Understanding ISO 27001
ISO 27001 is an internationally recognized standard with a framework for implementing, maintaining, and continually improving an Information Security Management System (ISMS). This standard was published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC).
Article's content
Download our ISO 27001 Certification Guide
The Purpose of ISO 27001
The main purpose of ISO 27001 is to establish a structured approach to managing sensitive company information, ensuring it remains confidential, accurate, and available only to those who have the proper authorization by implementing Information Security Management System(ISMS). Specifically, ISO 27001 aims to:
Reduce Information Security Risks: Help organizations identify vulnerabilities, assess threats, and implement measures to mitigate risk.
Enhance Data Security and Trust: Safeguard data from breaches, theft, or unauthorized access to maintain the trust of customers, partners, and employees.
Compliance and Governance: Ensure compliance with regulations and standards governing information security, thereby improving overall governance.
ISO 27001 establishes a culture of security throughout the organization by promoting security awareness and adherence to established protocols.
Principles of ISO 27001
ISO 27001 adheres to the three principles of Information Security:
Confidentiality: only authorized personnel have the right to access information
Integrity: only authorized personnel are allowed to modify the information
Availability: information must be accessible to authorized personnel when they require it
Organizations need to begin their ISO journey with a Risk Assessment to understand where these principles of information security may be violated. This assessment exposes the vulnerabilities in their architecture and guides them as they restructure it to ensure these principles are followed. This 2-step process enables them to identify the source of potential problems, work on risk mitigation strategies, and ensure that security controls and safeguards are implemented effectively.
The structure of the ISO 27001 standard consists of two parts:
ISO 27001 Clauses
ISO 27001 Audit Controls: Annex A
Enforcement of ISO 27001
The implementation of ISO 27001 is not regulated by a specific government body; instead, it relies on the efforts of various entities:
International Organization for Standardization (ISO): ISO is an independent, non-governmental body that develops standards, including ISO 27001, in collaboration with industry experts.
Accredited Certification Bodies: To achieve ISO 27001 certification, an organization must undergo an audit conducted by an accredited certification body. These bodies assess whether an organization’s ISMS meets the standard’s requirements. They conduct the triennial ISO 27001 certification audit and annual surveillance audits per ISO 17021 and ISO 27006 standard requirements. databrackets is an authorized certification body for ISO 27001.
Internal Auditors and Compliance Teams: Organizations implementing ISO 27001 must conduct regular internal audits and compliance reviews to ensure that their ISMS remains effective and up to date. Compliance teams play a key role in maintaining adherence to ISO standards.
If your organization is transitioning from ISO 27001:2013 to 27001:2022, explore our blog Transition to ISO 27001:2022
Key Components of ISO 27001
ISO 27001 is built on several core components that serve as the foundation for a robust ISMS. These components are critical for managing and protecting information security effectively:
Information Security Management System (ISMS): An ISMS is a comprehensive approach that covers processes, technologies, and people, ensuring that information is managed securely. The ISMS is designed to be scalable, adaptable, and tailored to the organization’s unique needs.
Risk Assessment and Treatment: Organizations must conduct risk assessments to identify potential threats and vulnerabilities. This process includes identifying information assets, assessing associated risks, and implementing measures to treat or mitigate those risks.
Annex A Controls: ISO 27001 includes 93 security controls outlined in Annex A. These controls are categorized across domains such as access control, cryptography, physical security, communications security, and more. Organizations select and implement appropriate controls based on their risk assessment.
Statement of Applicability (SoA): The Statement of Applicability identifies which Annex A controls are applicable and why they were selected or omitted. It serves as the foundational document for ISO 27001 implementation and is critical for audits.
Continuous Improvement (PDCA Cycle): ISO 27001 promotes a culture of continuous improvement through the Plan-Do-Check-Act (PDCA) cycle. This involves planning security measures, implementing them, evaluating their effectiveness, and making necessary adjustments to enhance security.
Industries that benefit from ISO 27001
ISO 27001 is relevant to a wide range of industries where information security is paramount. Some of the industries that benefit most from ISO 27001 include:
Finance and Banking: Financial institutions, such as banks, insurance companies, and investment firms handle large volumes of sensitive customer data, including financial transactions and personal identifiers. ISO 27001 ensures secure handling and minimizes the risk of fraud, cyberattacks, or data breaches.
Healthcare: Hospitals, clinics, pharmaceutical companies, and other healthcare entities deal with confidential patient records, medical histories, and drug research data. ISO 27001 helps healthcare organizations comply with HIPAA and protect patient data from unauthorized access.
Technology and Software Development: Tech companies, software development firms, and SaaS providers manage sensitive customer information and intellectual property. ISO 27001 ensures the integrity of software products and protects customer data, mitigating the risk of data leaks and cyberattacks.
Government and Public Sector: Government bodies and public institutions collect and store data related to citizens, public infrastructure, and national security. ISO 27001 helps protect sensitive data from threats, including espionage and cyberattacks.
Telecommunications: Telecom companies deal with extensive amounts of customer data, including personal identifiers, communication logs, and geolocation information. ISO 27001 ensures the security of network infrastructures and personal data.
Manufacturing and Industrial: Manufacturers dealing with proprietary information, supply chain data, or product development details can benefit from ISO 27001. It ensures that the confidentiality of intellectual property and supplier relationships is maintained.
Legal and Consultancy Firms: Law firms, consultancies, and other professional services handle sensitive client data. ISO 27001 helps these firms protect client confidentiality, build trust, and ensure compliance with various data protection regulations.
The ISO 27001 Certification Process
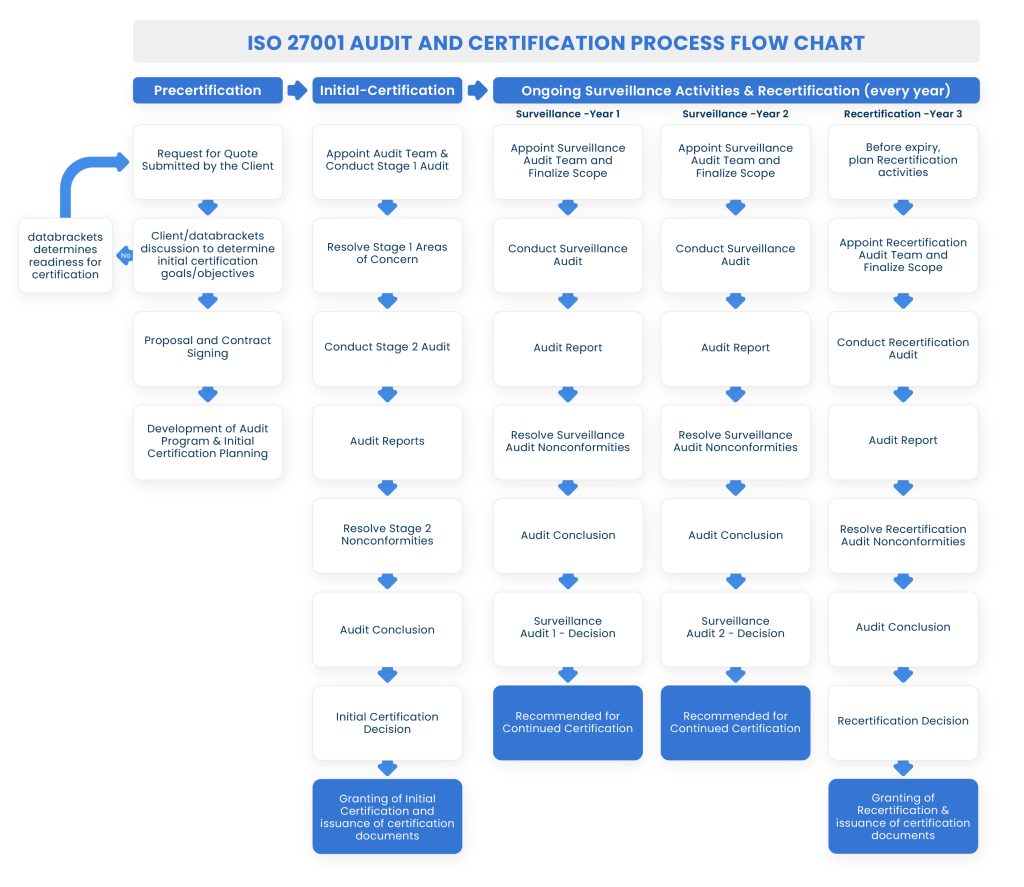
There are 2 stages in the certification process in year 1: Stage 1 & Stage 2 Audit followed by 2 annual surveillance audits. The Stage 1 Audit evaluates your existing processes and reports on any areas of improvement, and the Stage 2 audit determines if those areas have been implemented and your ISMS meets the standards of ISO 27001. After 2 annual surveillance audits in Year 2 and Year 3, the organization needs to begin the triennial cycle again by undergoing a re-certification audit.
1. Stage 1 Audit (Year 1)
The initial examination is referred to as a “Stage 1” audit. During this stage, the organization’s documentation and procedures are evaluated to assess how well the organization already meets the ISO 27001 criteria. The length of the evaluation is determined by the size of the organization and the industry in which it operates.
When the Stage 1 evaluation is completed, a closing meeting is held to summarize the findings. The ISO Lead Auditors submit a report outlining what transpired during the assessment along with any areas of improvement. These are referred to as” areas of concern that could be classified as nonconformity during Stage 2.”
2. Stage 2 Audit (Year 1)
During this stage, the auditor observes organizational procedures in operation. This also includes meetings with both managers and employees. The auditor evaluates if the procedures have been clearly understood and if the checks and controls are sufficient to limit the risks of a data security breach, as required by ISO 27001.
If the lead auditor discovers no issues, they confirm that the ISMS fulfills the necessary ISO 27001 criteria. The certification committee examines their recommendation and issue the Initial Audit ISO 27001 certificate. However, If the auditor discovers nonconformities, they are included in a detailed report. They need to be addressed before getting certified. Once the issues are resolved, the organization is officially recognized as “ISO/IEC 27001:2013 certified”.
3. Ongoing Surveillance Audits (Year 2 & 3) and Re-certification Audit (Year 4): Annual audits are planned between the certification body and the organization to guarantee compliance and to schedule the re-certification process every 3 years.
Download our ISO 27001 Certification Guide
7 Benefits of ISO 27001 Certification
Pursuing the ISO 27001 Certification is proof of an organization’s dedication to information security. However, this may not be required in all cases, countries, or businesses. Organizations have the choice between being compliant and pursuing certification to prove their compliance.
In several countries, B2B contracts and financial institutions mandate compliance with ISO 27001 controls and do not mandate getting ISO certified. Their prerogative is to ensure that potential threats remain at bay. However, there are several B2B deals that demand certification before a partnership is formalized and information is shared. This is done to ensure that annual audits and recertification are conducted at regular intervals by an independent third party that is cognizant of the dynamic landscape of cyber threats.
7 benefits of getting an ISO 27001 certification are:
Win business deals globally and grow your competitive advantage
Enhance your business reputation
Create a resilient and efficient Information Security Management System
Align business processes with information security & safeguard all types of organizational data
Avoid potential data breaches and penalties
Comply with legal, regulatory, and contractual requirements
Receive an authentic and independent review of your security posture
Some of the key processes covered as part of the ISO 27001 Certification process are:
Risk assessment
Organizational structure evaluation
Information categorization
Access control
Implementation of various information security policies
Physical and technical protection of information
How long does it take to get ISO 27001 Certified?
This is most likely the second most often asked question concerning ISO 27001. Most companies anticipate the duration for compliance to be a couple of weeks. However, this is not realistic. The actual duration to implement ISO 27001 controls and prepare for certification ranges from a few months for small businesses to more than a year for larger corporations. The certification process takes a few weeks once your organization is fully prepared.
We recommend a strong focus on quality while conducting your initial gap analysis and risk assessment, designing the ISMS and ensuring that the safeguards and controls are compliant with ISO 27001 standards. Organizations that prioritize speed and cost-savings above quality, may pay a higher price by having to re-do the process. This also results in a high level of confusion in the workforce who may be accustomed to the original insecure way of maintaining information.
Timelines for ISO 27001 Implementation and Certification
The primary implementation effort is focused on the ISO 27001 “Plan” and “Do” phases of a PDCA cycle. These are the first two obligatory stages when a risk assessment is performed and all safeguards (security controls) are applied.
The size of the organization determines the duration of these two phases:
Organization Size | Duration of ISO 27001 Implementation |
|---|---|
1-20 employees | Up to 3 months |
20 – 50 employees | 3 – 5 months |
50 – 200 employees | 5 – 8 months |
>200 employees | 8 – 20 months |
These are rough estimates since the actual duration varies from organization to organization. In our experience as a Certifying Body, it usually takes 3- 5 months on average. However, these estimates may be realistic if a consultant or an online tool is used to assist with implementation. It may take longer if the preparation is done solely in-house by employees who are not well-versed with the most recent ISO 27001 standards.
Following implementation, the certification process is often separated into three steps:
1) A review of the documentation – The certification auditor will inspect all of your management system documentation to ensure that everything is in place to meet the criteria. This takes 1-3 days on average.
2) A certification audit – The certification auditors will check all of your processes at your site, comparing them to what was documented and verifying compliance. The Initial Audit ISO 27001 Certificate will be issued based on the auditor’s recommendations and report. The Certificate is valid for three years, subject to successful annual surveillance audits. The duration is based on the number of employees. For small-medium organizations, this takes 5-15 days on average.
3) Surveillance and maintenance audits – There will be surveillance audits for the next 2 years after the Initial Audit. At the end of 3 years, the certified organization will have to undergo recertification. During this time, certification auditors will visit and evaluate a sample of system procedures to ensure that you maintain the system. The complete system is meant to be audited during monitoring, but not all at once.
Surveillance and maintenance audits usually take 30% – 40% of the time taken for the certification audit, approximately 2-5 days.
What is the cost of ISO 27001 certification?
This is a critical question while considering ISO 27001. Once an organization decides to proceed with ISO 27001, they need to evaluate cost estimates for implementation/compliance and certification. These are 2 separate processes. While it is not possible to give a fixed amount, we have observed a trend.
Service | Criteria | *Cost Estimate (USD) |
|---|---|---|
ISO 27001 Implementation / Compliance | Small-Medium organizations | $ 10,000 – $ 20,000 * |
ISO 27001 Certification
(Stage 1, Stage 2, and Reporting) | The cost is based on the number of employees and number of days | $ 10,000 – $ 20,000 * |
To get a customized quote for your organization, we encourage you to schedule a meeting or request a quote.
*Disclaimer:
The cost estimates are based on the maturity level of the security architecture, the time required for readiness assessment, stage 1 and stage 2 audits, and the number of employees. They are, at best, only an estimate. Organizations are required to request a quote to obtain the actual cost they will incur and the duration of each service, as well as to select the engagement model best suited to their environment.
Download our ISO 27001 Certification Guide
Penalties for Non-Compliance with ISO 27001
While there are no direct legal penalties associated specifically with ISO 27001 non-compliance, the consequences of information security failures can be significant:
Data Breaches and Financial Loss: Failing to implement proper information security measures can lead to data breaches, resulting in financial losses, including costs related to breach management, regulatory fines, and compensation to affected clients.
Legal Consequences: Lack of compliance with ISO 27001 may lead to failure in meeting regulatory requirements, such as GDPR, CCPA, or HIPAA. This can result in significant legal penalties and litigation costs.
Loss of Business Opportunities: Many businesses require their partners or vendors to be ISO 27001 certified. Non-compliance could mean a loss of contracts or partnerships and missed business opportunities.
Reputation Damage: Failure to protect sensitive data can damage an organization’s reputation. Customers, stakeholders, and partners may lose trust, and the organization may face negative publicity that impacts its standing in the marketplace.
Employee Responsibilities under ISO 27001
Employees are at the core of maintaining ISO 27001 compliance. Below are some of the essential responsibilities you should be aware of:
Follow Security Policies and Procedures: Employees must be familiar with and adhere to all information security policies and procedures. This includes access control policies, password management, and restrictions on sharing data without authorization.
Participate in Risk Management: Employees should report potential security risks or vulnerabilities to the compliance or IT security team. Identifying risks early helps prevent incidents and ensures corrective actions can be taken.
Use Strong Authentication and Access Control: Access to sensitive information should be restricted to authorized personnel only. Employees must use strong, unique passwords and refrain from sharing login credentials. Multi-factor authentication (MFA) should be enabled where possible.
Secure Devices and Workspaces: Keep devices such as laptops and workstations locked when not in use. Do not leave documents containing sensitive information unattended. Ensure physical security by locking office spaces or using access-controlled areas.
Report Security Incidents Immediately: If you encounter a security incident, such as phishing attempts, lost devices, or unauthorized access, report it immediately to your information security officer. Prompt reporting helps contain threats before they escalate.
Stay Up to Date on Security Awareness & Phishing Awareness Training: Complete any security awareness and phishing awareness training required by the company. Training helps you recognize threats like phishing and understand the best practices for handling information securely.
Best Practices for Compliance with ISO 27001
Follow a Clean Desk Policy: Keep your workspace free of sensitive information when not in use. Lock documents in secure storage and avoid leaving personal data visible on desks.
Encrypt Sensitive Data: Always use encryption for data that is being transmitted externally or stored in a potentially insecure location. Encryption is crucial for preventing unauthorized access to information.
Use VPN for Remote Work: Employees working remotely must use Virtual Private Networks (VPN) to connect securely to the company network. This ensures that sensitive data is not exposed when using external networks.
Practice Vigilance Against Social Engineering: Be cautious when handling unsolicited emails, calls, or messages. Always verify the identity of individuals requesting sensitive information. Avoid phishing and social engineering attacks by following protocols for verifying authenticity.
Monitor Access and Activity: Maintain an understanding of who has access to sensitive information and log any actions involving this information. Monitoring helps ensure that data is accessed only by authorized individuals and provides an audit trail in case of a security incident.
Audit and Evaluate the ISMS Regularly: Regular internal audits help assess the effectiveness of the ISMS. Participation in these audits ensures that everyone complies with ISO 27001 standards and that potential gaps are addressed.
ISO 27001 provides a strong framework for managing information security and protecting sensitive data within the organization. It affects a wide range of industries that handle confidential or sensitive information, and every employee has an important role to play in ensuring compliance.
Maintaining compliance with ISO 27001 is not only about meeting a standard—it’s about maintaining the trust of our customers, partners, and stakeholders. By following security policies, practicing good data hygiene, and staying vigilant, each of us can contribute to a culture of security within the organization.
Remember, safeguarding information is a collective responsibility. With everyone doing their part, we can ensure that our information assets are protected, regulatory requirements are met, and our business remains resilient against cyber threats and data breaches.
Download our ISO 27001 Certification Guide
databrackets and your ISO Journey
databrackets has a team of certified ISO Lead Auditors. We help organizations achieve their ISO goals by supporting them with:
ISO 27001 Certification
Do-It-Yourself ISO 27001 assessment toolkit
All our ISO services involve the use of our secure and user-friendly online assessment platform called ‘dbACE’. On this platform we identify gap areas, prioritize solutions, and help organizations demonstrate compliance with ISO 27001 standards. We offer a ‘Readiness Assessment’ through our DIY solution.
In our DIY (Do It Yourself) assessment toolkit, all the clauses and controls stipulated by ISO 27001 standards are uploaded. Customers need to upload their data along with evidence and mark the clause/controls’ ‘implementation’ status for Stage 1 and Stage 2 Assessments.
Our auditors conduct an impartial assessment based on the evidence provided and record their findings on our platform. This helps them communicate the results and seek corrective measures wherever necessary – all in one location. The dbACE interface makes the turnaround quicker and saves time, effort and, thereby, costs. The documentation for the audit from start-to-finish takes place on this platform. This includes the final report that reflects the status of the customer’s adherence to ISO 27001 standards and guidelines.
If your organization is transitioning from ISO 27001:2013 to 27001:2022, explore our blog: Transition to ISO 27001:2022
Explore our ISO 27001 FAQs
The updated standard has a simpler framework that may be adopted throughout an organization. ISO 27002 has been updated and may now be used to manage a broader risk profile. This includes information security and the more technical components of physical security, asset management, cyber security, human resource security, and privacy protection. Read More
Since ISO 27001 is primarily a framework for establishing an ISMS, it will not address all of the particular regulations of the European Union’s General Data Protection Regulation (GDPR). However, when combined with ISO 27701, which addresses the construction of a data protection system, enterprises will be able to satisfy the GDPR obligations to a large extent.
While ISO 27001 addresses general information and data management, the Sarbanes–Oxley Act (SOX) addresses how financial controls are in place for public companies in the United States. Fortunately, organizations with a broad scope of data management may use ISO 27001 certification to demonstrate compliance with SOX rules.
ISO 27001 specifies the standards for an Information Security Management System (ISMS), whereas ISO 27002 details how to put ISO 27001 Annex A controls into practice.
In other words, ISO 27001 merely gives a brief overview of each control, but ISO 27002 provides thorough recommendations.
While ISO 27001 is an international standard, the National Institute of Standards and Technology (NIST) is a US government institution that supports and maintains measurement standards in the US, including the SP 800 series of papers, which describes best practices for information security.
The NIST SP (Special Publication) 800 series and ISO 27001 can be used together for information security implementation, even though they are not identical.
While ISO 27001 isn’t a legal mandate, organizations around the world look for B2B partners and vendors who comply with the controls listed under this standard and often demand proof of this through certification. As a result of its popularity, it is prioritized by businesses who want to secure contracts by proving their ability to protect the information they are entrusted with.
Some governments, however, have established legislation requiring specific industries to get certified ISO 27001.
Compliance with ISO 27001 can be defined as a legal obligation in contracts and service agreements between public and private enterprises. Furthermore, nations can specify laws or rules that implement ISO 27001, a legal necessity for enterprises operating on their territory.
| Criteria | SOC 2 | ISO 27001 |
| Definition | SOC 2 refers to a collection of audit reports that demonstrate the level of conformance to a set of defined criteria (TSC) | ISO 27001 is a standard that defines specifications for an Information Security Management System (ISMS). |
| Regional applicability | SOC 2 is primarily for the United States | ISO 27001 is globally respected |
| Industry-specific applicability | SOC 2 is more popular in the financial industry and data centre and data hosting organizations | Enterprises of any size or industry |
| Compliance | SOC 2 is attested by a licensed Certified Public Accountant (CPA) | ISO 27001 is certified by an ISO certification body |
| Methodology | SOC 2 demonstrates system security against static principles and standards | ISO 27001 is intended to define, implement, operate, regulate, and enhance total security |
Both SOC 2 and ISO 27001 are excellent compliance initiatives that organizations may use to obtain a competitive edge, show the design and operational effectiveness of internal controls, and achieve regulatory compliance.
If you’re primarily conducting business in the US, databrackets recommends that you consider SOC 2 examination as your first option. However, if you are planning on having a global presence, then ISO 27001 is more suited to meeting those goals. Both standards have been used interchangeably to implement security controls and provide assurance to customers and partners.
Certainly, combining the two can provide various benefits in terms of competitive advantage and audit efficiency since there are significant overlaps between the subject areas of SOC 2 and ISO 27001.