While a SOC 2 report is often associated with technology companies and cloud service providers, its principles are equally applicable and beneficial to organizations in the healthcare sector, including radiology and imaging systems. Healthcare providers are legally required to focus on compliance with the Health Insurance Portability and Accountability Act (HIPAA). However, due to the data breaches in Hospitals, Healthcare Insurance Providers, and other Healthcare businesses facing a cyber attack due to their vendors, business partners have begun requesting proof of strong cybersecurity and data privacy controls before sharing Protected Health Information (PHI).
A predominant reason for SOC 2 becoming a part of the Vendor Security Assessment or Request for Quote process can be attributed to the fact that HIPAA compliance does not require an audit by an independent licensed auditor. Repercussions of non-compliance and deviation from HIPAA rules are penalized and investigated, but there is no proof of compliance that helps Healthcare Vendors and Radiology organizations secure business contracts. Additionally, the HHS Office for Civil Rights (OCR), responsible for HIPAA enforcement, prioritizes other areas beyond investigating HIPAA complaints. Also, business partners usually require more security controls and look for vendors who go beyond HIPAA Compliance. This is where a SOC 2 Examination (often called a SOC 2 Certification) by an independent and licensed CPA comes into play.
SOC 2 Certification is beneficial for radiology organizations in several ways. It encompasses critical components of Radiology IT architecture such as Digital Imaging and Communications in Medicine (DICOM), Picture Archiving and Communication Systems (PACS), Radiology Information Systems (RIS) standards, and Protected Health Information (PHI). By undergoing a SOC 2 audit and obtaining a SOC 2 report, you can provide assurance to stakeholders, including patients, healthcare providers, and regulatory bodies, that you have implemented robust controls to protect sensitive data and ensure the reliability of your services. This enhances trust and confidence and strengthens your organization’s competitive position in the healthcare market by demonstrating your commitment to data security and compliance. Additionally, SOC 2 reports are typically issued annually, necessitating that companies undergo at least one annual audit by a third party.
Why Businesses prefer Radiology and Imaging Partners
with a SOC 2 Certification
Businesses prefer radiology and imaging partners with a SOC 2 certificate for several reasons, all of which contribute to ensuring the security, reliability, and compliance of the services provided. Here are the key reasons explained:

1. Annual testing of Controls by an Independent Licensed Third Party: HIPAA rules are stringent but compliance is not audited and security controls are not tested periodically by a third party. SOC 2 Certification requires an annual evaluation by a licensed CPA through a SOC 2 Audit wherein an organization’ security controls are tested. An organization cannot self attest as being SOC 2 Compliant and this is the key differentiating factor that business partners look for.
2. Data Security Assurance: A SOC 2 certificate provides businesses with assurance that their sensitive data, including medical images, reports, and patient information, is adequately protected against unauthorized access, breaches, or tampering. By adhering to SOC 2 security controls, radiology and imaging partners demonstrate a commitment to robust security measures like encryption, access controls, and monitoring to safeguard confidential information. In addition, SOC 2 reports mandate that companies perform regular vulnerability scans and penetration testing of their environments. This is especially critical in the radiology industry, which relies heavily on technological infrastructure to manage medical images.
3. Regulatory Compliance Confidence: Businesses operating in highly regulated industries, such as healthcare, require partners who comply with industry-specific regulations and standards, such as HIPAA (Health Insurance Portability and Accountability Act). A SOC 2 certificate serves as evidence that radiology and imaging partners have implemented controls to meet regulatory requirements related to data security, confidentiality, and privacy, thereby reducing the risk of non-compliance penalties and legal consequences.
4. Risk Mitigation: SOC 2 compliance involves thorough risk assessments and implementing risk management strategies to identify, assess, and mitigate security risks and vulnerabilities. By partnering with radiology and imaging providers who adhere to SOC 2 principles, businesses can mitigate the risk of data breaches, service interruptions, and reputational damage associated with inadequate security controls or non-compliance with industry standards.
5. Service Reliability and Availability: SOC 2 compliance requires radiology and imaging partners to ensure the reliability and availability of their services, even in the face of unexpected disruptions or system failures. By implementing redundancy, failover mechanisms, and disaster recovery plans, radiology, and imaging partners can minimize downtime and ensure uninterrupted access to critical medical imaging services, thereby enhancing business continuity and operational efficiency for their clients.
6. Trust and Reputation Building: SOC 2 certification is a recognized and preferred industry standard that demonstrates a commitment to security, reliability, and compliance with best practices in data management and governance. Businesses prefer to partner with radiology and imaging providers who have obtained SOC 2 certification as it instills trust and confidence in the partnership, strengthens the provider’s reputation, and fosters long-term relationships based on transparency and accountability.
Businesses prefer radiology and imaging partners with a SOC 2 certificate because it provides assurance of data security, regulatory compliance, risk mitigation, service reliability, and trustworthiness. By choosing SOC 2-certified partners, businesses can mitigate risks, ensure the confidentiality and integrity of their data, and build strong, mutually beneficial partnerships focused on delivering high-quality, secure healthcare services.
What kind of Radiology Data does SOC 2 evaluate?
Radiology organizations typically store various types of data critical to their operations and patient care. Security controls listed under SOC 2 evaluate if these types of data meet the AICPA’s Trust Service Criteria. These include:
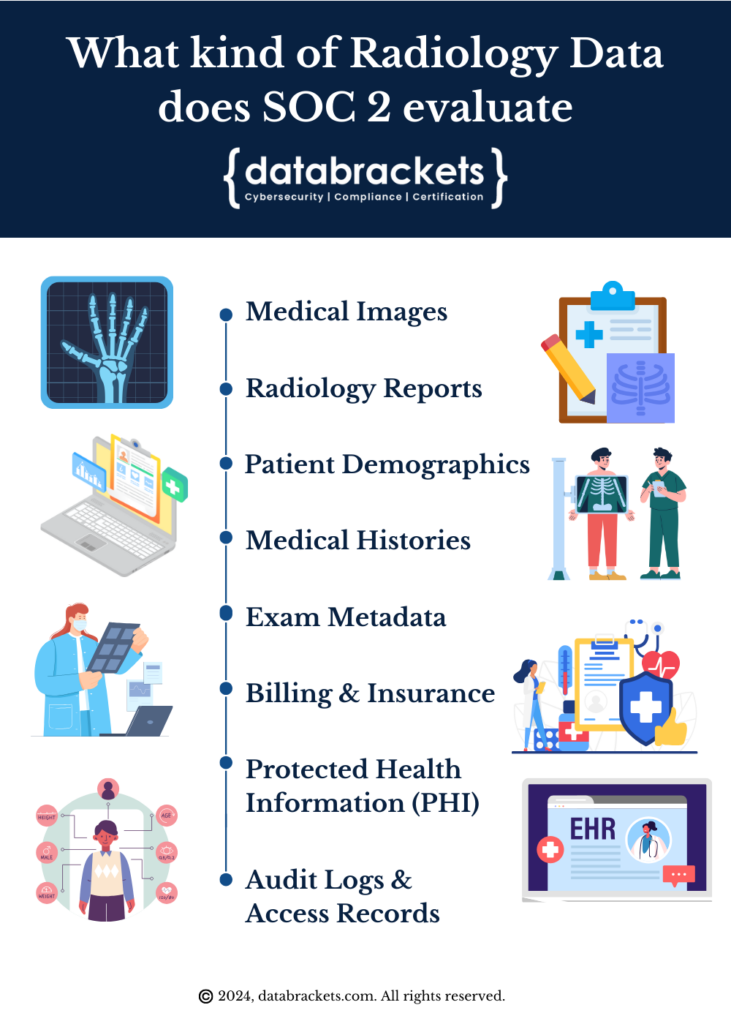
1. Medical Images: X-rays, MRI scans, CT scans, ultrasound images, and PET scans. These images are essential for diagnosis, treatment planning, and monitoring of patient health.
2. Radiology Reports: Generated by radiologists interpreting medical images. These reports contain findings, diagnoses, and recommendations for further treatment or follow-up.
3. Patient Demographic Information: Including names, dates of birth, genders, addresses, and contact details. This data is used for patient identification and communication.
4. Medical Histories: Information about patients’ medical conditions, previous treatments, allergies, and medications. This data helps radiologists contextualize imaging findings and make accurate diagnoses.
5. Exam Metadata: Such as exam dates, times, types of imaging procedures performed, and the equipment used. This metadata is crucial for tracking patient exams, managing scheduling, and ensuring quality control.
6. Billing and Insurance Information: Insurance policies, billing codes, and payment records. This data is essential for reimbursement and financial management.
7. Protected Health Information (PHI): Any information that can be used to identify an individual and is related to their physical or mental health condition in the past, present, or future. This includes all the aforementioned types of data and must be protected in accordance with healthcare privacy regulations such as HIPAA.
8. Audit Logs and Access Records: Records of who accessed patient data, when, and for what purpose. These logs are crucial for monitoring data access, detecting unauthorized activities, and demonstrating compliance with regulatory requirements.
By securely storing and managing these types of data, radiology organizations play a crucial role in supporting patient care, medical research, and healthcare operations while ensuring compliance with relevant privacy and security regulations. SOC 2 Compliance helps them prove the effectiveness of their security measures to stakeholders and potential business partners.
SOC 2 Controls and Radiology IT Architecture
Radiology organizations must demonstrate the security and confidentiality of patient data and the availability and integrity of their imaging systems. SOC 2 audits evaluate the resilience of PACS, RIS, and DICOM infrastructure to ensure continuous availability, resilience to system failures, and timely access to critical medical images and reports. Additionally, measures such as data backups, disaster recovery plans, and redundancy configurations are assessed to minimize the risk of service disruptions and ensure the integrity of patient data.

Some examples of SOC 2 Trust Services Criteria (TSC) as they relate to Radiology IT Architecture include:
1. PACS (Picture Archiving and Communication Systems)
Access Control: They include role-based access controls within PACS to ensure only authorized personnel can view, modify, or delete patient images and data.
Encryption: Encrypting data at rest and in transit within PACS is critical to protect patient information from unauthorized access or interception.
Audit Logging: Enabling comprehensive audit logging within PACS is essential for tracking user activities, access attempts, and changes made to patient data. This ensures accountability and traceability.
2. RIS (Radiology Information Systems)
Authentication: Implementing robust authentication mechanisms within RIS to verify the identity of users accessing the system helps to prevent unauthorized access to patient information.
Data Integrity: Ensuring data integrity controls within RIS helps to detect and prevent unauthorized alterations or tampering with patient scheduling, workflow management, and administrative data.
Incident Response: Developing incident response procedures within RIS helps your team to promptly address security incidents, breaches, or unauthorized access attempts, minimizing the impact on patient care and data security.
3. DICOM (Digital Imaging and Communications in Medicine)
Data Transmission Security: Implementing secure communication protocols and encryption mechanisms that are compliant with DICOM standards helps protect patient data during transmission between imaging devices and systems.
Interoperability: Ensuring compliance with DICOM standards helps promote interoperability and seamless integration between different imaging devices, systems, and healthcare IT infrastructure components.
4. IoT Devices
Data Transfer and Infrastructure Security: IoT devices include devices that are wireless, work with Bluetooth or chip-enabled technology connected to the internet to send data from the devices to cloud-based systems or a centralized dashboard. If the connectivity between the device and the internet is not secure the data transfer between these devices could be compromised. Ensuring data transfer and infrastructure security helps mitigate the risk of a breach and contamination of the data.
Infrastructure Related Security: If IoT devices have some kind of a footprint through which external hackers can get access, it can potentially be used to get into the network. Ensuring Infrastructure Related Security helps radiology organizations prove their network cannot be infiltrated.
5. Overall Radiology IT Architecture
Risk Management: Conducting regular risk assessments and implementing risk management strategies across Radiology IT Architecture helps to identify, assess, and mitigate potential security risks and vulnerabilities.
Vendor Management: Establishing a robust vendor management process to assess the security posture of third-party vendors providing PACS, RIS, or other radiology IT solutions helps to ensure they meet SOC 2 security requirements and standards.
Business Continuity Planning: Developing and maintaining business continuity and disaster recovery plans for Radiology IT Architecture ensures continuity of operations, data availability, and patient care in the event of system failures, disasters, or emergencies.
Asset Management: Ensuring that all assets and devices are secure helps to prove that the data stored within will remain secure.
By aligning SOC 2 TSC security controls with various components of Radiology IT Architecture, radiology organizations can strengthen their security posture, protect patient data, and demonstrate compliance with SOC 2 security requirements. This ensures the integrity, availability, confidentiality, and privacy of patient information, enhancing trust and confidence among clients, stakeholders, and regulatory authorities.
SOC 2 Compliance for Radiology
As radiology organizations embark on their SOC 2 compliance journey, they will position themselves as leaders in their field, earning the confidence and loyalty of clients and stakeholders.
The SOC 2 reporting process for a Radiology organization heavily emphasizes data flow, security controls implemented by the organization, and those used by their sub-service organizations (vendors). The initial step in the engagement involves identifying the Trust Services Criteria (TSC) essential for the radiology organization. Commonly selected criteria by radiology groups we’ve worked with include:
- Security
- Availability
- Privacy
- Processing Integrity
As your readiness partner, databrackets will conduct an initial gap assessment to pinpoint controls needing further attention. We will assist in remedying these gaps and perform the final readiness assessment before involving one of our CPA partners for the external SOC 2 audit. Throughout this process, databrackets will serve as the main contact for all audit-related inquiries until the engagement concludes successfully with a detailed SOC 2 report. Additionally, databrackets will implement monitoring activities to ensure these controls are continuously operational and maintained, thereby supporting ongoing SOC 2 compliance.
Key Takeaways
Radiology organizations increasingly rely on digital systems and external service providers, making independent assurance over security and availability controls essential to maintaining trust with partners and patients.
SOC 2 is relevant in radiology environments because sensitive imaging data and related workflows require consistent protection across systems that store, process, and transmit regulated information.
The framework helps radiology practices demonstrate that controls are not only defined but operate effectively within complex, technology-driven service environments.
SOC 2 is an attestation rather than a certification, meaning its value comes from how accurately it reflects real operational practices rather than the existence of written policies alone.
Selecting appropriate trust services criteria allows radiology organizations to focus assurance efforts on risks most relevant to imaging services, data handling, and service reliability.
Type I and Type II reports serve different purposes, with one validating control design and the other demonstrating sustained operational effectiveness over time.
Preparing for SOC 2 requires alignment between documented procedures and daily clinical and administrative operations so controls function consistently under real-world conditions.
Evidence collection and process discipline are critical, as auditors evaluate whether controls operate reliably across the assessment period rather than during isolated moments.
For radiology organizations, SOC 2 supports confidence among hospitals, partners, and customers by providing credible, third-party validation of security and operational controls.
SOC 2 Readiness and Examination with databrackets
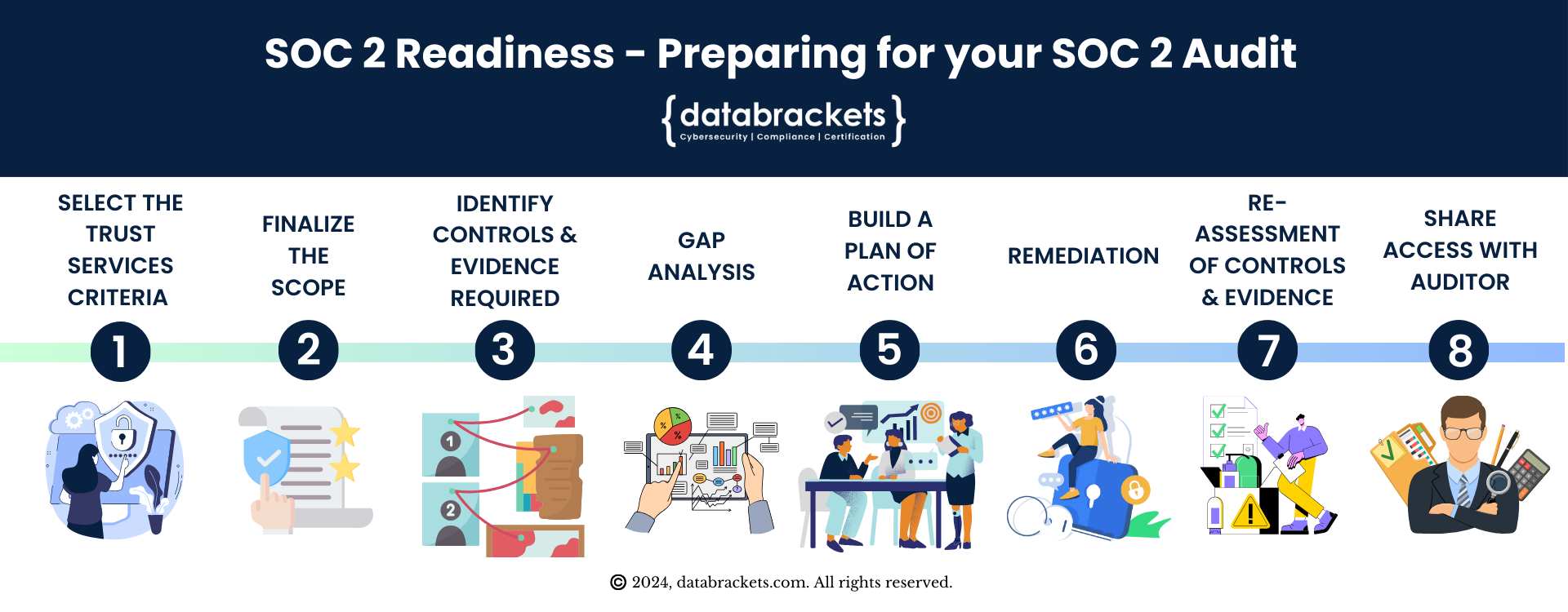
Typically, organizations tend to directly look for a licensed CPA firm and sign up for a SOC 2 Audit. There are several stumbling blocks in this approach and it can lead to superfluous payments that can be avoided. When you approach a licensed CPA, you will not receive guidance on which type of report you need (SOC 1, SOC 2 or SOC 3) or the Trust Services Criteria and security controls for your industry. They are not required to help clients with guidance to implement or prove their SOC 2 Compliance. Their mandate is to conduct an impartial audit and issue a structured report to help your clients understand if your systems are secure.Working with SOC 2 Compliance Readiness Partner can help you save a significant amount of time, money and resources. Our security experts have extensive experience working with clients across industries with the sole purpose of helping to position your organization for a successful audit. The tasks that we undertake, as your SOC 2 Compliance Readiness Partner include:
Initial Consultation and Scoping
Educating the Client
Gap Analysis
Control Mapping
Documentation Review and Development
Remediation Planning
Implementation Support
Internal Audit
Readiness Assessment Report
Ongoing Support and Monitoring
The data of our SOC 2 Readiness clients is maintained in a structured format on our GRC platform – dbACE and is accessible to the CPA that you chose to work with. You can refer to the controls, Trust Services Criteria and the 2 sections of your SOC 2 Report which you need to submit – the Management’ Assertion and a Description of your System, using your unique login. We also collaborate with certified CPA firms whom you can choose to work with, if you decide to do so. Hence, working with a Readiness Partner helps you to not only prepare for SOC 2 Certification but also ensures that your security controls are implemented adequately and you have evidence to prove their effectiveness.
Overview of databrackets
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Summary
To summarize,
Radiology organizations operate in highly digital environments where imaging data, reporting systems, and external service providers must work together securely and reliably.
SOC 2 offers a structured way for radiology practices and service providers to demonstrate that controls protecting sensitive data and system availability are designed and operating as intended.
The framework is particularly relevant in radiology because imaging workflows often involve shared platforms, third-party vendors, and remote access, increasing the importance of transparent control assurance.
SOC 2 reports function as attestations rather than certifications, meaning their credibility depends on how well they reflect actual operational practices instead of policy statements alone.
Selecting appropriate trust services criteria allows radiology organizations to align assurance efforts with the specific risks associated with imaging data handling and service continuity.
The difference between Type I and Type II reports shapes how assurance should be interpreted, with one focusing on control design and the other on sustained operational effectiveness.
Preparing for SOC 2 requires close alignment between documented procedures and everyday clinical and operational activities to ensure controls work consistently in practice.
Evidence collection over time is central to a successful assessment, as auditors evaluate whether controls operate reliably throughout the reporting period.
For radiology organizations, SOC 2 supports trust with hospitals, partners, and customers by providing independent validation of security and operational reliability.