SOC 2 Readiness & Examination
SOC 2 is the most popular independent third-party security assessment report requested by prospects customers, partners, cyber insurance companies etc
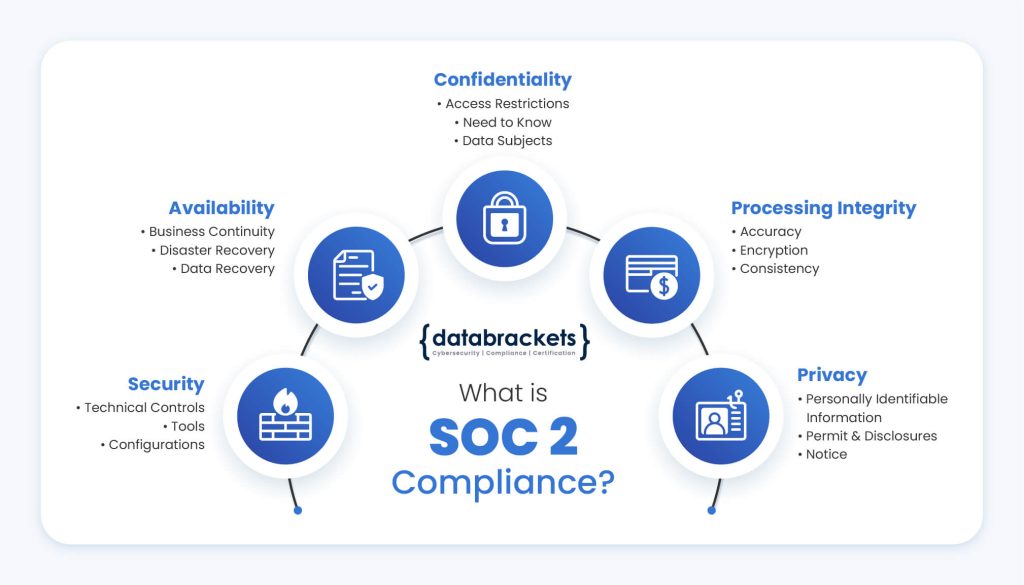
What is SOC 2

Service Organization Control 2 (SOC 2) is a widely recognized auditing standard developed by the American Institute of Certified Public Accountants (AICPA). Organizations seeking to demonstrate their commitment to data security and operational excellence often pursue SOC 2 compliance to build trust with customers, partners, and regulators.
A SOC 2 Examination is designed to assess the controls and security practices of service organizations that store, process, or transmit sensitive customer data. A SOC 2 Report is often used by organizations that provide services to other businesses, such as data centers, technology companies, cloud providers, and SaaS companies. This report is critical in assuring clients and stakeholders that a service organization has adequate controls in place to protect sensitive information and ensure the reliability of their services.
Monitoring and assessment of SOC 2 compliance are typically conducted by independent third-party audit firms, known as CPA firms. These auditors evaluate the organization’s controls and practices against the Trust Services Criteria (TSC), which includes security, availability, processing integrity, confidentiality, and privacy.
Important Resources to learn about SOC 2 Compliance:
Trust Services Criteria by AICPA
During your SOC 2 Audit, your CPA will assess if you are complying with the Trust Services Criteria that you have selected. AICPA’s ‘Trust Services Criteria’ or the ‘SOC 2 Framework’ consists of security, availability, processing integrity, confidentiality and privacy of customer data. Read more
SOC 2 Readiness Process (Preparing for your SOC 2 Audit)
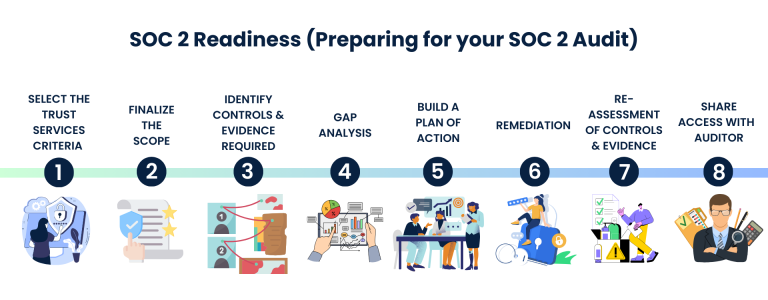
Our SOC 2 Readiness consulting services are tailored to assist SaaS and Service organizations in navigating the complex terrain of SOC 2 audits. We understand the critical importance of compliance, and our comprehensive approach ensures that you are well-prepared every step of the way. Our expert consultants will work closely with you through out the SOC 2 Readiness process:
1. Determine the Trust Services Criteria (TSC) relevant to your specific industry
2. Finalize the scope of your SOC 2 Audit
3. Identify the applicable controls under each TSC while providing guidance on accepted evidence documentation
4. Gap Analysis by our experts, based on the scope of your audit
5. Develop a Plan of Action as per the identified gaps
6. Guide your team as they work through the Remediation process
7. Re-Assessment of Your Controls and Evidence Documentation to ensure you are ready for your SOC 2 Audit. We will also continue to monitor your controls.
8. Share access to evidence documents with your Auditor to ensure you do not have to duplicate your efforts during your SOC 2 Audit
Deliverables for SOC 2 Readiness
The deliverables for our SOC 2 Readiness encompass a comprehensive suite of tools and documentation aimed at fortifying your security posture and ensuring compliance with stringent standards. Our deliverables include:
1. Gap Analysis Reportto offer a meticulous overview of current security protocols and identify areas that require enhancement
2. Pen Testing Reportsto provide an in-depth assessment of vulnerabilities
3. A collection of compliance and security assessment reports to ensure a comprehensive evaluation
4.Guidance on acceptable evidence documentswill be supplied to streamline the compliance process
5. Updated Policies and Procedures to address policy and procedural requirements
6. Security Tech Consulting will facilitate the implementation of any missing technical controls
7. Customized User Training< will empower staff with the knowledge needed to maintain security standards
8. Support for the completion of the Management Assertion for the SOC 2 Report
9.Final Readiness Reportthat outlines the organization’s preparedness for SOC 2 Type 2 certification
These deliverables collectively provide a robust foundation for your SOC 2 Examination and to prove you have a secure and compliant operational environment.
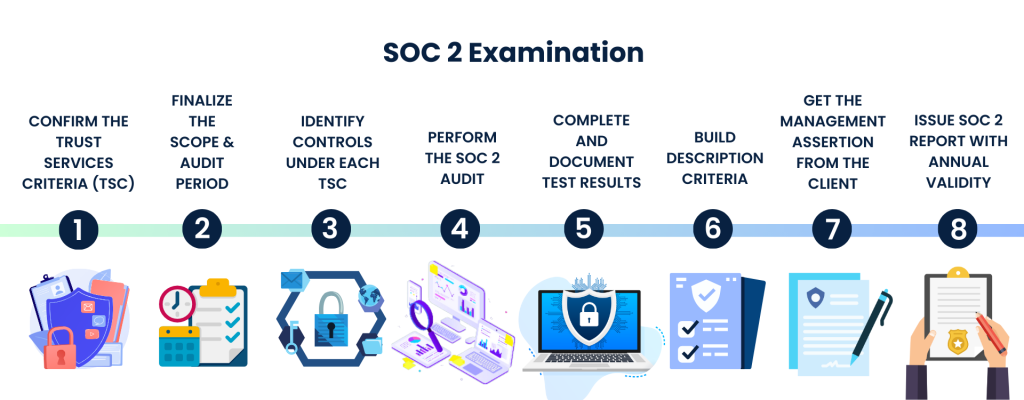
SOC 2 Examination Process
The SOC 2 Examination process is a comprehensive and structured assessment designed to evaluate an organization’s adherence to the Trust Services Criteria (TSC). Once the SOC 2 Report is issued, there are no recommendations to bridge the gaps. While the SOC 2 Report is the auditor’s opinion of how well an organization is complying with the chosen Trust Services Criteria, there are protocols about the kind of evidence documents and third-party independent pen testing reports that are accepted. Steps in the SOC 2 Examination Process include:
1. Confirming the Trust Services Criteria relevant to the organization’s operations, which sets the framework for the examination
2. Finalizing the Scope of the SOC 2 Examination and the SOC 2 Audit Period
3. The Applicable Controls under each TSC are Identified by the CPA to ensure that all relevant aspects of the criteria are addressed
4. Performing the SOC 2 Audit
i) Selecting samples where applicable
ii) Examination, Testing and Verification of Controls
The SOC 2 audit then proceeds with a meticulous approach. This includes selecting samples, where applicable, to assess the effectiveness of controls. The CPA then conducts a thorough examination, testing, and verification of these controls, scrutinizing processes, systems, and documentation to ensure compliance
5. Comprehensive test results are documented, including any deviations or issues identified during the examination process.
6. Description criteria : To provide context for the assessment, a detailed description of the organization’s systems and controls is built, outlining their design and implementation.
7. Management Assertion from the client: The examination process also involves obtaining a Management Assertion from the client, where management attests to the accuracy and completeness of the controls and processes being examined.
8. Issue SOC 2 Report with annual validity: Finally, upon successful completion of the examination, a SOC 2 report is issued with an annual validity. This report summarizes the findings, confirms compliance with the Trust Services Criteria, and provides valuable information to stakeholders, helping them make informed decisions about the organization’s security and privacy controls.
 The cost of a SOC 2 Examination is usually the reason that organizations delay undergoing the assessment. However, the benefits far outweigh the cost when you connect with a team that understands your priorities and is able to deliver cost-effective solutions.
The cost of a SOC 2 Examination is usually the reason that organizations delay undergoing the assessment. However, the benefits far outweigh the cost when you connect with a team that understands your priorities and is able to deliver cost-effective solutions.




























