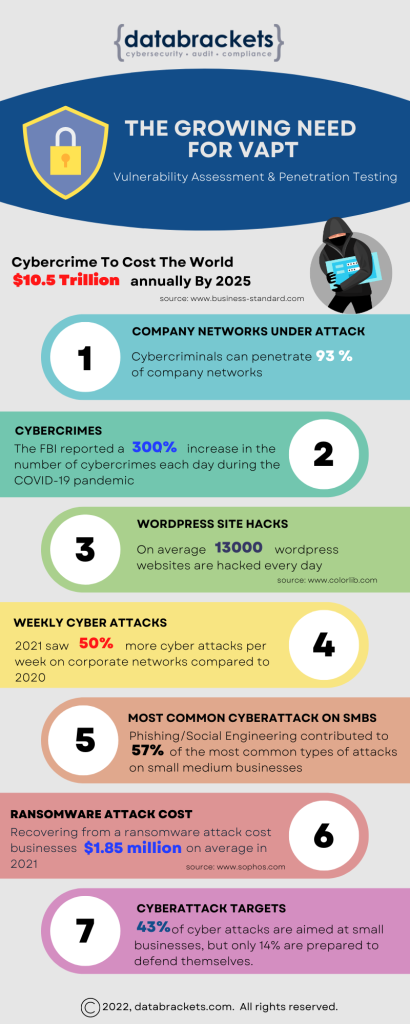
Every business with digital assets is at risk of being hacked, no matter how big or successful it is on a global scale. Reports show one ransomware attack occurred every 11 seconds in 2021. These attacks could hurt anyone, from a multimillion-dollar company to a small business starting to make some sales online.
A vulnerability assessment report tells you where potential risk is and the steps you can take to reduce it. A vulnerability assessment focuses on your systems, network, and the places people can connect.
A Penetration Test or Pentest is an authorized simulated attack on computer systems to assess security. Penetration tests simulate various business-threatening attacks and can examine any system component with the right scope. Penetration testers use the same Tools, Tactics, and Procedures (TTPs) as attackers to find weaknesses in a system and show how they affect business.
Comparing penetration testing and vulnerability assessments helps understand their roles in your organization’s security practices and determine your needs.
Vulnerability Assessment
What is a Vulnerability Assessment?
Vulnerability assessments identify, classify, and prioritize computer, application, and network vulnerabilities. Vulnerability assessments examine information system security flaws; it checks for vulnerabilities, assign severity levels, and suggest solutions.
Why are Vulnerability Assessments needed?
A vulnerability assessment determines an organization’s areas that need improvement. This process helps the company understand its assets, security flaws, and risk, reducing the likelihood of a cyberattack. It also guides risk assessment for weaknesses.
Depending on your organization, you may need regular vulnerability assessments to stay compliant. Compliance regulations have evolved to address security issues and vary by region/industry. Examples include GDPRs, PCI DSS, and HIPAA. These standards require regular assessments to demonstrate sensitive customer data is being protected properly. Vulnerability Assessments are comprehensive security processes that include:
- Checking security protocols
- Password safety of routers and Wi-Fi networks
- Reviewing network strength against network intrusions, DDoS, and MITM attacks
- Network port vulnerability scanning
How often do you need to perform a Vulnerability Assessment?
How often assessments must be done is set by compliance requirements. While legal regulations may require them less frequently, in the best-case scenario, assessments should be done once a month. Businesses generally get the recommendation to scan their internal and external systems at least once every three months.
Major standards’ frequency levels:
- Payment Card Industry Data Security Standards (PCI DSS): Every three months
- The Health Insurance Portability and Accountability Act (HIPAA): Does not require scanning but mandates that a detailed assessment process must be set up
- Cyber Security Maturity Model Certification (CMMC): Once a week to once every three months, depending on what auditors need
- National Institute of Standards and Technology (NIST): Every three to four months, depending on how the organization is run
What’s in the Vulnerability Assessment Report?
Vulnerability Assessment involves vulnerability scanning and technical judgment. A Vulnerability Assessment report includes an organization’s security policy and other security products utilized. The Vulnerability Assessment suggests risk-mitigation measures afterward.
A Vulnerability Assessment report analyzes an organization’s systems, identifies vulnerabilities, and rates their severity. Security professionals use automated and manual testing tools for these assessments.
How do Vulnerability Assessments benefit you?
Vulnerability Assessments help you:
- Discover security flaws to help organizations stay one step ahead of attackers
- Catalog all network devices, including the purpose and system information
- Plan upgrades, installations, and inventory of all enterprise devices
- Define network risk
- Optimize security investments with a business risk/benefit curve
How do you perform a Vulnerability Assessment?
- Establishing the testing scope
Establish a Vulnerability Assessment methodology:
- Locate your sensitive data
- Find hidden data
- Identify mission-critical servers
- Select systems and networks
- Check ports, processes, and configurations
- Map the IT infrastructure, digital assets, and devices
- Streamline the process
- Identifying vulnerabilities
Conduct a vulnerability scan of your IT infrastructure and list all security threats. This step needs an automated vulnerability scan and a manual penetration test to ensure correct results and reduce false positives.
- Analyze
A scanning tool generates risk and vulnerability assessments. Most tools have a CVSS (common vulnerability scoring system) score. These scores show weaknesses. Prioritize them by severity, urgency, potential damage, and risk.
- Addressing vulnerabilities
After identifying and analyzing vulnerabilities, choose a fix—options include mediation and remediation.
Remediation resolves vulnerabilities. It can be done by installing security tools, keeping products up to date, or using other methods. All stakeholders must participate in vulnerability remediation based on identified priorities.
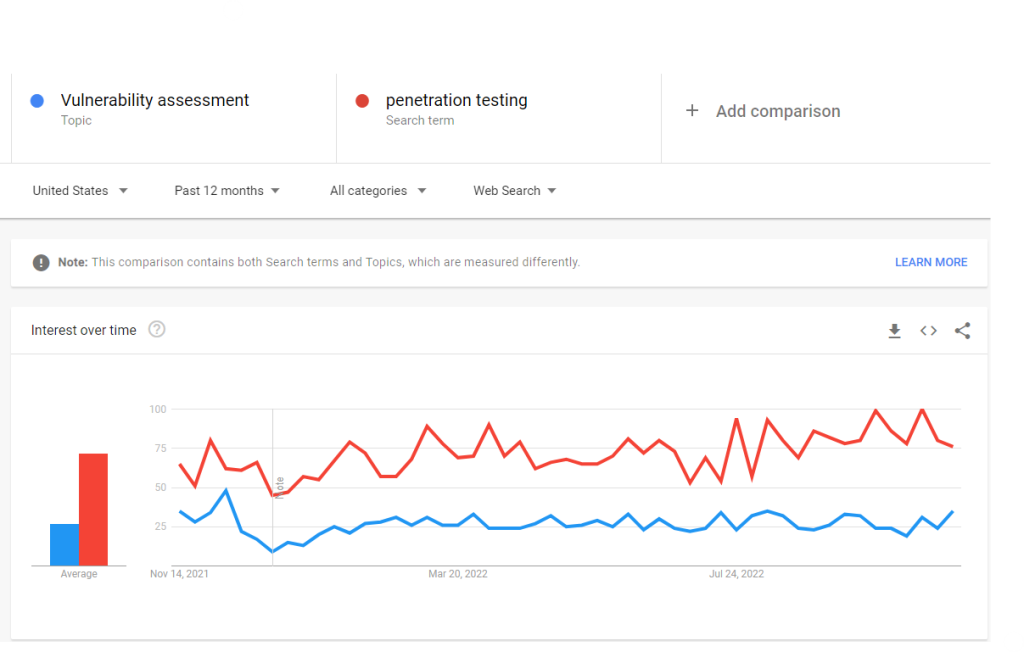
Google Trends for Vulnerability Assessment vs. Penetration Testing
Google trends show that penetration testing’s relative interest nearly peaked last year. Organizations are grouping Vulnerability Assessment and Penetration Testing (VAPT) to improve security maturity.
Penetration Testing
What is Penetration Testing?
Penetration Testing (or Pentest) is the authorized simulation of various business-threatening attacks on computer systems to evaluate security. Penetration tests determine if a system can handle attacks from authenticated and unauthenticated users and system roles. Pen testers use the same tools, methods, and processes as attackers to find weaknesses in a system and show how they may affect business. Pentest can examine any system component with the right scope.
Why is Penetration Testing important?
- Find vulnerabilities that traditional IT security tools miss
- Identify weak spots in an application or network that hackers might use to get into the system
- Establish customer and company trust
- Protect company data and reputation; data leaks ruin reputations
Preparing for attacks from hackers or employees who leak confidential information is important. A non-destructive penetration test can identify security vulnerabilities before an attack and recommend improvements.
How often do you need to perform Penetration Testing?
At least once a year, penetration testing should be performed to improve IT and network security management and to reveal how malicious hackers may exploit newly discovered threats (0-days, 1-days) or emerging vulnerabilities. For example, PCI DSS compliance requires annual penetration testing or major infrastructure or application upgrades.
IT Governance recommends an annual Level 2 penetration test for high-profile or high-value organizations. Organizations with a low-risk appetite should do level 1 penetration tests often (usually every three months).
What’s in the Penetration Testing report?
Penetration Testing reports detail security test vulnerabilities. The report lists weaknesses, threats, and solutions. The Pen Test Report provides a complete overview of vulnerabilities with a POC (Proof of Concept) and priority remediation rating for each issue and its impact on your application/website.
A good penetration testing report includes an executive summary, vulnerabilities, business impact, and recommendations to fix them.
How do you perform Penetration Testing?
Planning and reconnaissance, scanning, system access, continued access, and analysis/report comprise the penetration testing process. Ethical hackers can look at a system, figure out its strengths and weaknesses, then choose the best tools and methods to break into it. Penetration testing begins long before a simulated attack.
Planning and Reconnaissance
The first penetration phase involves simulating a malicious assault to obtain as much system information as possible. Ethical hackers look at the system, its weaknesses, and how the technology stack reacts when a system is broken. The methods include Social engineering, dumpster diving, network scanning, and domain registration information retrieval. Employee names, emails, network topology, and IP addresses are searched. The audit goals determine the type of information and investigation depth.
Scanning
Penetration testers scan systems and networks based on planning findings. The scan identifies system vulnerabilities that could be exploited for targeted attacks. All this information is crucial to the success of the next steps.
System Access
Pen testers use system vulnerabilities to enter infrastructure. They escalate privileges to show how deep they can get into target environments.
Continued Access
In this step, the Pentest identifies which data and services one can access to gain the most privileges, network knowledge, and system access. Pentesters should stay in a system long enough to mimic hostile hackers’ intentions.
Analysis and Reporting
The security team writes a comprehensive penetration testing report of their results at the last stage. Finally, they recommend safeguards to prevent future attacks. Attacks have skyrocketed in recent years and don’t appear to be slowing down, so the number of precautions needs to be adjusted accordingly.
How does Penetration Testing benefit you?
- Reveals the system’s weaknesses
- Reveals the system’s strengths
- Prevents Hackers from Infiltrating Systems
- Verifies if your system design meets the current regulations
- Helps ensure an experienced hacker cannot access your data
- Shows how a hacker might attack your system. This distinguishes them from most other testing choices
- Helps establish customer trust, showing you’re correcting problems and working hard to serve clients well
- Helps budget your security expenditure
Vulnerability Assessment vs. Penetration Testing
Vulnerability Assessment vs. Penetration Testing | Vulnerability Assessment | Penetration Testing | |||
|---|---|---|---|---|---|
Purpose | Identifies, analyzes, remedies, and discloses security problems. Security techniques help companies limit their “attack surface.” | Detect and exploit computer system flaws. This simulated attack finds vulnerabilities that attackers could exploit. | |||
Frequency | On average, it is performed every quarter | At least once a year | |||
Scope | Finds and categorizes system vulnerabilities. | Exploits weaknesses for insights. | |||
Report | Lists all system vulnerabilities detected during a scan by severity and offers fixes. | Details vulnerabilities found during a security test, list flaws, threats, and possible remedies. | |||
Performed by | Vulnerability scanning is a largely automated process | Penetration testing is a hybrid process that combines automated scanning with manual interaction. | |||
Timeline | Automated vulnerability assessment saves time and money. | A penetration test is a time-consuming and costly process. | |||
Cost | Vulnerability assessments typically cost $2,000–$2,500, depending on the number of IPs, servers, or apps checked. | Website penetration testing costs $349–$1499 per scan. | |||
Depending on your needs, SAAS or web application scans cost $700–$4999. | |||||
Website penetration tests cost $2500–$50,000. | |||||
Pentesting mobile and web apps cost $1500–$5000. | |||||
Cloud, network and device pen testing quotes vary in cost $400–$2000. | |||||
White-box penetration testing: $500–$2000 per scan | |||||
Black-box penetration testing: $10,000–$50,000 per scan | |||||
Grey-box penetration testing: $500–$50,000 per scan | |||||
Limitation | Rarely yield zero false positives. | Exposes the network to fraudsters, hackers, or severe data loss. | |||
Best Suited | Suitable for a multimillion-dollar SaaS firm or a small e-commerce venture that relies on data that must routinely check for security flaws. | Ideal for firms with sophisticated applications and valuable data. | |||
Depth | The report will detail all potential vulnerabilities and may rank vulnerabilities by network threat. | The penetration tester acts like a hacker to attack vulnerabilities (in an ethical manner) without stealing, exploiting, or destroying network data. | |||
Why might an organization need to conduct Vulnerability Assessments and Pen Testing?
Most of the time, Vulnerability Assessments and Penetration Tests are grouped. A good security program will use vulnerability and penetration testing to improve security maturity.
Conclusion
Vulnerability scans are often confused with penetration tests but provide different benefits. The best vulnerability management solutions regularly find, evaluate, report, and rank weaknesses in software and network systems. The findings are presented in an easily understandable format to protect your business-critical assets.
Vulnerability scans cannot replace penetration tests. Vulnerability scans identify risks at a high level while penetration testers investigate them. Penetration tests can show if vulnerabilities can be exploited to access your environment, whereas vulnerability scans cannot. Most vulnerability scans are automated, making them a better option for daily use. Alongside penetration tests, reviewing your environment’s vulnerabilities frequently can alert you to new vulnerabilities and their severity.
How can databrackets help with VAPT?
Before an attacker can discover the network, application, cloud service, and code vulnerabilities, databrackets’ A2LA-accredited process and pen testers can quickly and cost-effectively identify security vulnerabilities.
Contact us to learn more about how our services and specialists can help your company defend against security threats and attacks.