypt sensitive data at rest and in transit to protect it from unauthorized access, even if a ransomware attack occurs.
12. Backup and Disaster Recovery Plan:
Implement a robust backup strategy that includes regular and automated backups of critical data and systems. Store backups offline or in a separate, secure network at an isolated location to prevent ransomware from encrypting them. Develop a comprehensive disaster recovery plan to restore systems and data in the event of a ransomware attack. Test the backups periodically to ensure their integrity and reliability.
13. Email and Web Filtering:
Implement email and web filtering solutions that can identify and block malicious content, including phishing emails, attachments and websites distributing ransomware. These solutions can help prevent employees from inadvertently accessing malicious links or downloading infected files. Regularly update and configure these filters to enhance their effectiveness.
14. Restrict Execution of Unauthorized Software: Implement strict policies that restrict the execution of unauthorized or unknown software. This can be achieved through application whitelisting or using secure application sandboxing techniques.
15. Continuous Monitoring and Threat Intelligence:
Deploy robust monitoring systems to detect and respond to potential ransomware threats in real-time. Stay updated with the latest threat intelligence and information sharing initiatives to proactively defend against emerging threats. One solution that merges this with compliance and regulatory requirements is to use continuous compliance-based monitoring. This practice is subscription based and it monitors how well your security controls are functioning in real-time with regard to regulatory and compliance benchmarks.
16. Vendor and Third-Party Risk Management:
Implement a robust vendor and third-party risk management program to ensure that external partners and suppliers maintain adequate security measures. Ensure that they adhere to proper security standards to minimize the risk of ransomware infiltrating the organization through external connections This includes assessing their security practices, contractual obligations, and conducting regular audits.
By implementing these best practices, organizations can significantly reduce the risk of ransomware attacks and minimize the potential impact of any successful attempts. However, it’s important to note that cybersecurity is an ongoing process, prevention measures alone may not guarantee 100% security, and organizations should continuously adapt and improve their defenses to keep up with evolving threats.
How databrackets can help you prevent Ransomware
Experts at databrackets have extensive experience working with clients across a variety of industries. We have customized services to help you detect and prevent Ransomware. They include:
- Security Tech Consulting: Our certified experts understand your risk exposure and recommend best-in-class tools to mitigate the risks.
- Customized Policies and Procedures: Based on our assessment and after understanding your processes and procedures, we leverage our extensive policy templates and customize them for your organization.
- Customized Training: We customize our training content based on the roles in your organization and your existing procedures.
- Regular Compliance Audits: We conduct regular audits to support your business requirements for periodic regulatory and customer-contract based evaluation.
- Regular Vulnerability Scans and Pen Testing: We conduct Vulnerability Scans and Third party Pen Testing periodically.
- Managed Security Services: We offer managed compliance and security services to continuously monitor and update your security team about your security posture.
- Backups & Disaster recovery: We help you design a plan & implement solutions for Business Continuity.
Our team has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.