Penetration testing, often referred to as “pen testing” or “ethical hacking,” is a proactive security assessment approach used to identify vulnerabilities and weaknesses within a computer system, network, or application. In the context of radiology, penetration testing is specifically designed to evaluate the security of medical imaging systems, including Picture Archiving and Communication Systems (PACS), Radiology Information Systems (RIS), medical devices and associated network and application infrastructure. The primary goal of penetration testing in radiology is to simulate real-world cyberattacks and assess the system’s ability to withstand and defend against these threats as the Radiology industry increasingly handles sensitive electronic patient data with many partners, vendors and customers.
Areas of Pen Testing for Radiology
There are 4 specific areas of pen testing that are of relevance to organizations that work with medical imaging and radiology. They are:
- Network Testing
- Application Testing
- Mobile App Testing
- IoT Testing
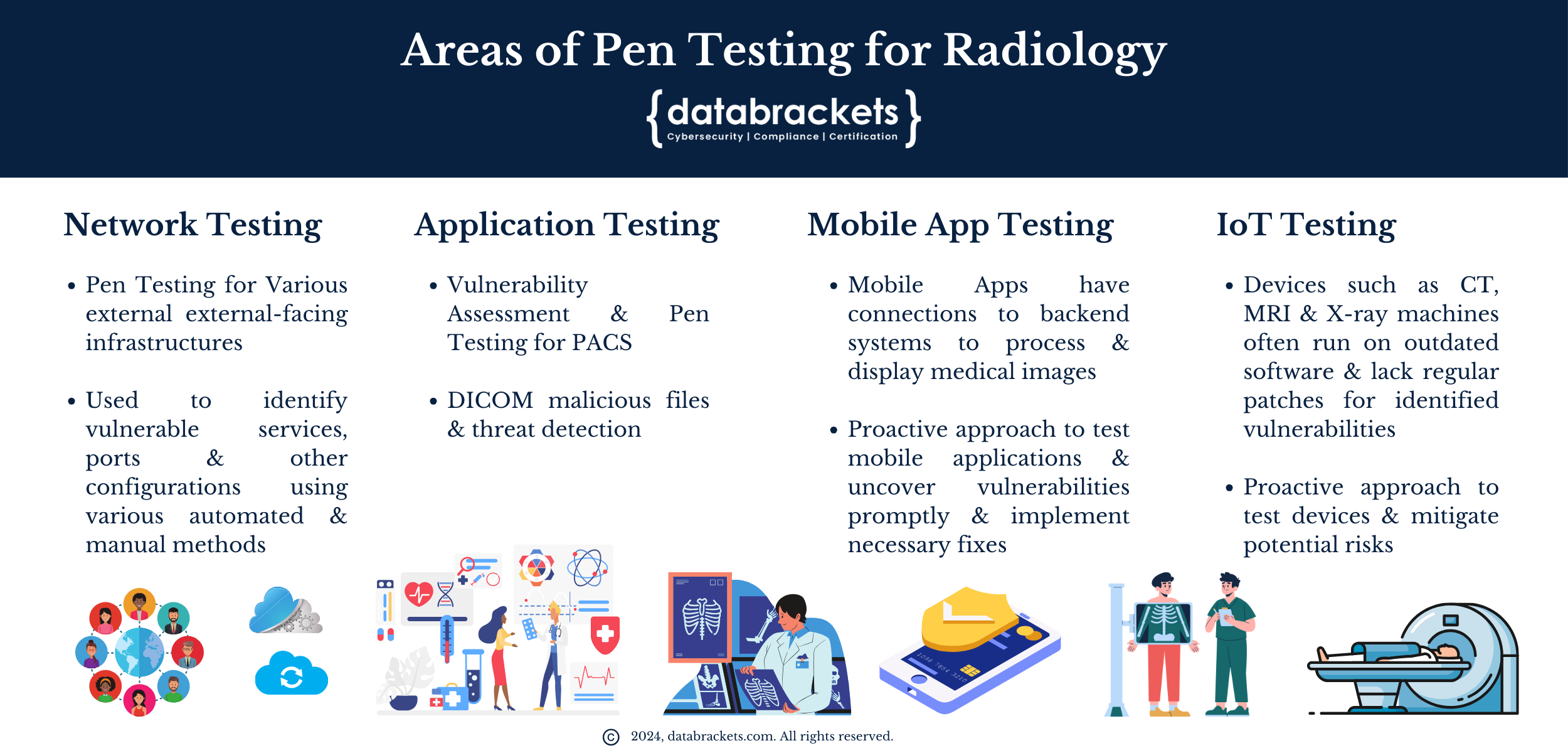
1. Network Testing for Radiology
Radiology organizations operate various external-facing infrastructures essential for engaging with hospitals, referring physicians, and other collaborators. However, the existence of these interfaces poses significant risks to the organization’s security if not adequately fortified. Ensuring the robustness of network security protocols becomes paramount in safeguarding sensitive data and maintaining the integrity of operations. Proactive measures, including comprehensive vulnerability assessment and penetration testing of network systems, are imperative to identify vulnerabilities and implement necessary defenses, thereby mitigating potential breaches and protecting the confidentiality of patient information.
2. Application Testing
Radiology organizations must also prioritize application testing, particularly for Picture Archiving and Communication Systems (PACS), which store vast patient records accessed by numerous radiologists. As part of Vulnerability Assessment and Penetration Testing (VAPT), rigorous evaluation of PACS system infrastructure and applications is essential to verify correct configuration and fortify against potential vulnerabilities. Additionally, given the interconnected nature of many external-facing applications in the radiology domain, comprehensive testing within this context becomes imperative. This includes ensuring the secure implementation of DICOM (Digital Imaging and Communications in Medicine) protocols, which facilitate the exchange of medical images and related information. We conduct a DICOM vulnerability assessment (DVA) to meet this objective. Such assessments serve to identify weaknesses in the system’s architecture and application interfaces, enabling the implementation of robust security measures to safeguard patient data and uphold operational integrity.
3. Mobile App Testing
Mobile applications utilized by radiologists frequently establish connections to backend systems to process and display medical images. However, vulnerabilities within these mobile apps pose a significant risk, potentially compromising the integrity of the backend infrastructure if left unidentified and unaddressed. Therefore, it is crucial to conduct thorough testing of mobile applications to uncover any vulnerabilities promptly and implement necessary fixes. This proactive approach ensures the security and stability of the entire system, safeguarding sensitive medical data and maintaining seamless functionality for healthcare professionals.
In radiology, numerous devices such as CT, MRI, and X-ray machines are connected to the hospital networks or provider systems. Unfortunately, many of these devices run on outdated software and lack regular patches for identified vulnerabilities. Vulnerability Assessment and Penetration Testing (VAPT) play a crucial role in uncovering these issues, providing a structured framework for prioritizing and addressing them. By identifying vulnerabilities in connected radiology devices, VAPT ensures a proactive approach to cybersecurity, mitigating potential risks and enhancing the overall safety and reliability of diagnostic equipment within healthcare settings.
How databrackets can help you with Pen Testing for Radiology
The digitization of radiology is advancing rapidly, presenting a growing risk landscape. Systems lacking robust hardening and configuration create ample opportunities for hackers to exploit vulnerabilities using straightforward techniques, potentially causing significant disruptions to business operations. Given the external-facing nature of radiology infrastructure, it is imperative for radiology organizations to consistently invest in fortifying their security posture and validating its effectiveness. Proactive measures in security enhancement are essential to mitigate risks and uphold the integrity of radiological operations amidst the evolving digital landscape.
Security Experts at databrackets
Our Vulnerability Assessment & Pen Testing capabilities have been accredited by the A2LA for ISO 17020 Conformity assessment for inspection bodies. The security experts at databrackets bring years of extensive Radiology industry experience to the table, along with a deep understanding of industry-standard security practices. We possess comprehensive knowledge of common pitfalls in system configurations, recognizing factors such as outdated software in medical devices, inadequately configured firewalls, and unpatched systems that often lead to security vulnerabilities. Through meticulous scoping and testing using a variety of tools, we meticulously uncover all potential vulnerabilities visible to attackers, ensuring thorough detection and protection for our clients’ systems and data.
Our client engagement starts with your business objective in mind. Vulnerability Assessment & Pen Testing is requested for several reasons:
- To secure your environment
- To meet certain regulatory compliance or certification requirements
- To fulfill a request made by your customer
- A combination of the reasons mentioned above
Once we understand what you require, our exercise focuses primarily on scoping of the engagement and setting expectations. We use a variety of tools depending on the type of test and systems in which we need to identify vulnerabilities & conduct pen testing. Our process includes:
- Discovery
- Identifying and finalizing assets
- Identifying vulnerabilities
- Exploitation of the vulnerabilities (Pen Testing)
- Validation of the issues identified
- Remediation/Recommendations
- Re-testing
Apart from using the tools best in the industry, we also focus on remediation and retesting of the environment. We just don’t give hundreds of pages of reports without any help to eliminate the risks. We help our clients prioritize the risks based on the context, patch the systems and select security tech, policies and procedures that are considered best practices in their industry. We also set up continuous monitoring after our tests to track any changes to your environment & send you timely alerts.
As we continue to work with our clients, we sharpen our understanding of your specific environment and system. This helps us to design cadence for continuous protection and monitoring using the right tools to ensure continual improvement and proactive identification of issues for the future. You can contact us for a customized quote or schedule a consultation.
You can also meet us in-person at RSNA 2024, at South Hall Level 3 – Booth No. 3174.
databrackets overview
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like ISO 27001:2022, SOC 2, HIPAA, 21 CFR Part 11, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC 2.0 etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Related Links:
Technologies To Detect And Prevent Ransomware Attacks
Sources of Ransomware Attacks on Healthcare Systems
What are the new controls added to ISO 27001 in 2022?
How to Select a Security Vendor
Author: Aditi Salhotra, Digital Marketing and Business Development, databrackets.com
Aditi is a Digital Marketing and Business Development Professional at databrackets.com. She graduated with honors in Marketing from Sheridan College, Canada. In addition to her current profile, she contributes to Product Development and Content Creation. She is a strong advocate of Good Cyber Hygiene and white hat SEO techniques. She is proud of the company’s mission to safeguard organizations from cyber threats and ensure their business continuity in adverse situations.
Technical Expert: Srini Kolathur, Director, databrackets.com
The technical information presented in this blog has been carefully reviewed and verified by our Director, Srini Kolathur. Srini is results-driven security and compliance professional with over 20 years of experience supporting, leading, and managing global IT security, compliance, support, and risk assessment in fortune 100 companies. Some of his key areas of focus are SOC 2, ISO 27001, NIST 800-171, NIST 800-53, NIST Cybersecurity Framework, HIPAA, Security Risk Assessment, CMMC 2.0 among others. He is a CMMC Registered Practitioner (RP), CISSP, CISA, CISM, MBA. He is active in several community groups including Rotary International and TiE.