Security Risk Analysis Requirements for Quality Payment Program (MACRA/MIPS)
The Quality Payment Program implements provisions of MACRA, the Medicare Access and CHIP Reauthorization Act of 2015, to reform Medicare Part B payments. The QPP improves Medicare payments by helping you focus on care quality and the one objective that matters most — making patients healthier. The QPP includes two tracks- the Merit-based Incentive Payment System (MIPS) and the Advanced Alternative Payment Models track (AAPMs). Most of the eligible professionals in 2018 will report under MIPS. Under the QPP, CMS has consolidated and replaced three previous programs- PQRS, Meaningful Use, and the Value-based Payment Modifier, and created one new program with four performance categories: Quality, Cost, Improvement Activities, and Advancing Care Information (ACI).
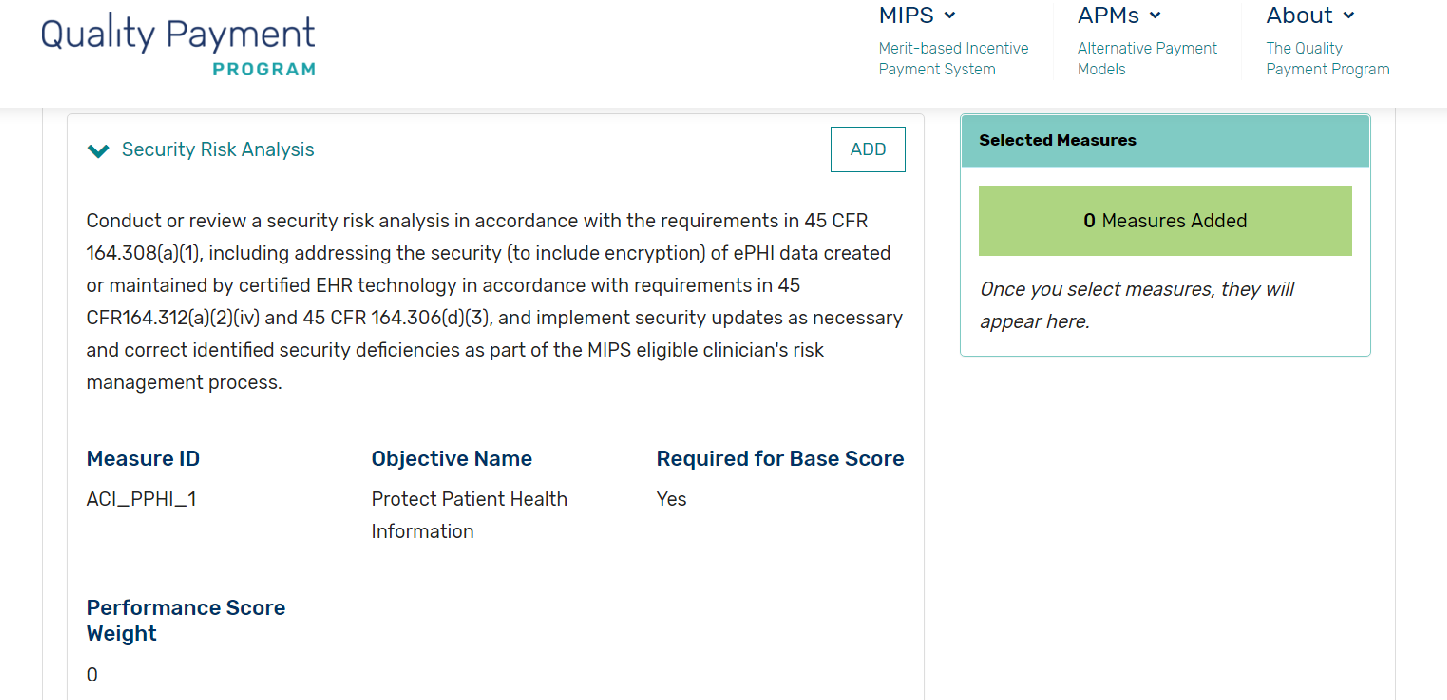
To satisfy the 2018 ACI base measures, clinicians participating in the MIPS program need to conduct a thorough security risk analysis of their certified Electronic Health Record Technology, according to the measure specification:
Conduct or review a security risk analysis in accordance with the requirements of 45 CFR 164.308(a)(1), including addressing the security (to include encryption) of ePHI data created or maintained by certified EHR technology in accordance with requirements in 45 CFR164.312(a)(2)(iv) and 45 CFR 164.306(d)(3), and implement security updates as necessary and correct identified security deficiencies as part of the MIPS eligible clinician’s risk management process.
Let’s translate the requirements and CFR (Code of Federal Regulations) for MIPS participants:
- CMS/Medicaid agencies are expecting all participants to conduct a formal security risk analysis of electronic Protected Health Information (ePHI) managed as part of their EHR implementation.
- The scope of the analysis includes all devices, connecting interfaces, and other systems involved in creating, storing, transmitting, and receiving patient data
- Based on our consulting and auditor engagements, here’re the five key elements that need to be covered as part of the security risk analysis:
- Technical security risk assessment (SRA)
- SRA includes but is not limited to network vulnerability scan, password management, encryption, patch management, anti-virus, timeout, and other key security best practices.
- Security risk assessment document with proper prioritization of identified risks, along with plan to mitigate the risks.
- Policies and procedures
- Covered entities should have in place an information security policy document covering guidelines for handling patient data in your organization. Acceptable usage policy, sanction policy, and removable media usage, etc. should be included as part of this document.
- Security awareness training
- Ensuring all staff is trained at least annually on your policies and procedures, along with HIPAA/HITECH requirements, is an important aspect of security best practices.
- Business Associate Contracts
- Signed business associate contracts must be active and up-to-date with all the vendors you are doing business with, which may have access to PHI.
- Other documentation
- This involves maintaining evidence to demonstrate you comply and are taking steps to address identified risks. Forg., reviewing of user accounts to your EHR system periodically to confirm only authorized personnel to have access.
- Technical security risk assessment (SRA)
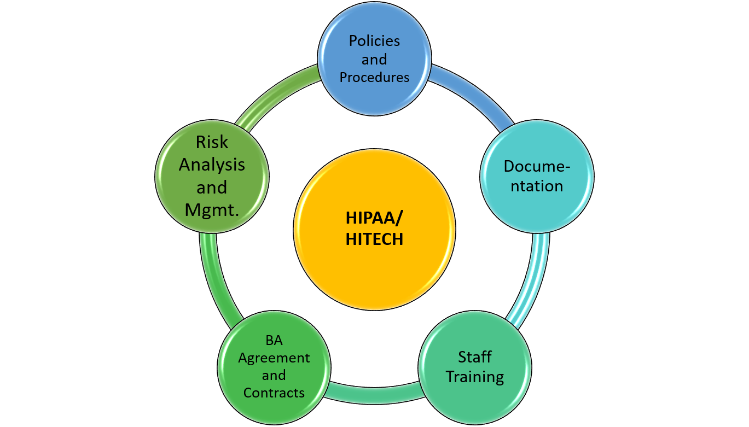
The above-mentioned areas of focus will help organizations to show their due diligence and demonstrate that the core measure, “Protect Patient Health Information,” required in the MIPS/MACRA program, is satisfied.
EHR 2.0 specializes in providing consulting in the area of security and compliance assessments, and we can work to provide the documents required by auditors as we have for hundreds of our customers.
If interested to receive an estimate for Security Risk Assessment and Compliance Consulting services, you can provide preliminary details at databrackets.com/request-for-quote.