If you are a SaaS platform provider, it is increasingly important to demonstrate your security and privacy implementations through a third-party independent audit report, such as SOC 2. A SOC 2 Examination (often called a SOC 2 Certification) is a tool to help you do that because it creates standardization in how security controls are grouped into AICPA’s Trust Services Criteria and how licensed and experienced CPAs can test their effectiveness. Businesses trust SOC 2 certification for several reasons, which also explains why they often require it as part of their Request for Quotation (RFQ) or vendor selection process.
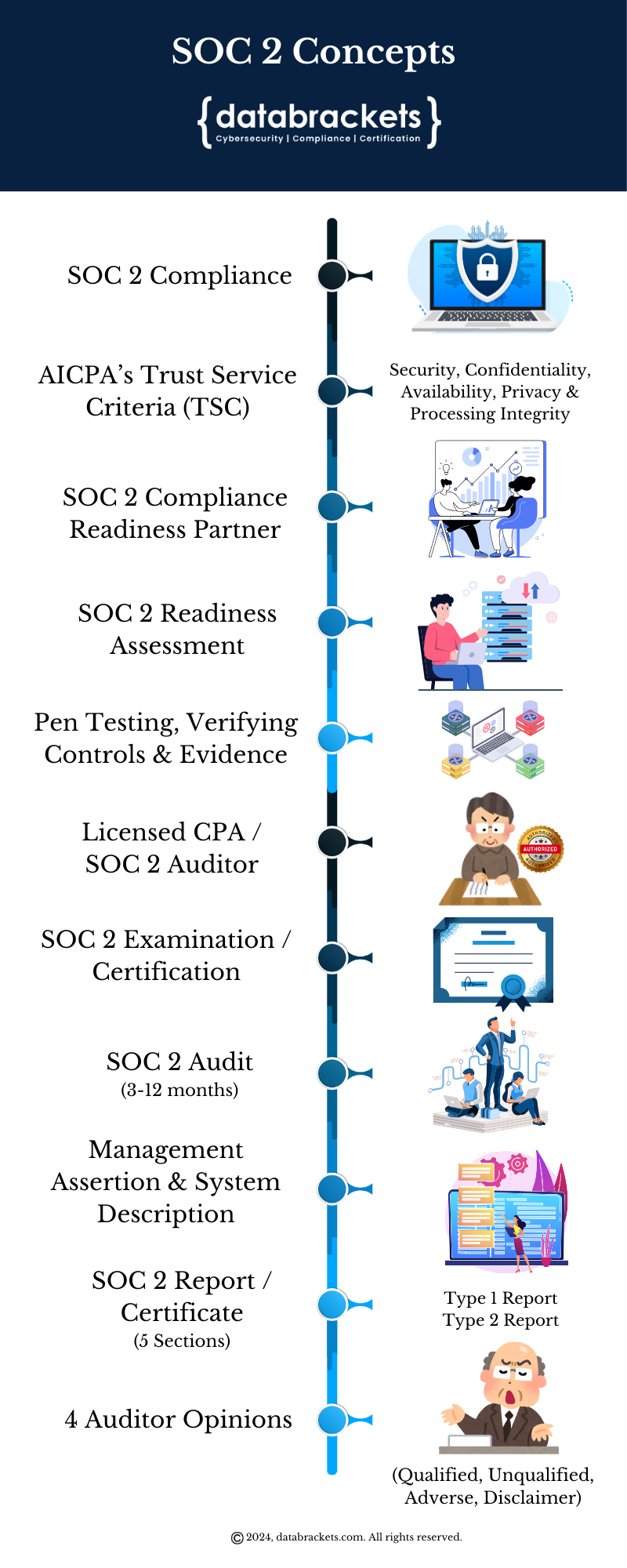
The SOC 2 Process
A SOC 2 Examination consists of a SOC 2 Audit conducted by an authorized CPA licensed to practice by the AICPA. Once the audit is completed, the SOC 2 Auditor issues a SOC 2 Report, which may be a Type 1 Report or Type 2 Report, as per your request. As part of the SOC 2 Audit process, the authorized CPA or SOC 2 Auditor tests the controls under AICPA’s Trust Service Criteria to prove the appropriateness of their design (Type 1 Report) and their operational effectiveness (Type 2 Report).
While organizations can choose which Trust Service Criteria they implement and include in the scope of the audit, they cannot choose which controls are evaluated under those criteria. Quite often, we see SaaS providers choose to get certified in Security, Availability, and Processing Integrity. The other two criteria, Confidentiality and Privacy, tend to be more common among healthcare entities. Their systems and processes are thoroughly audited during the audit period, and the resulting SOC 2 Report outlines the Auditor’s Opinion along with a detailed description of efficiencies and deficiencies.
Organizations typically identify the controls they need in their vendor’s control architecture before they share their data, and a SOC 2 Report helps them evaluate the vendors who meet their requirements. Even though CPAs can use different formats for their SOC 2 Report, these are generally five sections. This creates a standardized way to evaluate vendors and partners based on the efficacy of their controls before making decisions about partnerships. Since SaaS Providers have a lot to lose if they do not succeed at implementing and demonstrating the security of their systems, it is generally recommended that they partner with a SOC 2 Compliance Readiness Partner to prepare for their SOC 2 Examination.
Are SOC 2 Compliance and SOC 2 Certification different?

SOC 2 compliance and SOC 2 certification are related but distinct concepts. SOC 2 compliance refers to adhering to the criteria outlined in the Service Organization Control 2 (SOC 2) framework. The SOC 2 Framework consists of five Trust Services Criteria by the AICPA: security, availability, processing integrity, confidentiality, and privacy of customer data. Achieving SOC 2 compliance involves implementing and maintaining these controls in accordance with the standards outlined by the American Institute of Certified Public Accountants (AICPA).
SOC 2 Examination (often called SOC 2 Certification) is the formal recognition by an independent auditor that an organization’s systems and processes meet the requirements of the SOC 2 framework. It signifies that an organization has undergone a thorough audit conducted by a qualified third-party auditor, who has assessed the effectiveness of the controls in place and verified compliance with SOC 2 standards. While SOC 2 compliance is about meeting the necessary criteria, SOC 2 certification involves obtaining official validation of that compliance through an external audit process.
While SaaS Providers implement a wide variety of security measures in the normal course of setting up their systems and processes and may be confident of their level of security, it is inadvisable to undergo a SOC 2 Audit without a Readiness Assessment. The SOC 2 audit period ranges from 3 to 12 months, and SaaS providers risk losing time and revenue from potential contracts if the evidence to prove their security controls are not adequate or the control is not functional for any reason.
The role of a SOC 2 Compliance Readiness Partner is extensive in preparing their clients to successfully meet SOC 2 standards for their industry. SaaS Providers can benefit from a thorough Gap Analysis, Control Mapping, Documentation Review, Remediation Planning, Implementation Support, Internal Audit, Readiness Assessment, Pen Testing, and Support to draft the Management Assertion and describe their systems for their SOC 2 Report.
7 Benefits of SOC 2 Certification for SaaS Providers

SOC 2 compliance is increasingly recognized as a crucial standard for Software as a Service (SaaS) providers, as proof of their commitment to security, and privacy of customer data. This compliance is especially vital in a digital landscape where data breaches are common. SOC 2 Certification provides a competitive edge to SaaS providers by showcasing their dedication to data security and operational excellence. In turn, this compliance helps in attracting and retaining discerning customers who prioritize data security in their service providers.
Credibility in a highly competitive marketplace: SOC 2 Certification provides instant credibility for SaaS providers by demonstrating their commitment to data security and operational excellence. This reassurance can attract more clients and build trust in a highly competitive marketplace.
Business Growth: Obtaining a SOC 2 Certification demonstrates your capability to securely manage customer data, which can help you secure more deals and attract additional clients.
Organize people, processes, and technology based on security best practices: SOC 2 Certification helps SaaS providers streamline their operations by aligning people, processes, and technology with industry-leading security standards. This structured approach not only enhances efficiency but also mitigates risks, fostering a robust and secure service environment.
Respond to Multiple Vendor Security Questionnaires: SOC 2 Certification minimizes the need for repetitive vendor assessment questionnaires by providing a standardized proof of security compliance. This efficiency saves time and resources for SaaS providers, allowing them to focus more on core business activities and less on administrative tasks.
Assure Customers: SOC 2 Certification offers customers fundamental assurance that their data is protected, demonstrating a SaaS provider’s dedication to stringent security measures. This trust-building factor can enhance customer loyalty and confidence in your capabilities.
Vendor Management: With SOC 2, you can establish benchmarks for vendors and ensure they adhere to the highest standards of information security.
Risk Management: You can develop and oversee risk management processes and internal corporate governance following the SOC 2 framework.
Why Businesses prefer SaaS Providers
with a SOC 2 Type 2 Certification

Businesses rely on a SOC 2 Report when selecting a SaaS vendor to partner with. Some of the primary reasons for this choice are:
- Trust and Credibility: SOC 2 compliance demonstrates that a SaaS provider has robust controls to ensure customer data security, availability, processing integrity, confidentiality, and privacy. This enhances trust and credibility among current and potential clients, as they can be assured that their data will be handled responsibly.
Independent Verification: SOC 2 certification involves an independent audit conducted by a third-party auditor. Businesses trust this independent verification because it provides assurance that the SaaS provider’s security controls are effective and in line with industry standards.
Risk Mitigation: By selecting a SaaS provider with SOC 2 certification, businesses can mitigate the risk of data breaches, reputational damage, compliance violations, and other security incidents. SOC 2 compliance demonstrates that the provider has implemented adequate controls to protect sensitive data and maintain the integrity of their systems. Additionally, by adhering to SOC 2 standards, SaaS providers can identify and address security vulnerabilities and operational weaknesses, thereby reducing the likelihood of costly incidents.
Regulatory Compliance: SOC 2 compliance demonstrates that a SaaS provider has robust controls to ensure customer data security, availability, processing integrity, confidentiality, and privacy. This enhances trust and credibility among current and potential clients, as they can be assured that their data will be handled responsibly.
Contractual Obligations: Businesses often have contractual obligations to protect the confidentiality and security of their customers’ data that go beyond regulatory compliance. By requiring SOC 2 certification as part of their RFQ, businesses reduce the time required to select vendors who meet these contractual obligations and reduce the risk of legal and financial liabilities.
Customer Expectations: In today’s digital landscape, customers expect businesses to prioritize the security and privacy of their data. SOC 2 certification serves as tangible proof that a SaaS provider takes these concerns seriously and has invested in robust security measures.
Competitive Advantage: Businesses that demonstrate SOC 2 compliance may have a competitive advantage over competitors lacking certification. SOC 2 certification signals to potential customers that a SaaS provider is committed to maintaining high standards of security and compliance, which can help attract new business and retain existing customers.
Impact on Revenue: While SOC 2 compliance itself may not directly generate revenue, it can indirectly impact revenue by opening doors to larger contracts with enterprise clients who require such compliance as a prerequisite. Additionally, being SOC 2 compliant can help reduce churn by reassuring existing customers about the security of their data, thus preserving revenue streams.
Scalability and Growth: SOC 2 compliance frameworks encourage SaaS providers to establish scalable processes and controls. This not only facilitates compliance but also lays a foundation for sustainable growth as the provider onboards more clients and handles increasing volumes of data.
Standardized Comparison of Vendors: SOC 2 Reports standardize the vendor selection process by providing a consistent framework for evaluating vendors’ security controls and practices. This allows for a more objective comparison between vendors, enabling businesses to assess their security posture effectively and make informed decisions about which vendors best meet their security requirements. Organizations with a SOC 2 Report can also save considerable time and resources by sharing it with existing clients instead of a Vendor Security Questionnaire.
Businesses trust SOC 2 certification because it provides independent verification of a SaaS provider’s security controls, helps them compare different vendors using a standardized list of controls and criteria, enhances trust, credibility, and competitiveness, helps mitigate risks, meets customer expectations and compliance obligations, support sustainable growth and confer a competitive advantage in the marketplace. As a result, they often include SOC 2 certification as a requirement in their RFQs to ensure they are selecting vendors that meet their security and compliance standards. While achieving SOC 2 compliance may require upfront investment in time and resources, the long-term benefits outweigh the costs for most SaaS providers.
Key takeaways
SOC 2 provides SaaS providers with a structured way to demonstrate trustworthiness by independently validating how security and related controls are designed and operated within their service environment.
The framework is especially relevant for SaaS companies because customers often rely on shared infrastructure and outsourced services, making transparency into control effectiveness essential for building confidence.
SOC 2 is not a certification but an attestation, meaning the value lies in how accurately the report reflects real operational practices rather than the mere existence of policies or tools.
Choosing the appropriate trust services criteria allows SaaS providers to focus the assessment on risks that are most relevant to their service model and customer expectations.
Type I and Type II reports serve different purposes, with one validating control design at a moment in time and the other demonstrating consistent operation over an extended period.
Preparation for SOC 2 requires aligning internal processes, documentation, and daily operations so that controls function consistently and can withstand auditor scrutiny.
Evidence collection and process consistency are critical, as auditors evaluate not just intent but whether controls are applied reliably throughout the assessment period.
SOC 2 readiness often exposes operational gaps, providing SaaS providers with an opportunity to mature security and reliability practices beyond minimum requirements.
For SaaS organizations, a well-executed SOC 2 report supports sales, vendor due diligence, and customer trust by offering credible, third-party assurance of control effectiveness.
databrackets as your SOC 2 Compliance Readiness Partner
Typically, organizations tend to directly look for a licensed CPA firm and sign up for a SOC 2 Audit. There are several stumbling blocks in this approach and it can lead to superfluous payments that can be avoided. When you approach a licensed CPA, you will not receive guidance on which type of report you need (SOC 1, SOC 2 or SOC 3) or the Trust Services Criteria and security controls for your industry. They are not required to help clients with guidance to implement or prove their SOC 2 Compliance. Their mandate is to conduct an impartial audit and issue a structured report to help your clients understand if your systems are secure.
Working with SOC 2 Compliance Readiness Partner can help you save a significant amount of time, money and resources. Our security experts have extensive experience working with clients across industries with the sole purpose of helping to position your organization for a successful audit. The tasks that we undertake, as your SOC 2 Compliance Readiness Partner include:
- Initial Consultation and Scoping
- Educating the Client
- Gap Analysis
- Control Mapping
- Documentation Review and Development
- Remediation Planning
- Implementation Support
- Internal Audit
- Readiness Assessment Report
- Ongoing Support and Monitoring
The data of our SOC 2 Readiness clients is maintained in a structured format on our GRC platform – dbACE and is accessible to the CPA that you chose to work with. You can refer to the controls, Trust Services Criteria and the 2 sections of your SOC 2 Report which you need to submit – the Management’ Assertion and a Description of your System, using your unique login. We also collaborate with certified CPA firms whom you can choose to work with, if you decide to do so. Hence, working with a Readiness Partner helps you to not only prepare for SOC 2 Certification but also ensures that your security controls are implemented adequately and you have evidence to prove their effectiveness.
Overview of databrackets
Our team of security experts has supported organizations across a wide variety of industries to align their processes with security frameworks like HIPAA, 21 CFR Part 11, ISO 27001:2022, SOC 2, NIST SP 800-53, NIST Cybersecurity Framework, NIST SP 800-171, GDPR, CMMC etc.
We are constantly expanding our library of assessments and services to serve organizations across industries. Schedule a Consultation if you would like to Connect with an Expert to understand how we can customize our services to meet your specific requirements.
Summary
To summarize,
SOC 2 is a widely used assurance framework that helps SaaS providers demonstrate how they protect customer data and operate reliable services through independently evaluated controls.
The framework is particularly relevant for SaaS environments because customers rely on shared platforms and outsourced infrastructure, making visibility into control effectiveness a critical trust factor.
SOC 2 reports are attestations rather than certifications, meaning their value depends on how accurately they reflect real-world operations instead of the presence of formal policies alone.
SaaS providers must determine which trust services criteria apply to their services, ensuring the assessment focuses on risks that align with how customers use and depend on the platform.
The distinction between Type I and Type II reports affects how assurance is interpreted, as one evaluates control design at a point in time while the other demonstrates consistent performance over a defined period.
Preparing for SOC 2 requires aligning documentation, processes, and daily operations so controls operate as described and withstand auditor review.
Evidence collection and consistency over time are central to a successful assessment, as auditors evaluate whether controls are applied reliably rather than sporadically.
SOC 2 readiness often reveals operational weaknesses, creating an opportunity for SaaS providers to strengthen internal practices and improve service reliability.
For SaaS organizations, SOC 2 functions as a trust-building mechanism that supports customer confidence, vendor due diligence, and long-term growth.